Unlike traditional credentials that are used by an individual to gain access to a particular system, secrets are leveraged by developers and their code to access applications, services, infrastructure, and by platforms to establish trusted identities. They can include usernames and passwords, API tokens, TLS certificates, keys, and more. However, as organizations distribute their workloads across more platforms they can lose centralized control and end up with secret sprawl.
This post offers a four part framework that offers solutions to modern secrets management challenges.
»A 4-part framework for secret control
Getting secret sprawl under control requires a comprehensive approach across four dimensions:
- Centralized secrets management platform - A single source of truth for all secrets
- Cross-platform synchronization - Unified management that breaks down harmful silos
- Secret scanning - Detection for leaked secrets, and visibility into where secrets exist across your infrastructure — managed and unmanaged.
- Access controls and encryption - Restrict who can access what, and protect secrets at rest
»1. Adopt a centralized secrets management platform
Having an organization’s secrets siloed does more harm than good. Every additional copy of a secret created opens another window for a secret to be leaked and a subsequent attack. A critical starting point in resolving secret sprawl is to adopt a centralized system where you can store, organize, manage, and ultimately protect all your secrets. There’s no way to build solid governance, auditing, and security around organizational access to secrets if you don’t centralize your management through one control plane. Without a centralized control plane, you can’t easily scale security practices, so you’ll be constantly reinventing the security wheel in different corners of your organization. This fragmentation can also bring significant costs, including an increased threat of a significant security breach.
The first step in resolving secret sprawl is to adopt a centralized system to store, organize, manage, and ultimately protect all your secrets. HashiCorp Vault brought secrets management into the mainstream as a tool category and has had the industry’s broadest adoption for years. Vault is an identity-based secrets and encryption management system that provides encryption services gated by authentication and authorization methods to ensure secure, auditable and restricted access to secrets. It is used to secure, store, generate, rotate, and protect secrets and other sensitive data using a UI, CLI, or API.
»2. Centralize secrets with synchronization integrations
