HashiCorp is pleased to announce the general availability of Vault 1.15. HashiCorp Vault provides secrets management, data encryption, identity management, and other workflow capabilities for applications on any infrastructure.
Vault 1.15 focuses on Vault’s core secrets workflows as well as team workflows, integrations, and visibility. Key additions in this release include:
- Certificate Issuance External Policy Service (CIEPS) [Enterprise]
- UI enhancements
- Azure SDK Workload Identity Federation (WIF) support
- Vault Secrets Operator (VSO) enhancements
- Vault Enterprise seal high availability (beta)
- Vault Enterprise secrets sync (beta)
- Event monitoring (beta)
Let’s take a closer look.
»Certificate Issuance External Policy Service (CIEPS)
There are an enormous number of possible fields and extensions on PKI X.509 certificates. The Vault PKI secrets engine supports the most commonly used subset of these to cover a majority of use cases. However, we do get requests from customers who want to add custom data to their certificates for a wide variety of reasons.
With the release of CIEPS, we’re enabling fine-grained control over issued certificates using custom policies in a customer-defined service outside of Vault. Using CIEPS, customers implement a custom service that can be called by the Vault PKI secrets engine to evaluate and override original certificate-request content. With this capability, customers can ensure Vault PKI-issued certificates meet corporate compliance standards.
CIEPS requires a Vault Enterprise license.
»UI enhancements
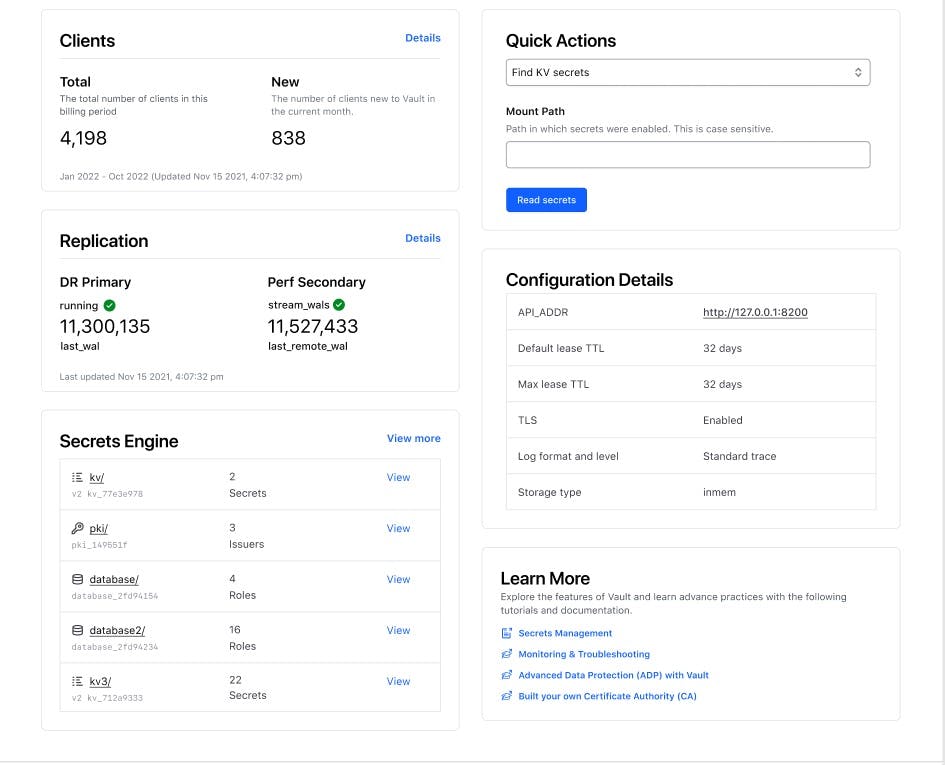
New landing page dashboard: Based on insightful feedback from our customers, we continue to enhance Vault's graphical user interface to better meet their needs. Vault 1.15 introduces a landing page dashboard that provides a more comprehensive and unified overview of important information about a Vault instance. From this new view, customers can quickly see key information like client counts and config details or take quick actions. The new layout also includes links to documentation and other relevant training materials.
New LDAP UI: The unified LDAP secrets engine was implemented as part of Vault 1.13 in June 2023 and afterwards we wanted to follow up with UI enhancements that would make it easier to manage LDAP roles, shared library accounts/credentials, and automatic password rotations through a single interface.
