We are pleased to announce the availability of a beta release for HashiCorp Nomad 0.10.
Nomad is an easy-to-use, flexible, and performant workload orchestrator that deploys containers and legacy applications. Nomad is widely adopted and used in production by PagerDuty, Target, Citadel, Trivago, Pandora, and more.
Nomad 0.10 introduces advanced networking and storage features that enhance our support for stateful workloads and sidecar applications. The major new features in Nomad 0.10 include:
- Consul Connect: seamless deployments of sidecar applications with secured service-to-service communication and bridge networking
- Network Namespaces: secure intra-task communication over loopback interface for tasks within a group
- Host Volumes: expanded support of stateful workloads through locally mounted storage volumes
- UI Allocation File Explorer: enhanced operability with a visual file system explorer for allocations
»Consul Connect
Nomad 0.10 enables easy, seamless deployments of sidecar applications and segmented microservices through Consul Connect.
[
service {
name = "count-dashboard"
port = "9002"
connect {
sidecar_service {
proxy {
upstreams {
destination_name = "count-api"
local_bind_port = 8080
}
}
}
}
}
]
Consul Connect introduces new connect and sidecar_service stanzas for service jobs. Nomad will automatically launch and manage an Envoy sidecar proxy alongside the application in the job file. This Envoy service is registered with Consul and is used to provide mTLS communications with other applications within the Nomad cluster. Sidecar configuration is available through the new upstreams stanza and its destination_name and local_bind_port parameters.
See the Consul Connect Integration guide for more details.
»Network Namespaces
The network stanza is now configurable with three modes: bridge, host, and none. Bridge mode enables secure intra-task communication over the loopback interface. Tasks within a task group can now share a networking stack (interfaces, routes, firewall) that is isolated from the host.
»Host Volumes
Nomad 0.10 expands support for running stateful workloads with Host Volumes.
host_volume "mysql_hv" {
path = "/opt/mysql/data"
read_only = false
}
External storage volumes attached at the node level can now be made available to Nomad with the new host_volume stanza in the client configuration. Read/write access can additionally be set through the read_only parameter.
job "myapp" {
group "db" {
count = 1
volume "mysql_vol" {
type = "host"
config {
source = "mysql_hv"
}
}
restart { ... }
task "mysql" {
driver = "docker"
volume_mount {
volume = "mysql_vol"
destination = "/var/lib/mysql"
}
config { ... }
resources { ... }
service { ... }
}
}
}
The new volume and volume_mount stanzas in the job file enable users to mount storage volumes into the applications that require them. Nomad will automatically ensure that the specified storage volume is available and mounted into the job at the task or group level, depending on the required granularity.
See the Host Volumes guide for more details.
»Allocation File Explorer
Nomad 0.10 brings the ability to browse the file system of an allocation to the Web UI, including streaming files and viewing images.
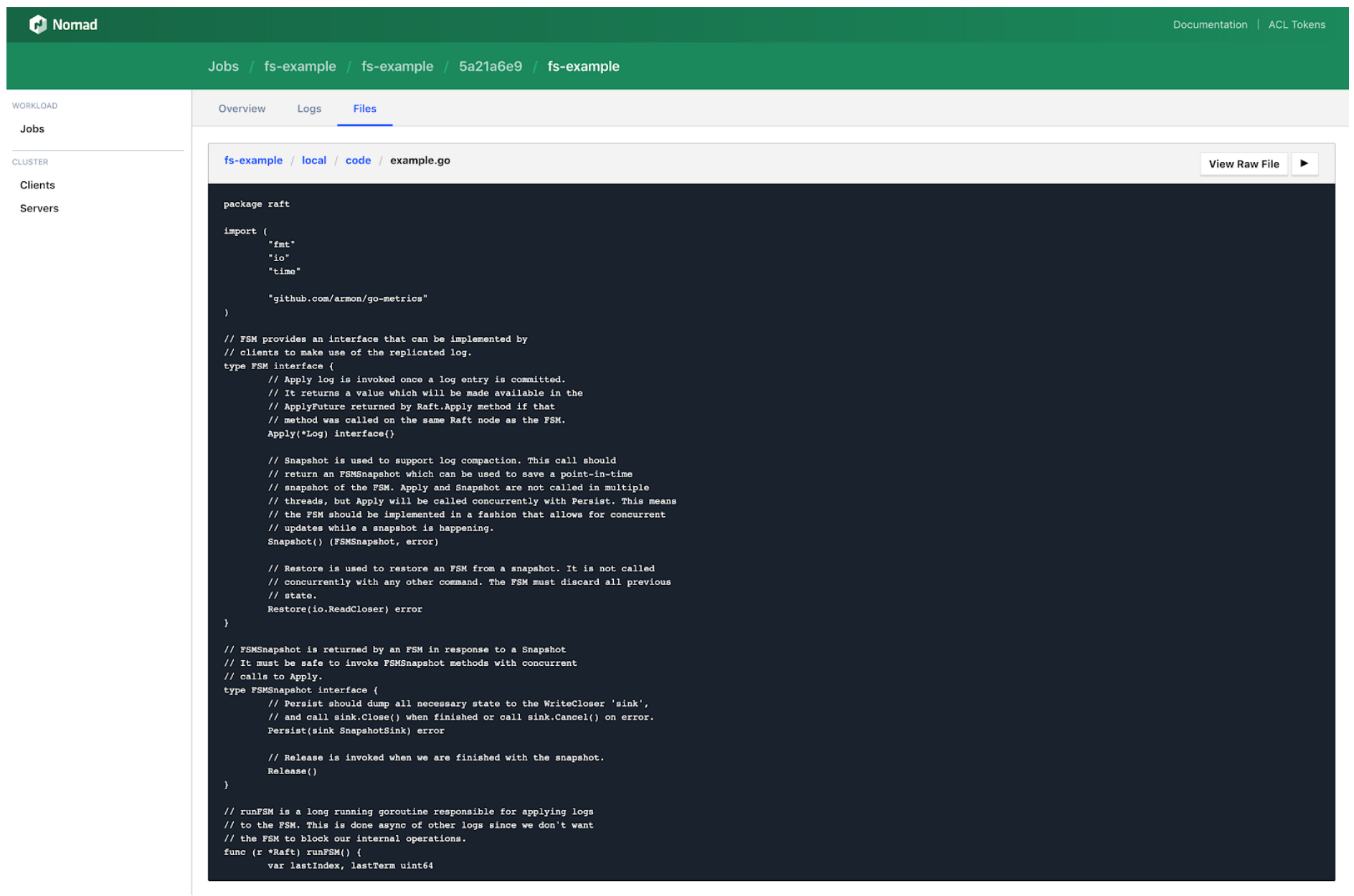
Files in an allocation’s directory are now visualized in the Nomad Web UI, which enables faster, intuitive debugging at the file system level. Historically, the file system was accessible in Nomad through only the command line via nomad alloc fs. The Allocation File Explorer is especially effective for users who write Nomad logs directly to files instead of the default stdin/stdout.

Images will be automatically rendered and files will be streamed when applicable. Nomad’s Allocation File Explorer will be familiar to Consul or Vault users, which have similar visualizations for key values and secrets, respectively.
Note: We encourage you to experiment with these new features, but recommend against using this build in a production environment. Depending on feedback and resolving outstanding issues, we may release further betas, release candidates, and will publish a final generally available Nomad 0.10 release when appropriate.
Thank you to our active community members who have been invaluable in reporting bugs and improving the documentation for Nomad in this release!