Some organizations store secrets in multiple solutions across different cloud service providers (AWS Secrets Manager, Microsoft Azure Key Vault, Google Cloud Secret Manager, GitHub, and others). While this may meet the requirement of bringing all secrets under management, there’s still a degree of secrets sprawl when security and site reliability engineering (SRE) teams must learn and use multiple solutions, each with their own nuances, in order to perform security reviews, implement organization-wide policies, carry out incident response tasks, or perform company audits.
The solution is to have a central, cloud-agnostic secrets management platform that can synchronize secrets produced in multiple cloud-specific secrets managers and also push its own secrets out to those solutions. Vault’s secrets sync feature allows users to synchronize secrets when and where they require them, continually synchronizing secrets from Vault to external secrets managers so they are always up to date.
With secret sync, Vault is able to:
- Offer complete visibility to satisfy your organization’s compliance and governance requirements.
- Easily manage, provision, rotate, and revoke secrets for external secrets managers using Vault’s UI, CLI, or API.
- Provide granular access controls and policies to determine who has access to which secrets across all secrets managers in an organization.
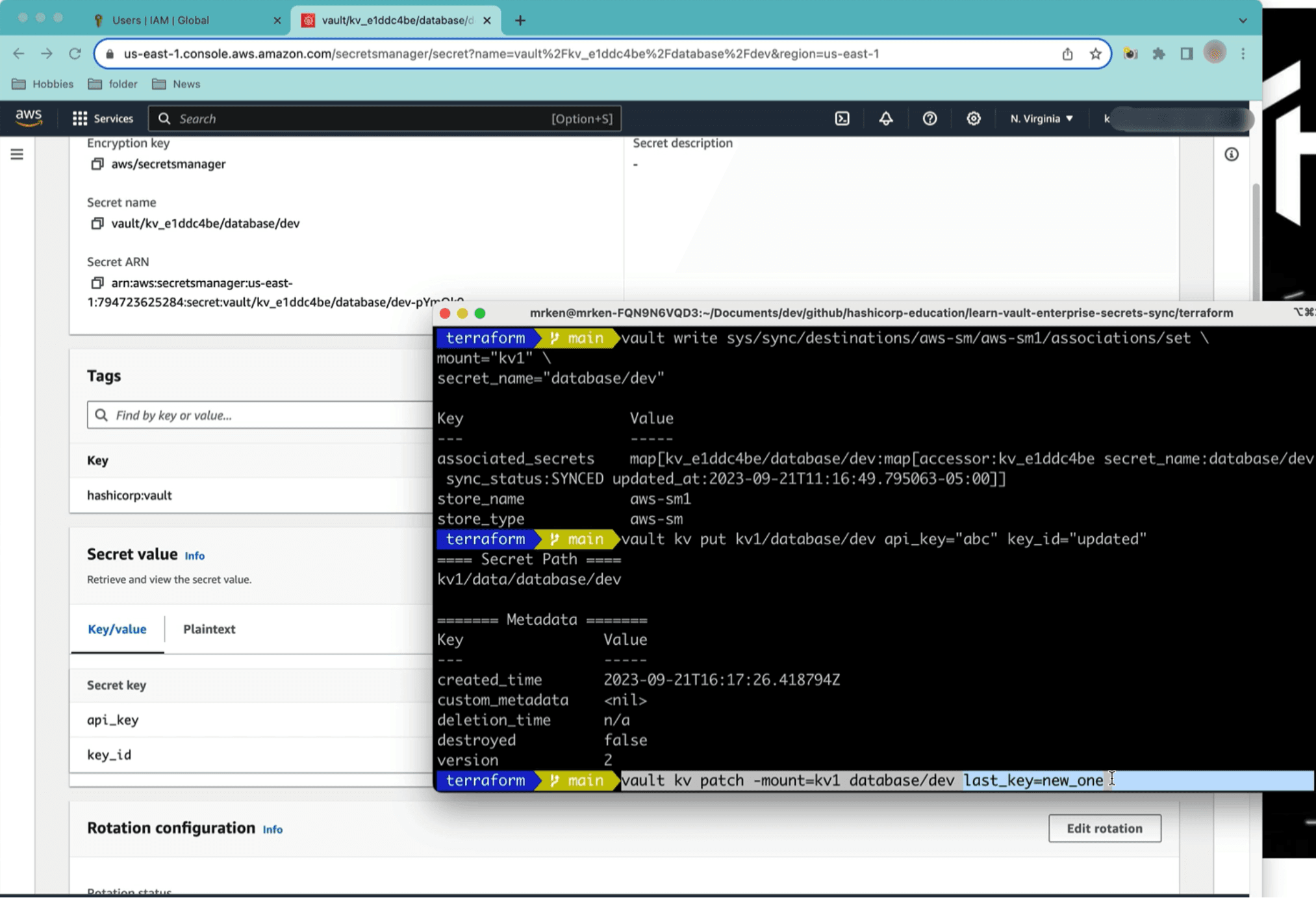
Vault’s CLI integration with AWS Secrets Manager
Vault supports secrets sync with common secrets storage locations, including:
- AWS Secrets Manager
- Microsoft Azure Key Vault
- Google Cloud Secret Manager
- GitHub
- Vercel
Vault has multiple platform and hosting options that allow organizations to take advantage of secrets sync, including HCP Vault and Vault Enterprise. By adopting one of these Vault offerings, organizations can resolve challenges created by secrets management tooling fragmentation and eliminate the need for context switching among multiple secrets management platforms.
»3. Find secrets with scanning
A key piece of any secrets centralization plan is being able to locate API keys, database credentials, security certificates, passwords or publicly identifiable information (PII) across potentially very large IT estates and complex software supply chains. This is where secret scanning tools are required.
HCP Vault Radar automates the initial scanning and ongoing detection and identification of unmanaged secrets so that they can either be revoked or migrated into Vault. HCP Vault Radar uses 300+ scanning algorithms to scan through several data sources, including:
- Git providers
- AWS Parameter Store
- Confluence
- Jira
- Amazon S3
- Terraform
- Local folders
HCP Vault Radar also integrates with Vault Enterprise to scan supported data sources for the presence of leaked secrets currently in Vault that are actively being used. Using additional metadata from the scan, Radar will give the secrets it discovers a risk rating to prioritize which ones may need immediate attention. Together, these features give organizations a more complete view of their secrets, allowing teams to find and manage all secrets and manage risk.
