Update 2025: Read our more comprehensive guidance on cloud identity brokering in our key concept page: Cloud access management
As organizations adopt one or more public clouds they are faced with the challenge of securely providing access to secret material, such as usernames and passwords, API tokens, encryption keys, and TLS certificates. This problem is known as secret management, and there are several primary challenges:
- Authenticating or Asserting Identity. Many recent exploits have shown perimeter based security to be inadequate at stopping modern threats. Because of this, private networks need to operate a policy of zero-trust. Clients must present credentials that allow their identity to be verified, and their access authenticated.
- Imposing Authorizations. Once a client identity is verified, it does not mean they should have access to all secret materials. Instead, access should be on a need-to-know basis (also known as default deny), minimizing the blast radius of a compromise. This means we need to manage authorizations, or "who can access what".
- Auditing Access. Once we have verified clients and authorized them to access secret material, we want to maintain an audit trail to perform forensics after a compromise or for routine auditing purposes. The audit trail provides us non-repudiation, or a strong guarantee that a particular client did access something.
- Supporting Multiple Environments, Clients, and Systems. The final challenge is doing the above in a consistent way across different environments (VMware, AWS, Azure, GCP, etc), clients (Developers, Operators, Applications, Shell Scripts, etc), and systems (MySQL, Cassandra, RabbitMQ, MongoDB, etc). The combinatorial explosion makes it impractical to build a custom solution.
»Using Vault to Broker Access
Vault was created to solve the secrets management challenge while brokering access across a diverse and growing set of environments, clients, and systems.
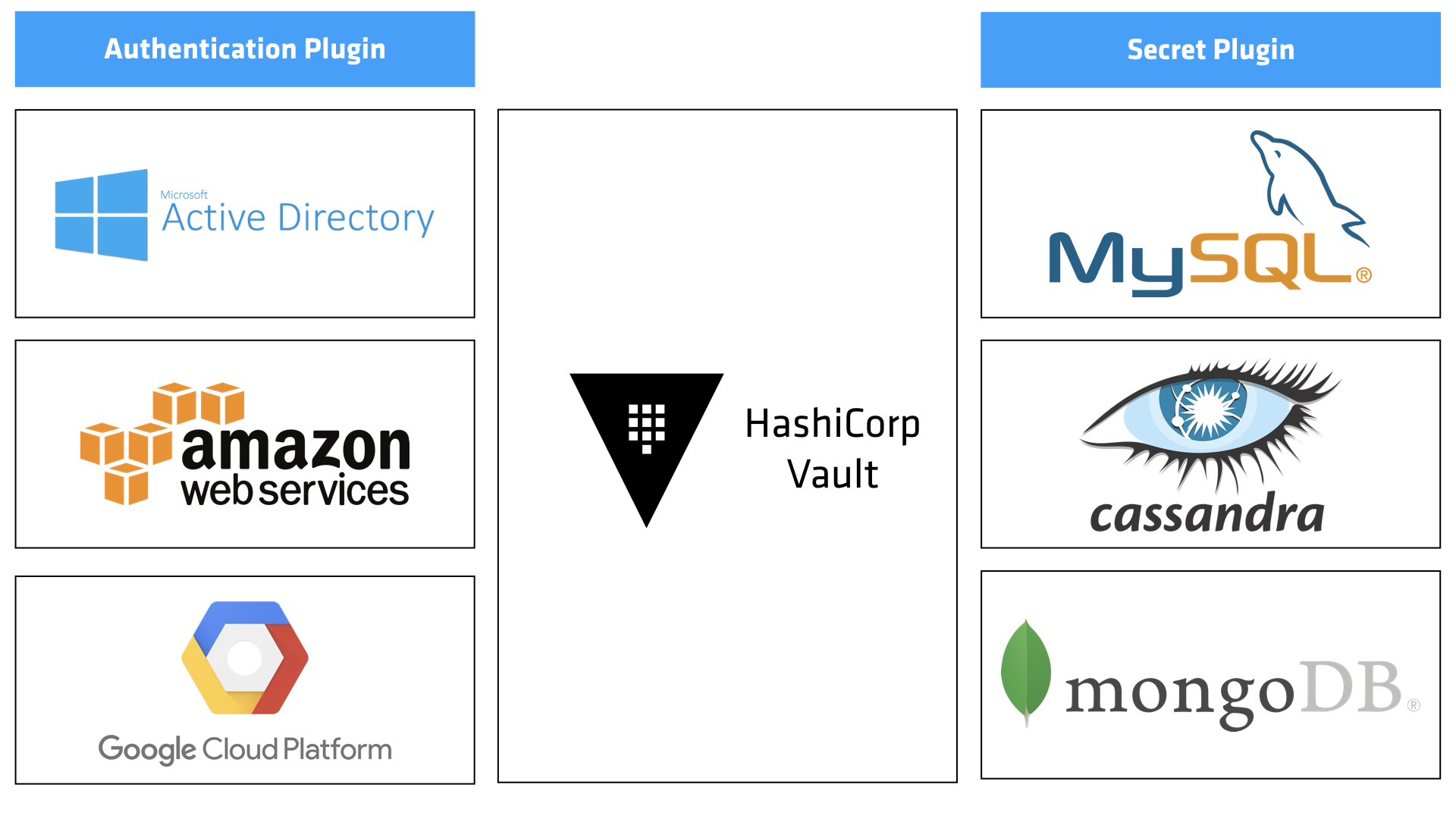
Vault provides a consistent API, user and group management, authorization policies, and plugin architecture. The plugin architecture allows Vault to be easily extended to solve the brokering challenge across a few different categories:
- Authentication Plugins. Authentication plugins solve the first challenge of asserting client identity. Vault integrates natively with LDAP / Active Directory, IDPs like Okta and Centrify, clouds like AWS and GCP, config management tools, and platforms like Kubernetes, among many others. This allows human operators to authenticate interactively and applications programmatically.
