Database Credential Rotation
Reduce the risk of breaches and credential leakage
Your Challenge
Each database in your organization requires credentials for access. These passwords are used by applications, services, and users.
Safeguarding credentials — and mitigating the risk from leaked credentials — is a complex problem. But it’s an important one: leaked credentials can leave your organization open to costly breaches and a loss of trust.
HashiCorp Vault can help you to overcome this problem by easily allowing you to create, rotate, and revoke database credentials through an automated workflow and API.
Automate credential rotation
HashiCorp Vault enables organizations to automatically rotate passwords for existing database users, applications, and services. Easily integrate existing applications with Vault, and improve secrets management.
- Improve securityReduce risk of breaches and credential leakage to ensure security of your networks, infrastructure, and data.
- Automate manual processesEliminate manual systems through automated processes to ensure information is secure and credentials only exist as long as necessary, limiting the window for a breach.
- Gain faster, more efficient auditingIncrease visibility into credential systems through detailed audit trails and logs to ensure and evaluate security posture.
"Vault was the solution for our business problem...Kubernetes that needed to connect to external services with credentials."
Diego Braga, Banco Popolare
Automate credential rotation to increase security and compliance
Secrets as a Service
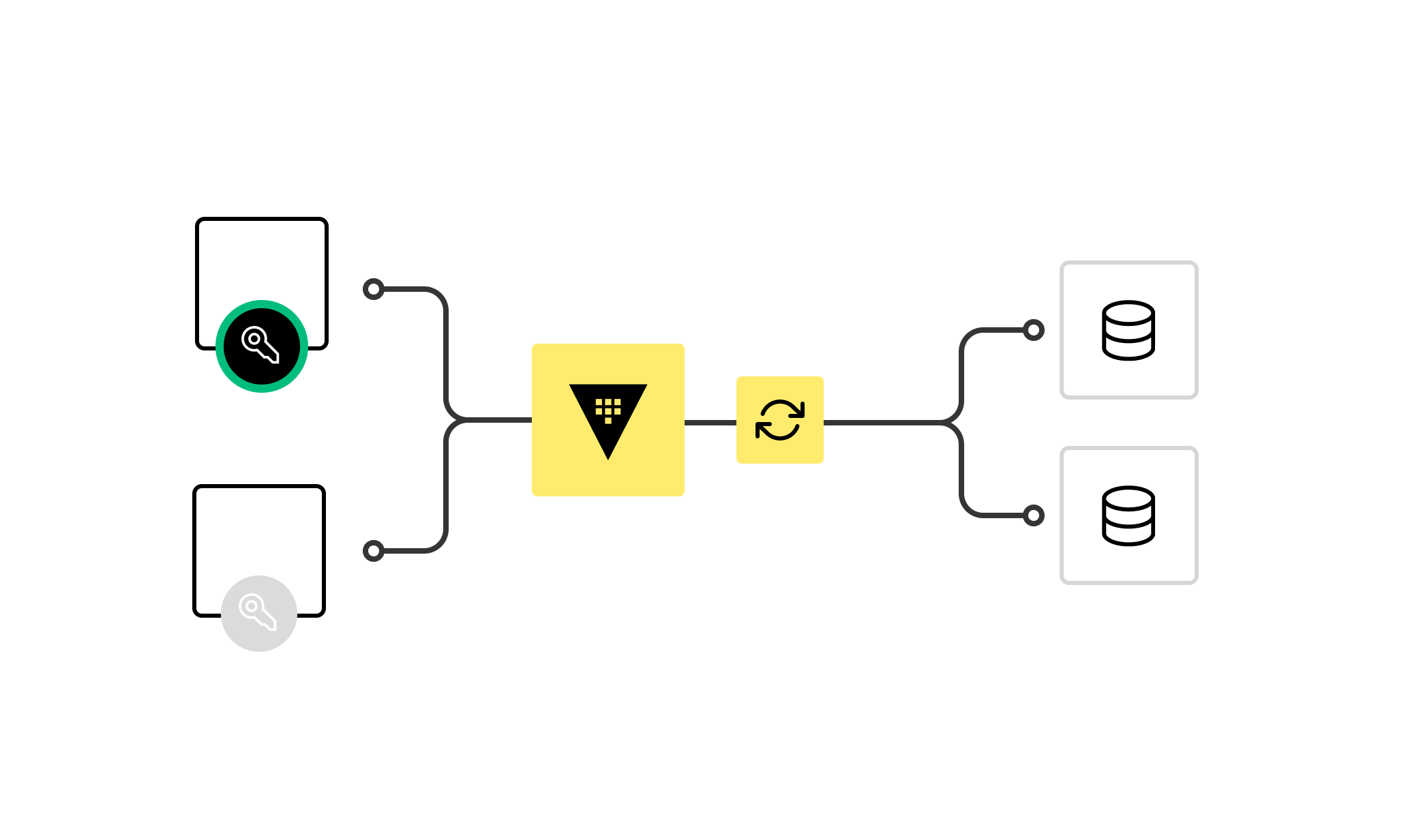
The Vault database secrets engine generates credentials dynamically based on configured roles. It is able to work with any combination of different databases leveraging a plugin interface, robust built-in database types, and frameworks that enable the running of custom database types. Services that need access no longer need to hardcode credentials: they can request them from Vault and use Vault's leasing mechanism to easily roll keys, creating dynamic secrets.