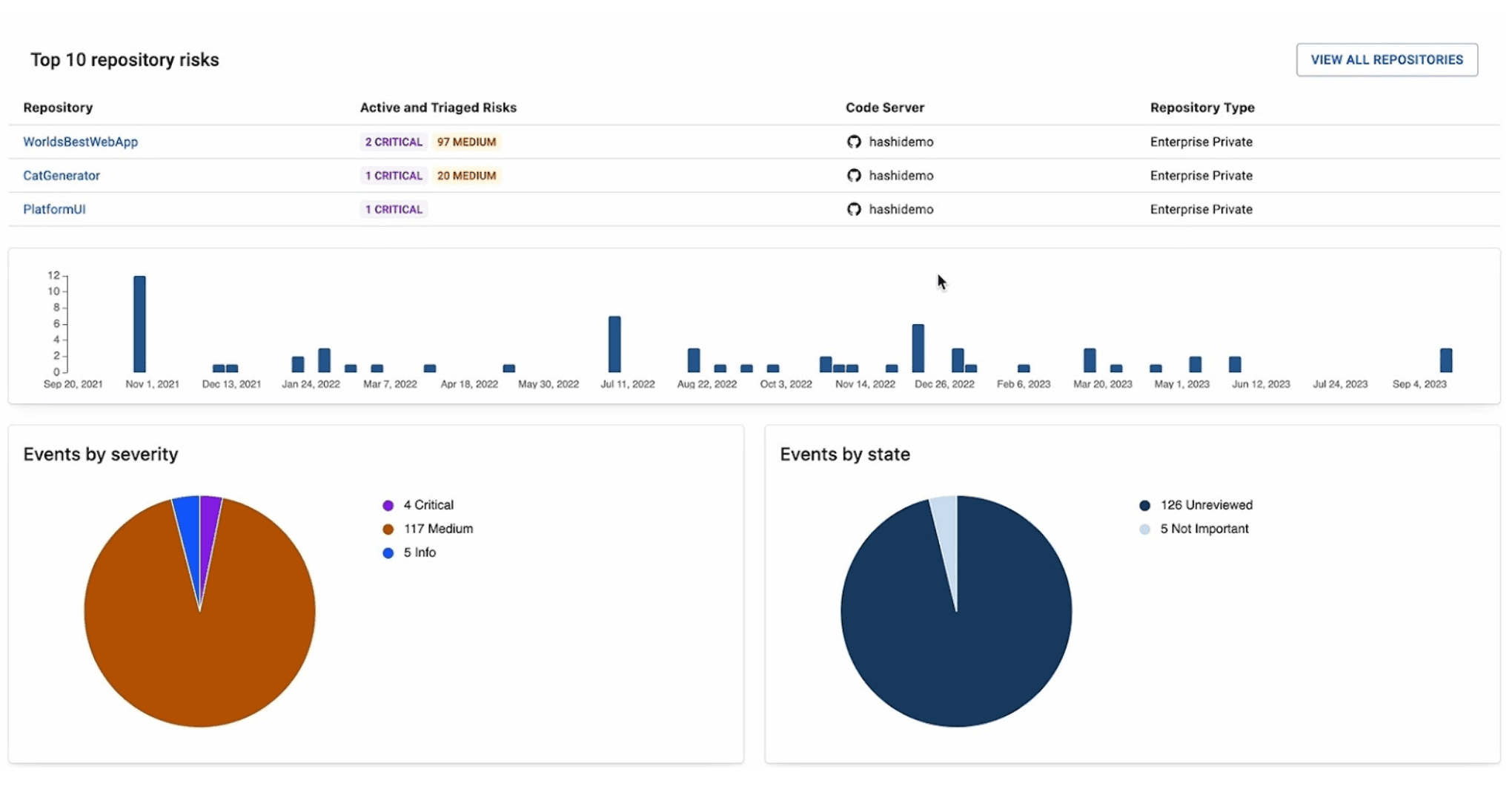
HCP Vault Radar analytics
Watch the video below to learn more about HCP Vault Radar:
»4. Limiting access to secrets
Another important method to mitigate secret sprawl is to limit access to the usable secret. There are two common tactics used to restrict access and usability of secrets to limit sprawl.
»Encryption
An effective secret management platform should provide encryption for its secrets storage. Encryption secures your data in such a way that it’s useless to anyone who doesn’t have the decryption key. Should the encrypted secret be obtained by a threat actor it can’t be used to gain access to systems, APIs, or infrastructure.
Vault provides a security barrier for all requests made to the API & data tier. The security barrier automatically encrypts all data leaving Vault using a 256-bit Advanced Encryption Standard (AES) cipher in the Galois Counter Mode (GCM) with 96-bit nonces. The nonce is randomly generated for every encrypted object. When data is read from the security barrier, the GCM authentication tag is verified during the decryption process to detect any tampering.
»Least privileged access
To maintain the privacy of your sensitive data, you must control access to it with effective controls. Use granular controls to grant secrets access to users, and don’t give a user access to a secret that they don’t need. Temporary access for temporary usage should also be the standard procedure. Ensure that your organization strictly limits unrestricted access or root users. Even when you are working with developers, restrict their access to the areas they are working on, so they don’t have a free pass to all your secrets or inadvertently leak them.
»Get started
Vault has multiple platform and hosting options to help your organization resolve secrets sprawl.
HCP Vault Dedicated: HCP Vault Dedicated is a SaaS-based solution for a number of use cases including secrets management/centralization, identity brokering, secret synchronization across other secrets manager tools, PKI certificate management, and encryption.
Vault Enterprise: Vault Enterprise is a self-managed platform with most of HCP Vault Dedicated's features, but self-managed for more strict regulatory circumstances.
HCP Vault Radar: HCP Vault Radar automates the initial scanning and ongoing detection and identification of unmanaged secrets so that they can either be revoked or migrated into Vault. It also provides remediation capabilities when integrated with Vault.
Resolving secrets sprawl requires a comprehensive approach covering people, processes, and technology. HashiCorp Vault can be a valuable technology within that approach, but for the best results it should be integrated into a broader compliance strategy that includes training, regular audits, and ongoing monitoring of your systems and processes.
To get started with HashiCorp Vault, visit the Vault product page. Please contact us if you’d like to discuss your secrets management journey.









