HCP Vault Secrets adds enterprise capabilities for auto-rotation, dynamic secrets, and more
HCP Vault Secrets focuses on making a fast and easy path for secure development with key new features including auto-rotation (GA), dynamic secrets (beta), a new secret sync destination, and more.
HCP Vault Secrets, HashiCorp’s cloud-native secrets lifecycle management platform, focuses on making secure software delivery paths easy for developers to follow. It’s the fastest way to get up and running with Vault secrets management, solve secret sprawl with centralized secrets lifecycle management, and lower the overhead of creating, storing, rotating, and deleting secrets.
At HashiConf we announced advanced capabilities for HCP Vault Secrets, including the general availability of auto-rotation, the public beta of dynamic secrets, and key upgrades to our granular access control capabilities. Other recent improvements include a new secrets sync destination, Workload Identity Federation (WIF) authentication via HashiCorp Cloud Platform (HCP), and notification webhooks.
»Auto-rotation ends manual rotation toil and neglect
HCP Vault Secrets auto-rotation, now generally available, adds an additional level of automation to an organization’s security management playbook. Teams that only use static secrets are taking on significant risks. If they let secrets live too long, threat actors have ample time to do damage if they gain access to active secrets. Teams will often set long expiry windows because there’s often a large effort involved with manual secret rotation at scale. This isn’t just theory. Before they eventually adopted Vault, Canva’s engineering productivity would dip when it was time to rotate secrets.
Automatically generating and rotating short-lived secrets at defined intervals is the solution for these challenges. It minimizes the potential impact of compromised credentials because it reduces the time in which they can be used maliciously. This auto-rotation strategy is significantly more secure and less work than manually rotated static secrets. In some use cases it is a better fit than dynamic secrets.
For a deeper dive into the differences and similarities of these two strategies, read: Rotated vs. dynamic secrets: Which should you use?
In HCP Vault Secrets, automated secret rotations can be set to a 30, 60, or 90-day rotation cadence, or they can be rotated on demand. In an emergency, admins can also automatically revoke or rotate a secret. In the GA release, users can now leverage two additional integration partners: AWS and Google Cloud, in addition to MongoDB and Twilio. To help maintain application uptime, HCP Vault Secrets allows you to have two versions of each secret live at a time.
Learn how to set-up auto-rotation for your credentials.
Auto-rotation integrates with partners such as MongoDB, which allows platform teams to add a deeper layer of protection to their infrastructure. According to Zuhair Ahmed, Senior Product Manager at MongoDB, "The integration of MongoDB Atlas with HCP Vault Secrets enhances data security by automating the management of database credentials. This move helps prevent breaches by storing, rotating, and revoking access as needed."
»Automate and issue ephemeral just-in-time credentials with dynamic secrets
Dynamic secrets, now available in public beta for HCP Vault Secrets, allow users to generate just-in-time, short-lived credentials for AWS and Google Cloud using WIF to provide secure access to resources at scale. Implementing dynamic secrets helps users minimize the risk and operational overhead associated with long-lived static credentials by creating a new short-lived secret for each unique access request.
In addition to supporting dynamic secrets, HCP Vault Secrets now offers dynamic cloud credentials for HCP Terraform (currently in public beta). Using this integration, when HCP Terraform automates provisioning with infrastructure as code, HCP Vault Secrets, as your central secrets manager, will dynamically retrieve them during the provisioning process, eliminating the need for static secrets embedded in code. This strengthens security by shrinking the attack surface and enhances visibility through granular access control and comprehensive audit logging functionalities in both platforms.
Learn how to manage dynamic secrets with HCP Vault Secrets (for cloud providers and applications)
»Utilize granular access controls to manage actions within your organization
HCP's identity and access model provides roles to govern what actions users or service principals can perform within HCP Vault Secrets. These roles and permissions can be granted broadly to access all resources within an HCP organization or project, or they can be scoped down to individual resources such as applications. This flexibility helps organizations securely define administrative boundaries for teams and apply least-privileged access principles to secrets.
HCP Vault Secrets provides fine-grained roles that can be applied to projects and applications. These roles enable precise access control, giving users only the permissions they need to perform their necessary tasks.
Now, HCP Vault Secrets allows admins to set roles for secret reader or application admin. Refer to the HCP Vault Secrets documentation to learn more.

