HCP Packer, a powerful tool for tracking, governing, and managing image artifacts across multi-cloud environments, has just added audit logs. This enhancement provides a way for organizations to document and monitor user activity across HCP Packer and gain visibility into the activity occurring in the registry. Audit logs are now generally available for all Plus-tier artifact registries.
Understanding resource lifecycles is crucial to successfully implement secure multi-cloud infrastructure. According to the 2023 HashiCorp State of the Cloud Strategy Survey, security ranks as the #1 factor in determining the success of an organization’s multi-cloud strategy. But without granular data and effective monitoring capabilities, it can be difficult to uncover security and compliance risks or identify if a breach has occurred. A lack of historical user activity data can also prevent organizations from uncovering insights regarding workflow inefficiencies and wasteful cloud spend.
»Introducing audit logs
Organizations can now gain complete visibility into their HCP Packer activity by relying on the audit log capabilities of the HashiCorp Cloud Platform (HCP). This offers insight into the lifecycles of their image iterations, buckets, and channels. This new functionality provides users with a description, metadata, and streaming capabilities for critical user activity information.
»Audit log descriptions and metadata
HCP Packer’s audit logs consist of a description (string) and metadata field (JSON object/hashmap). All HCP Packer audit logs contain common metadata, which relays information such as audit log status, type of operation being performed, organization and project ID, timestamp, and who initiated the operation.
In addition to the common fields, audit logs also send messages on specific operations taking place in HCP Packer such as:
- Buckets: Image bucket creation, deletion, updates, and labeling
- Iterations: Image iteration creation, completion, revocation, deletion, and restoration
- Builds: Build creation and updates
- Channels: Channel creation, updates, deletion, and iteration assignments
For a full list of all audit log types, their descriptions, and metadata, please refer to the HCP Packer documentation.
Below is an example of the metadata received when a user updates an image build:
{ "action":"update",
"actor":{
"principal_id":"test-auditlogs-911479@77f447d4-def0-46f2-bf09-6850d36745ed",
"service":{
"id":"test-auditlogs-911479@77f447d4-def0-46f2-bf09-6850d36745ed",
"name":"test-auditlogs",
"user_managed":true
},
"type":"TYPE_SERVICE"
},
"bucket":{
"id":"01GXXGSNEE1EMJEZ0TEH7KCQVX",
"slug":"bucket-test"
},
"build":{
"cloud_provider":"aws",
"component_type":"aws",
"id":"01H5APPBYYF4D0NMVZCRKR85E7",
"images":[
{
"image_id":"ami-f2",
"region":"us-west-2"
}
],
"labels":{
"os":"ubuntu"
},
"status":"DONE"
},
"description":"Updated build",
"iteration":{
"fingerprint":"f14",
"id":"01H5APNAK1BNEVMK3HPS7KZANV",
"version":"v5"
},
"organization_id":"77f447d4-def0-46f2-bf09-6850d36745ed",
"project_id":"a98c3c31-5760-4db1-b62b-0988080a66ad",
"registry":{
"id":"01GNZQS84K3PTGVVB2YY9R81BC"
},
"status":"OK",
"timestamp":"2023-07-14T17:21:09Z" }
»Audit log streaming
HCP Packer’s audit logs allow for near real-time streaming of audit events using industry-standard monitoring solutions such as Amazon CloudWatch or Datadog. Forwarding audit logs into these services allow organizations to observe higher-level correlations across all services and activities based on user or resource. Simply select the appropriate provider, enter the configuration details, and begin monitoring the full request and response objects for every interaction with the resource.