- Secret Plugins. Secret plugins solve the challenge of integrating with many different systems like databases (MySQL, PostgreSQL, MSSQL, Oracle, etc), messaging queues, cloud service providers, and more. A few lines of code allow Vault to generate unique credentials per client, to avoid sharing secrets and lower the attack vector.
- Auditing Plugins. Many organizations have existing solutions for centralized logging or audit logging, so Vault allows for integration of custom auditing backends. Vault is natively integrated with file based, socket based, and syslog for auditing.
»Crossing Cloud Boundaries
Many cloud providers expose API tokens to running instances, usually via a metadata API. This allows applications to easily make requests to cloud services, such as blob storage, without needing to explicitly manage tokens. This is very convenient for single tenant VMs running in a single cloud, but falls short for multi-tenant or multi-cloud architectures.
Imagine an application running in both AWS and GCP which needs access to both AWS S3 and GCP Cloud Storage. Each application instance can only run in one place, meaning it only has tokens for one cloud. Vault solves this problem, by allowing the clouds to be both an Authentication and Secret plugin.
Suppose an application is running in AWS, and needs GCP API tokens, here is how it would work:
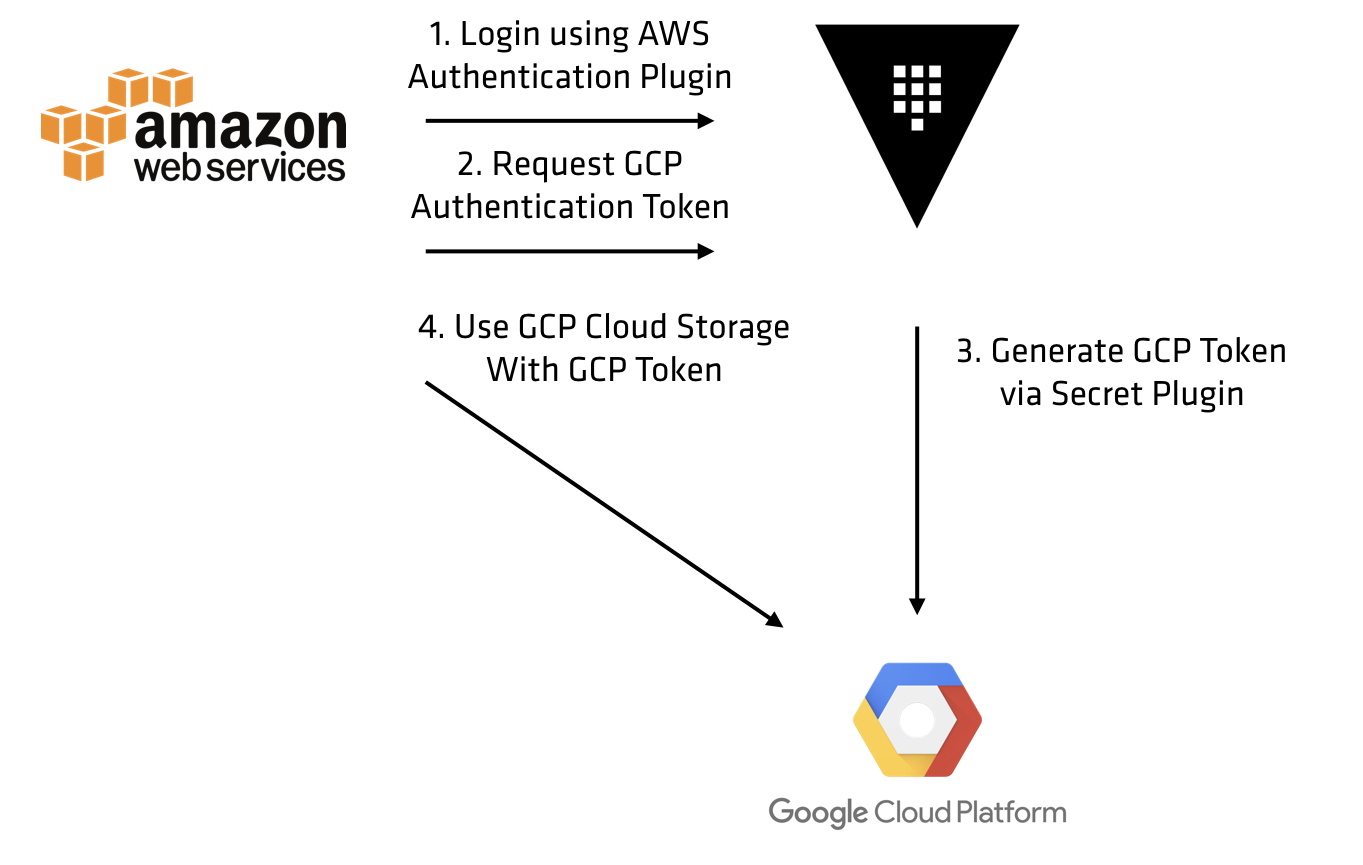
Here we can see how Vault helps broker access within a cloud, but also across them. This can simplify building multi-cloud applications. Chandler Allphin of Adobe gave a talk at HashiConf 2017 about their usage of Vault to solve just this problem.
»Conclusion
With each new public security breach, organizations are increasingly interested in improving their security posture. Assuming your network has been or will be compromised forces a new approach to secrets management, where access is carefully gated and audited. Vault provides a solution that is highly flexible, and can support the wide range of environments, clients, and systems that exist.
Learn more about Vault: https://www.vaultproject.io