Services access databases with unique credentials, making auditing much easier.
Vault's internal revocation system ensures that users become invalid after a set time.
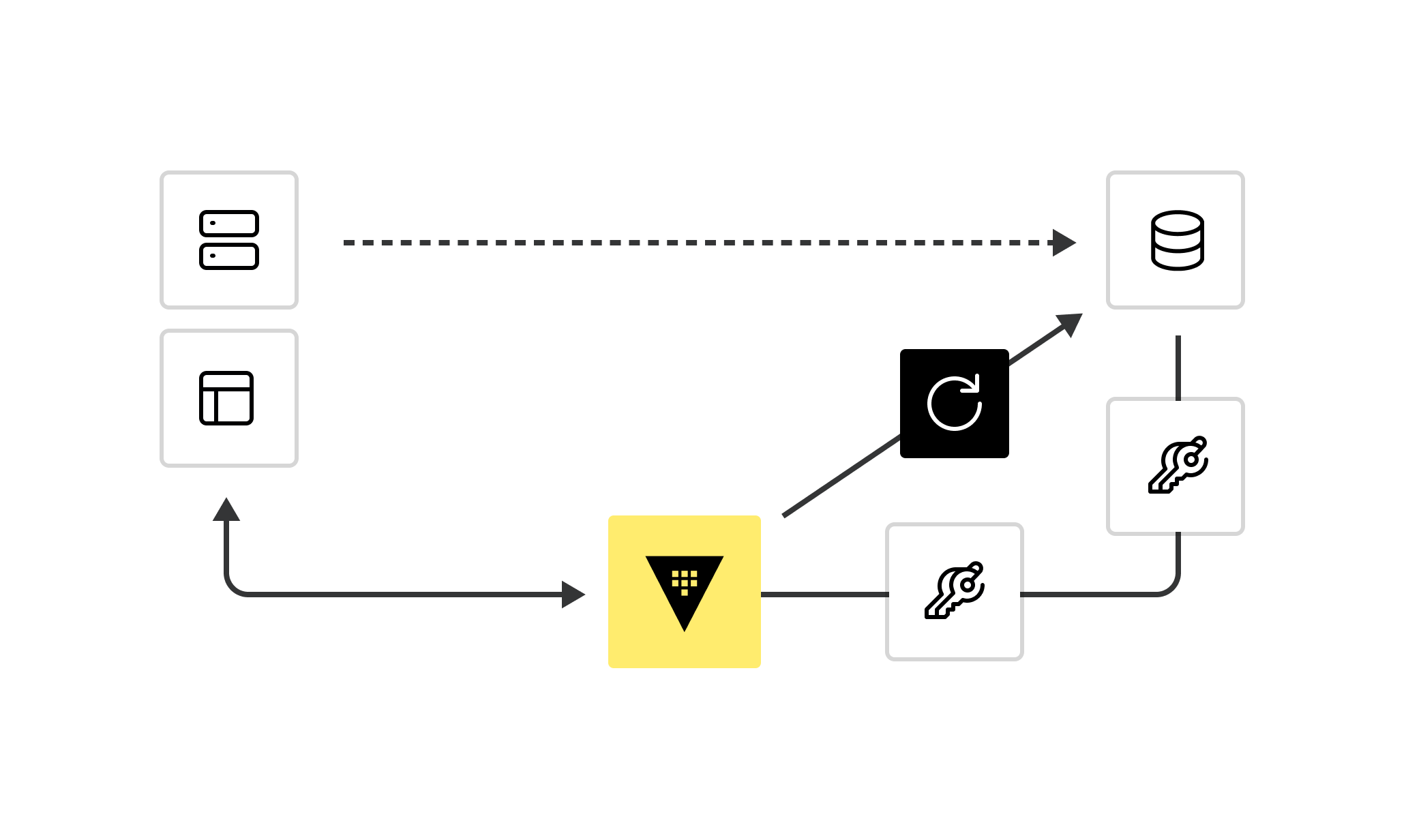
Dynamic secrets rotation and revocation
Applications “ask” Vault for database credentials rather than setting them as environment variables. Administrators specify the time-to-live (TTL) for database credentials so that they are automatically revoked when no longer used.
Each app instance can get unique credentials that don't have to be shared and are short-lived.
Using dynamic secrets reduces the chance they become compromised, and should that happen, individual secrets can be revoked rather than requiring global changes.