»Amazon CloudWatch
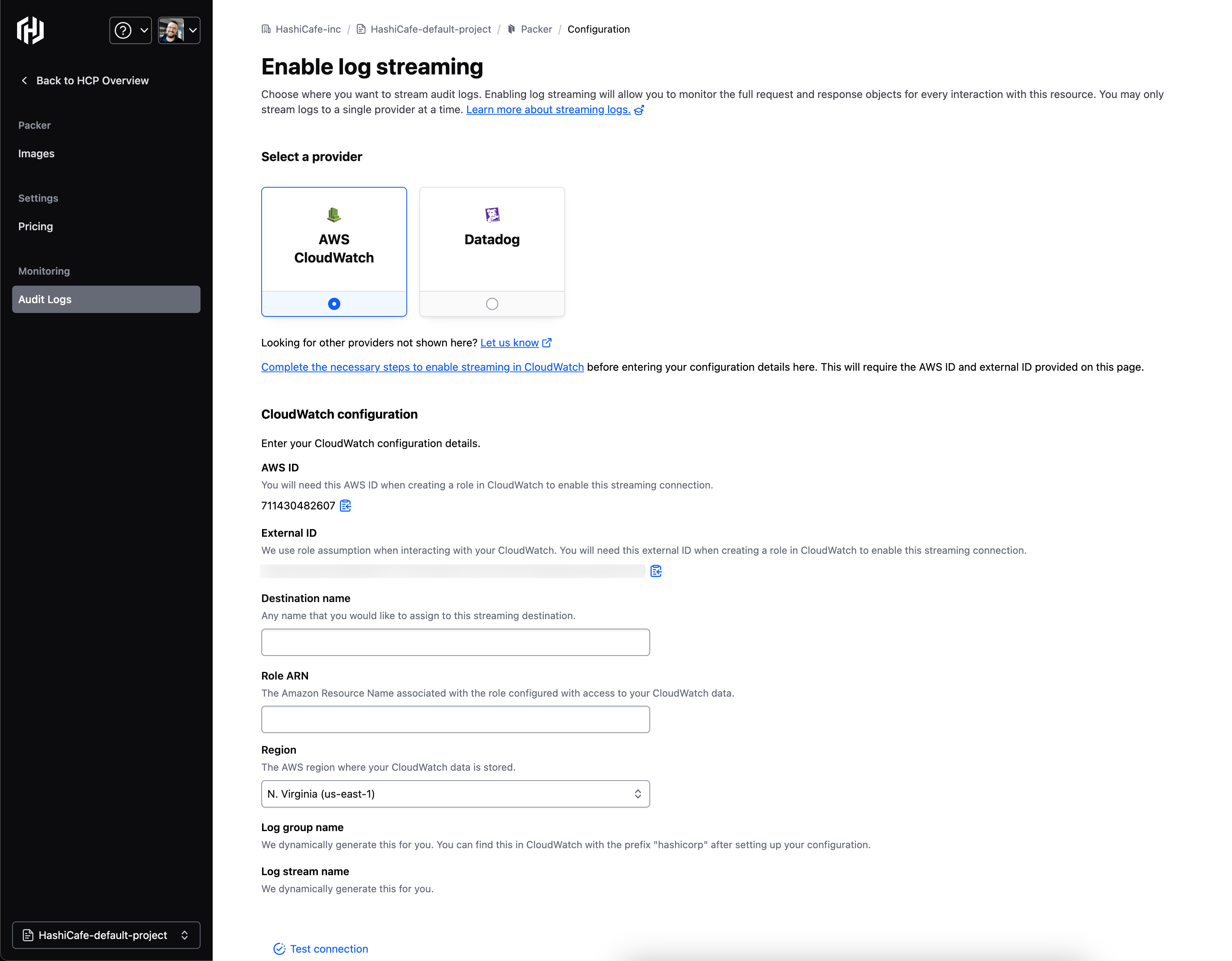
The log group and log streams are dynamically created and can be found in the Amazon CloudWatch console with the prefix “/hashicorp”. This lets you clearly see audit logs coming from HashiCorp separately from other log inputs you may have in CloudWatch.
