HCP Vault Radar is HashiCorp’s new secret scanning product that expands upon Vault’s secret-lifecycle management use cases to include the discovery and prioritization of unmanaged secrets. In January, we announced a limited beta program for HCP Vault Radar. Today, we’re announcing that HCP Vault Radar is entering limited availability. The limited availability phase signals that HCP Vault Radar is prepared for production workloads while the product continues to onboard additional data sources.
»Reduce the risk of secret sprawl
While IT organizations aim to securely store and manage every secret, developers often hard-code secrets into repositories, share secrets on messaging platforms, and include secrets in wikis or tickets. Sometimes, machines leak plaintext secrets in log data when errors occur. These unmanaged secrets pose a threat to organizations’ security posture if compromised.
HCP Vault Radar helps DevOps and security teams reduce the risk associated with secret sprawl by detecting unmanaged and leaked secrets, as well as those that have been hard coded or reside in plaintext, so they can take appropriate actions to remediate these secrets. HCP Vault Radar scans for secrets like usernames and passwords, API keys, and tokens in popular developer tools and repositories.
HashiCorp co-founder and CTO Armon Dadgar
»Prioritize remediation effectively
Secret scanning is helpful only if it detects signals from noise. As a result, secret scanning tools should help you determine if exposed secrets are low-risk or significant threats. That’s why HCP Vault Radar has invested heavily in reducing false positives and helping users effectively prioritize remediation efforts.
To rank the severity of an exposed secret, HCP Vault Radar uses a combination of data points to answer the following questions:
- Was the secret found on the latest version of the code or document?
- Does content have high entropy or randomness that likely indicates it's a secret?
- Is the secret currently active and in use?
- Is this secret currently live in Vault?
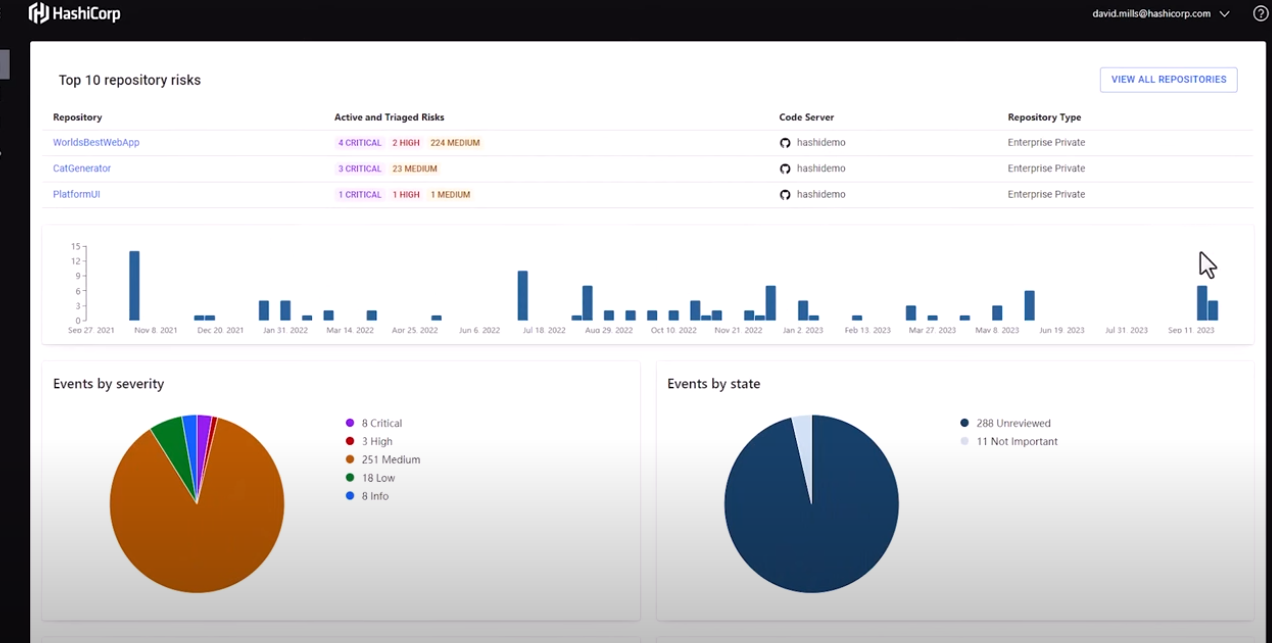
Secrets scan overview results
»Version history
Knowing whether the secret was discovered in the latest version of a file is important for remediation prioritization, as well as governance. If the potential secret was discovered in a current file, HCP Vault Radar assigns a higher priority because it is likely that this finding has not been previously evaluated and is therefore more likely to be a secret.
Governance and compliance teams are also interested in secrets that are discovered in historical versions of a file. They need to understand when the secret was published and why it wasn’t remediated. Depending on their findings they may need to adjust their workflows or determine if ignore rules need to be introduced or adjusted.
»String randomness
Another way HCP Vault Radar reduces false positives is by evaluating the entropy (randomness) of content. Relying on pattern-matching text searches alone increases the risk of missing secrets that don’t adhere to a particular format. Entropy algorithms are highly effective at identifying random or complex strings that frequently indicate the content is a secret. Evaluating string literals in code for entropy allows HCP Vault Radar to identify potentially suspicious strings in any format. HCP Vault Radar employs security scanning best practices by combining pattern matching with entropy to prevent secrets from making it to production.