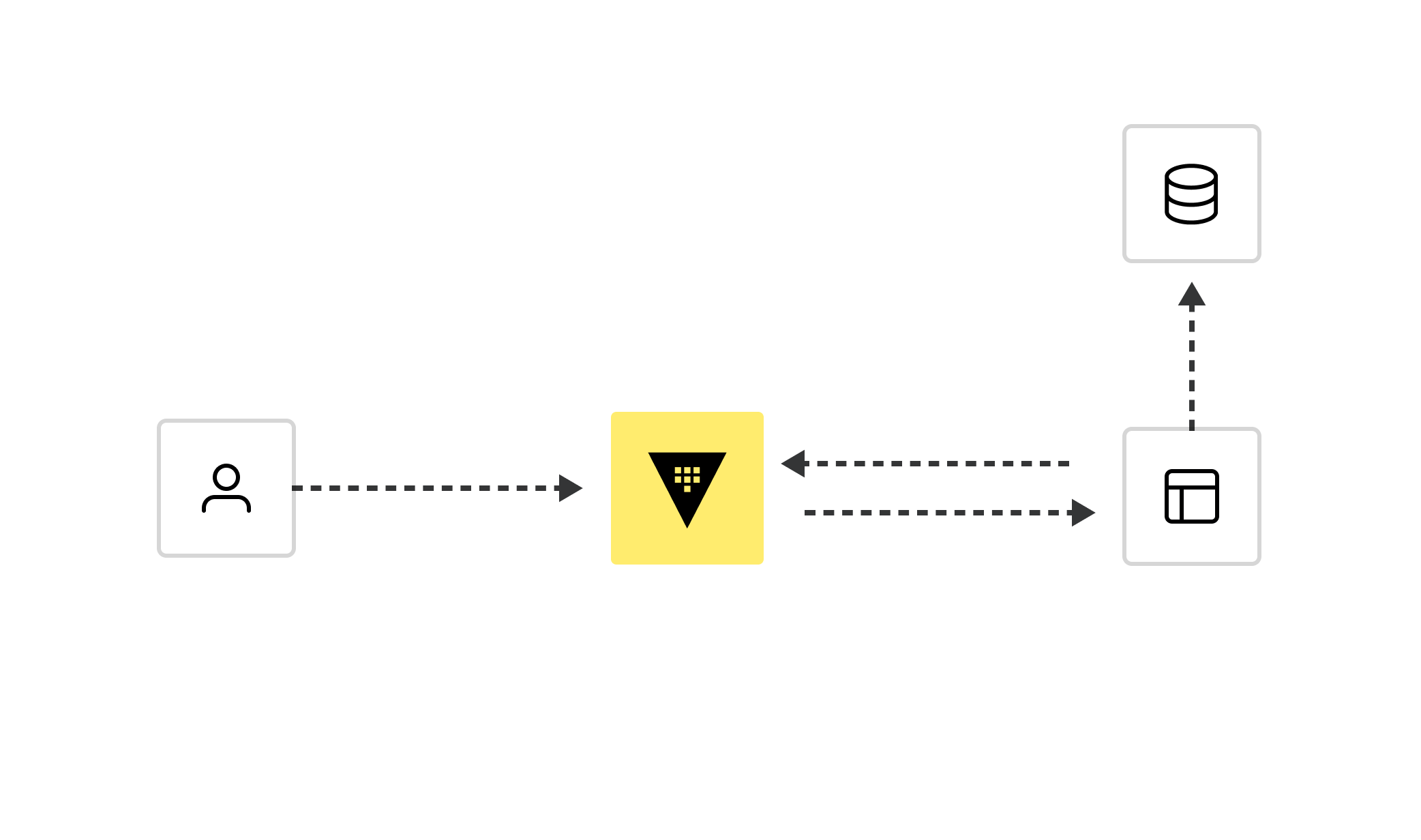
Database credential automation
Vault's database secrets engine provides a centralized workflow to automatically manage credentials for various database systems. Every service instance gets a unique set of credentials that live only for the life of that service. This also means that abnormal access patterns can be pinpointed to a specific service instance and its credential can be revoked immediately.
Policies and automated tasks reduce the need for manual tasks by database administrators, making database access and updates more efficient and secure.
Automated credential rotation maintains security and access to your information while reducing downtime.
Learn from your peers
Keep It Secret. Keep It Safe. Keep It Everywhere.
Adobe has been running Vault Enterprise in production for two years and now the platform services over 130 teams. Learn about all of the best practices and pitfalls of using Vault from this large-scale use case.
Explore our resources

Managing Target's secrets platform with HashiCorp Vault
Learn how Target manages and maintains its enterprise deployment of HashiCorp Vault from unattended builds and automated maintenance, to compliance and and client onboardings.

Database Credential Rotation with Vault
Eliminate long-standing shared credentials and reduce risk of breach and credential leakage with automated database credential rotation.
Dynamic secrets: database credential management
Vault's database secrets engine provides a database credential management solution so that the username and password can be dynamically generated upon request.
How to write a secrets engine for HashiCorp Vault from scratch
See how a HashiCorp Vault secrets engine plugin is built, step by step.
Take the next step
See how HashiCorp Vault can help you with all aspects of credential rotation and improve the security posture of your infastructure