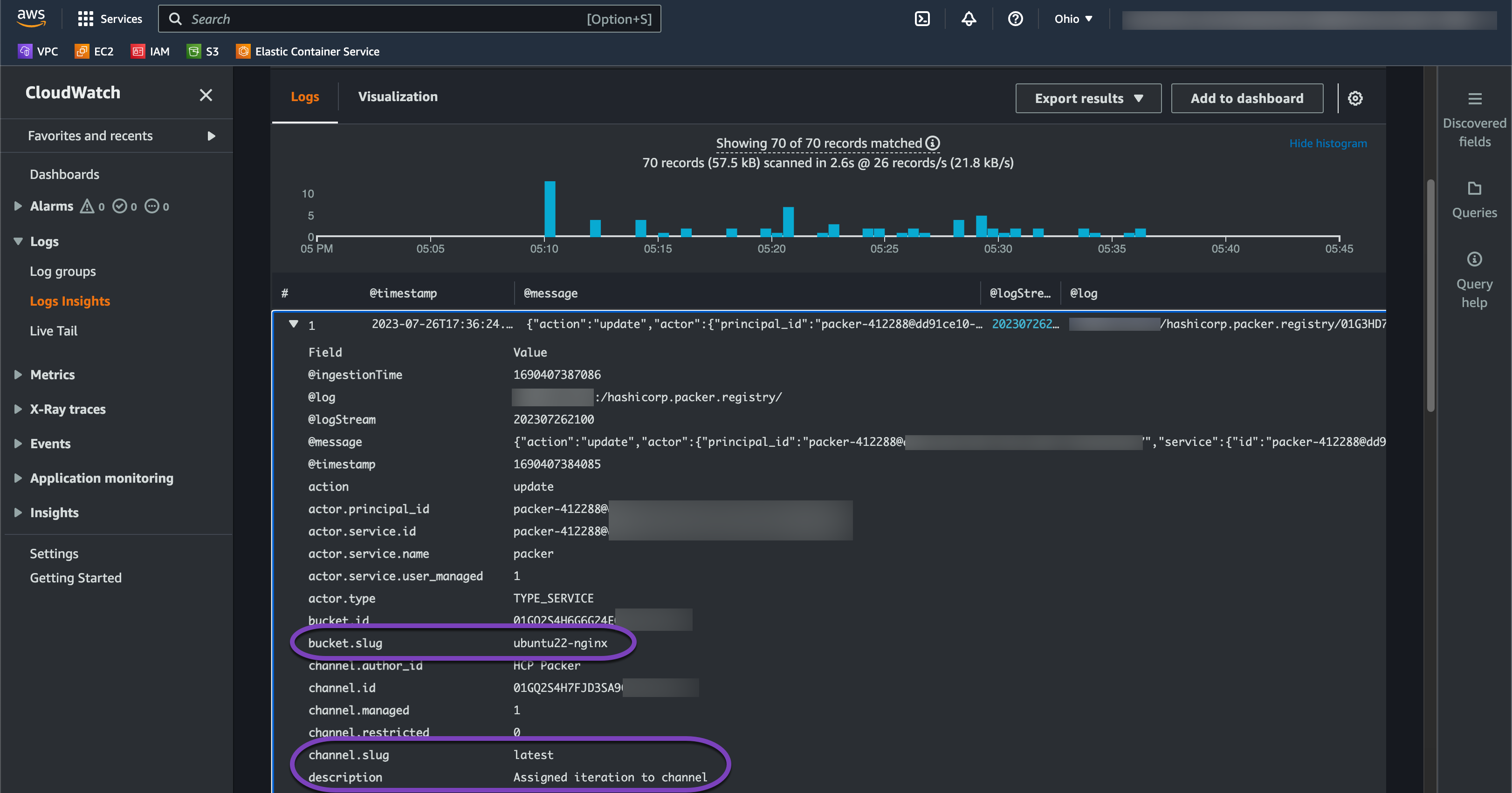
HCP Packer audit logs in Amazon CloudWatch Logs Insights.