Vault 1.15 has completed this UI work and users can now accomplish the following tasks through the Vault UI:
- Enable the LDAP secrets engine
- Connect to existing OpenLDAP, Active Directory (AD), or Resource Access Control Facility (RACF) systems
- Manage roles and libraries.
KV v1 secrets engine enhancements: Users now have a more functional UI where they can see more details and perform actions. They can:
- See secrets they have read access to under their directory
- Show a “diff” between a previous and new secret version
- Copy and paste a secret path from the UI to the CLI or API
KV v2 secrets engine control groups: Users can now take actions on control groups in the UI when permitted by policy.
Example policies: Users can now see example policies in the Policies UI space to help them configure their policies.
»Azure Workload Identity Federation (WIF) SDK support
This feature is for customers using Microsoft Azure Kubernetes Service (AKS) who also want to use the new Workload Identity authentication method. Microsoft is in the process of deprecating Azure’s pod-managed identity authentication method in favor of a new Workload Identity authentication method. In version 1.15, the Vault Agent supports both, per our partnership with Microsoft.
Customers using AKS can take advantage of the most up-to-date authentication methods and workflows from Microsoft. They won’t have to update any code as the feature is backwards compatible. Updating to Workload Identity Federation (WIF), however, will require changes to customers’ containers.
»Vault Secrets Operator (VSO) enhancements
The Vault Secrets Operator for Kubernetes was released in Vault 1.14 in June and connects Vault secrets directly into native Kubernetes secrets, freeing application developers to focus on application code as they return control over secrets to security and operations teams.
Key updates to VSO in Vault 1.15 include:
- Red Hat OpenShift certification, which unlocks use for customers in regulated industries such as financial services
Note: VSO updates will be released asynchronously to Vault 1.15, as a separate product binary.
»Vault Enterprise seal high availability (beta)
Prior to this release, Vault Enterprise customers could use a single KMS provider to store the Vault seal key (AWS KMS, HSMs, etc.). This creates a challenge for the customer if the seal key is unavailable from the KMS provider for some reason, such as deletion, compromise, or disaster. In that case, Vault can’t be unsealed, which could cause a production outage. This new feature enables enterprise customers to use independent seals retained in multiple KMS providers, ensuring continuity of business operations.
»Vault Enterprise secrets sync (beta)
Secrets syncing is now available in Vault Enterprise as a beta feature. Some managed services require users to fetch secrets from the native cloud service provider secrets manager, and other cloud service provider services are tightly integrated with the native secrets managers and support only AWS, Azure, Google Cloud, and GitHub. In certain circumstances, however, fetching a secret directly from Vault in a cloud environment is either impossible or impractical. This beta currently supports the KV v2 secrets engine.
This new Vault Enterprise capability supports one-way synchronization of KV v2 secrets with five external types of destinations:
- AWS Secrets Manager
- Azure Key Vault
- Google Cloud Secret Manager
- GitHub Action secrets
- Vercel Project Environment Variables
Using this capability, Vault remains the system of record for these secrets, caching them as read-only values in the external system. Users can then read the secrets from the external secret manager.
»Event monitoring (beta)
This event monitoring beta feature builds on the Vault 1.13 alpha release to add full policy support, namespaces, and an API. Applications and external integrations that rely on Vault for secrets management need to be alerted when a secret in Vault is updated. Historically, there was no mechanism in Vault to notify downstream applications of changes to secrets in Vault.
This feature allows subscribers to register to be notified of changes to their KV secrets. Subscribers can be a destination such as the Vault Agent (to allow for static secret caching) or other queues such as Kafka, AWS SQS, other Vault subsystems such as plugins, or another Vault instance. We plan to add support for more secrets engines in the future.
»Upgrade details
This release also includes more new features, workflow enhancements, general improvements, and bug fixes. All of these updates can be found in the Vault 1.15 changelog. Please visit the Vault release highlights page for step-by-step tutorials demonstrating the new features.
As always, we recommend upgrading and testing new releases in an isolated environment. If you experience any issues, please report them on the Vault GitHub issue tracker or post to the Vault discussion forum. As a reminder, if you believe you have found a security issue in Vault, please responsibly disclose it by emailing security@hashicorp.com — do not use the public issue tracker. For more information, please consult our security policy and our PGP key.
For more information about Vault Enterprise, visit the HashiCorp Vault product page.