»Activeness checks
Credentials currently in use present a bigger threat than those that were created for test purposes and never worked or aren’t active. When HCP Vault Radar finds a credential, it will call out to the associated application to check if the secret is still active. Active credentials are marked as high risk within the prioritization portal. Today, HCP Vault Radar can test for:
- Google Cloud API keys
- Amazon Web Services (AWS) credentials
- Personal access tokens for GitHub
- JSON web tokens (JWT)
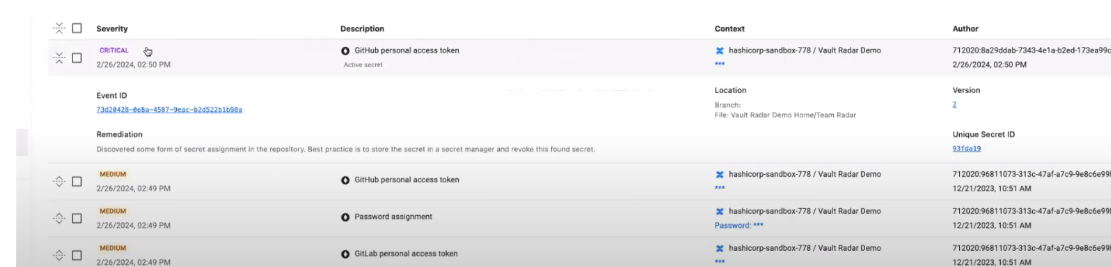
Metadata associated with an unmanaged secret in HCP Vault Radar
»Vault correlation
To further support prioritization, HCP Vault Radar can correlate if a leaked secret is stored in Vault. Most credentials in Vault are used in critical production environments, so HCP Vault Radar will give exposed secrets a higher severity score when also found in Vault’s key value stores.
»Scan top developer tools in the cloud or on-premises
HCP Vault Radar supports secret scanning from the SaaS HashiCorp Cloud Platform as well as an agent-based variant that allows for on-premises and self-managed scanning. Results from all sources are integrated into the HCP dashboard for a streamlined user experience when prioritizing remediation of unmanaged secrets. HCP Vault Radar also includes a CLI for point-in-time on-demand use cases. It is best leveraged for non-continuous or non-rule-based scans of a particular file or folder’s contents. Once the CLI scan is completed, the results are uploaded to the HCP portal to take advantage of Vault Radar’s prioritization and remediation workflow functionality.
HCP Vault Radar customers can scan the following data sources (HCP Terraform, Terraform Enterprise, and Slack are newly available):
- Git-based version control systems (GitHub, GitLab, Bitbucket, etc.)
- AWS Parameter Store
- Server file directory structures
- Confluence
- HashiCorp Vault
- Amazon S3
- HCP Terraform
- Terraform Enterprise
- JIRA
- Docker images
- Slack
»Remediate unmanaged secrets
In addition to secret scanning, HCP Vault Radar supports a robust set of remediation workflows via ticketing and alerting solutions. HCP Vault Radar includes integrations with the following alerting and ticketing solutions for further security incident response:
These integrations leverage common tools in DevOps, platform engineering, and security teams’ workflows supporting incident response processes. HCP Vault Radar transmits all of the information necessary to remediate its findings, including:
- Author
- Location
- Activeness
- If the secret is in the current version of a document or history
- Whether the secret is in plaintext
The secret is never exposed in the HCP console. Instead, the user is provided a link to the location where the secret can be found, investigated, and remediated when necessary.
»Prevent secret leakage
In addition to integrating with alerting and ticketing tools to remediate findings that have already been published, HCP Vault Radar integrates with GitHub to prevent possible secrets from being merged into the main branch in the first place. The GitHub app will alert you to any sensitive data found in the pull request, including both the tip of the pull request and the history of any commits. The alert includes details on what type of secret was found and where it was found.
Pull request checks allow HCP Vault Radar to perform a scan against a GitHub pull request when the HCP Vault Radar GitHub application is installed for a repository. The HCP Vault Radar application for GitHub will run for every pull request and for every new commit to any open pull requests.
By default, the HCP Vault Radar GitHub application does not block any pull requests. Our usage statistics show more than 80% of warnings about secrets in pull requests are fixed prior to merging into the main branch, so a non-blocking workflow tends to be a better fit for developer needs. However, organizations can configure GitHub to block the pull request from being merged if the check fails due to sensitive data being discovered.
»Learn more about HCP Vault Radar
HCP Vault Radar is an exciting new addition to HashiCorp Vault’s secret lifecycle management capabilities that helps enterprises reduce risk associated with credential exposure. Discovery of unmanaged secrets and subsequent remediation workflows further differentiate Vault’s secrets lifecycle management offering by enabling organizations to take a proactive approach to remediation before a data breach occurs.
To learn more, check out these resources:
- HCP Vault Radar product documentation
- Solutions to secret sprawl blog post
- Contact HashiCorp sales
- Demo