»Datadog
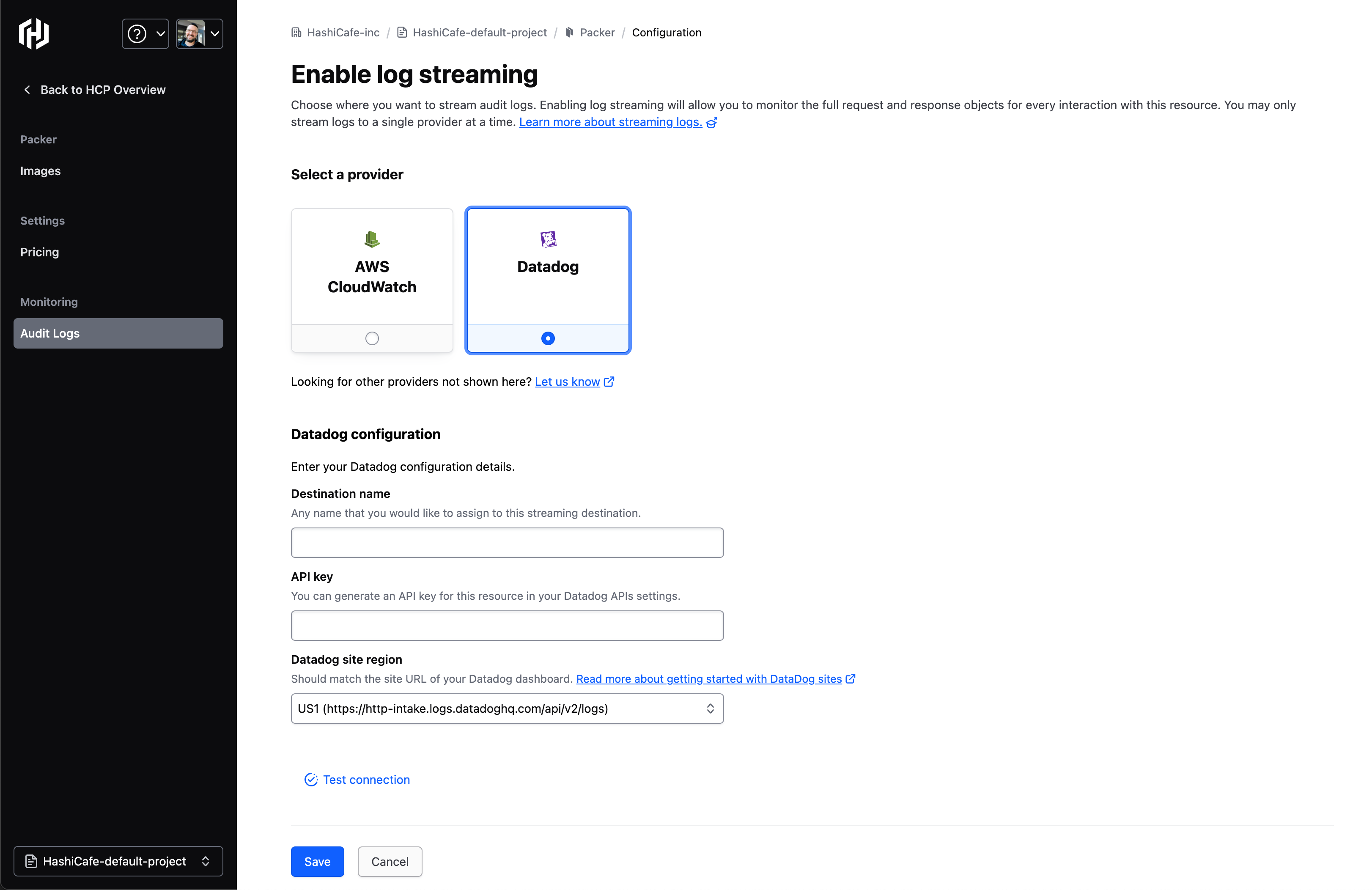
Logs arrive within your Datadog environment a few minutes after Packer usage. Refer to the Datadog documentation for details on log exploration.