Roles and permissions can be granted by organization, project, or application level.
»Secrets sync broadens centralization with support for HCP Terraform sync destination
HCP Vault Secrets lets you centrally manage secrets and sync them to destinations you may already have in your stack. This is done through the secret sync feature, which instantly makes secrets available across multiple platforms and keeps them up to date with the latest versions from any source.
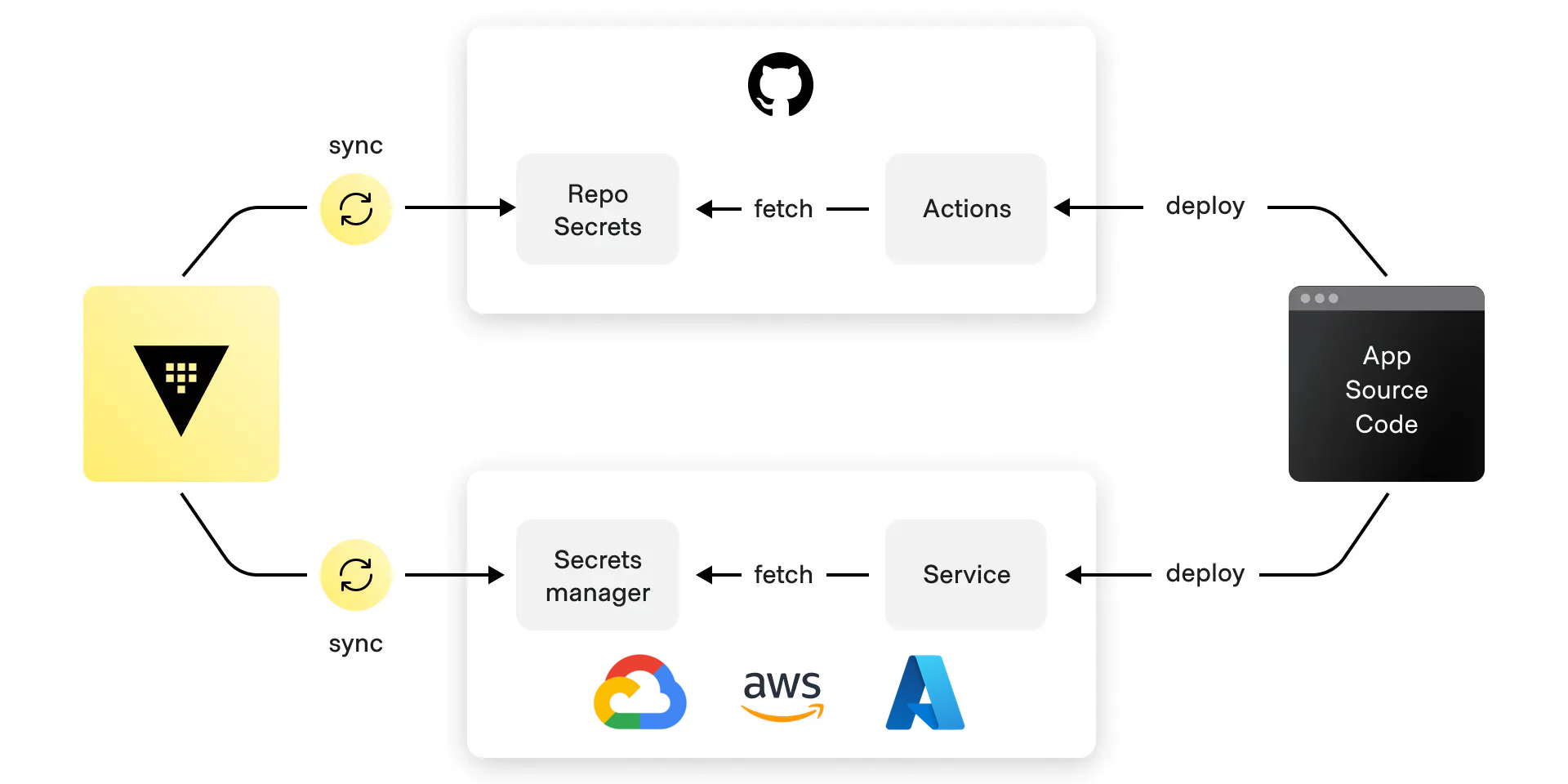
Continually sync secrets to 3rd party providers
Secrets sync saves teams significant time by automating the centralization of secrets into a single management plane that can provide a standard, unified secrets management workflow for the whole organization. Secrets sync also saves time by eliminating the arduous task of interfacing with multiple cloud vendors and key managers for access.
The latest update to this feature adds a new sync destination: HCP Terraform workspace variables and variable sets. This allows for a more streamlined secrets management process within the HCP Terraform provisioning workflow by adding the ability to make native secret references within Terraform runs.
HCP Terraform lets you override variables defined in variable sets on a per-workspace basis, which lets you modify the workspace's configuration without affecting other workspaces that use the variable set. When you update the values, the changes automatically affect all associated workspaces, making it easier to update credentials and infrastructure settings.
The complete list of available sync destinations now includes:
- AWS Secrets Manager
- Azure Key Vault
- Google Cloud Secret Manager
- GitHub Actions
- Kubernetes
- Vercel
- HCP Terraform
Automating these HCP Terraform secrets management processes reduces the risk of human error and unauthorized access, creating a more secure and compliant environment. Embracing this integration should streamline operations and fortify your security posture.
»WIF offers a secretless configuration experience