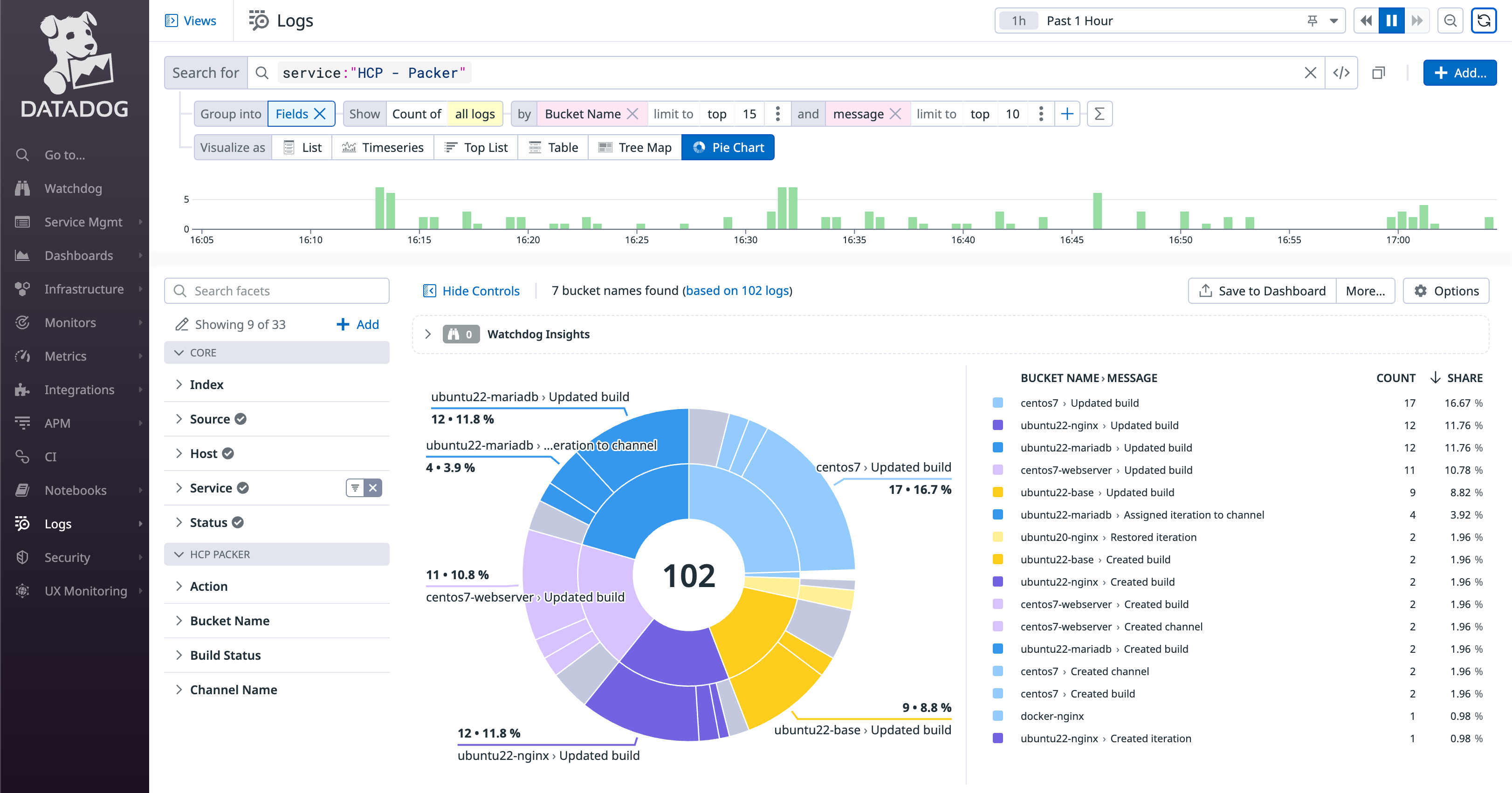
HCP Packer audit logs in Datadog with sample visualization.
»Key benefits of audit logs
Collecting activity data with HCP Packer’s audit logs helps organizations improve their:
Visibility: by enabling administrators to actively monitor a stream of user activity and answer important questions such as who is changing what? When? And where?
Security: by providing access to a historical audit trail that enables security teams to ensure compliance standards are met in accordance with regulatory requirements
»Summary and resources
For more information on audit logs for HCP Packer, please refer to the documentation:
Get started with HCP Packer for free to track and manage artifacts across all your cloud environments.