With HCP Workload Identity Federation, service principals can now be configured in a trust relationship with external identity providers, allowing workloads to use their native identity systems to authenticate into HCP Vault Secrets. This eliminates the need to manage long-lived, static key pairs to authenticate clients and offers a secretless configuration experience. The result is an improved security posture and reduced risk with less overhead.
Authenticating external applications and workloads to HCP Vault Secrets is achieved with service principals: assigned role-based permissions to control what actions can be performed across various resources, enabling least-privileged access control and providing a programmatic way for workloads to authenticate requests from various platforms and runtimes. You can generate unique key pairs from the service principal and use them as credentials in machine-driven workflows that need to interact with HCP Vault Secrets.
»Webhooks improve workflows and visibility
Webhooks can be configured to trigger or notify external systems when specific events occur within HCP Vault Secrets. This lets you extend workflow automation around secret lifecycle events to other tools within your technology stack. Examples include notifying teams when their secrets have been created and are ready for use or triggering a pipeline to run when a secret changes.

HCP Vault Secrets events can trigger notifications, builds, deployments, and Terraform runs.
»Get started
These new HCP Vault Secrets features make it even easier to adopt modern cloud security best practices by accelerating the onramp to high-maturity secrets management.
Learn more about HCP Vault Secrets here and sign up for our free tier today to access lifecycle management capabilities for your secrets.
Sign up for the latest HashiCorp news
More blog posts like this one

HashiCorp at Microsoft Build 2025: New products to automate, secure, and scale on Azure
Learn about the latest news from the HashiCorp and Microsoft ecosystems as we kick off Microsoft Build 2025 this week.

Why adopt HCP Vault Radar
HCP Vault Radar, enables teams to move from reactive firefighting to proactive secret remediation and management.

The 18-point secrets management checklist
How you handle secrets should evolve as your cloud journey progresses. Follow this best-practices checklist as a guide.