The Vault team is quickly closing on the next major release of Vault: Vault 0.11. As we approach the release we will preview some of the new functionality coming soon to Vault Open Source and Vault Enterprise.
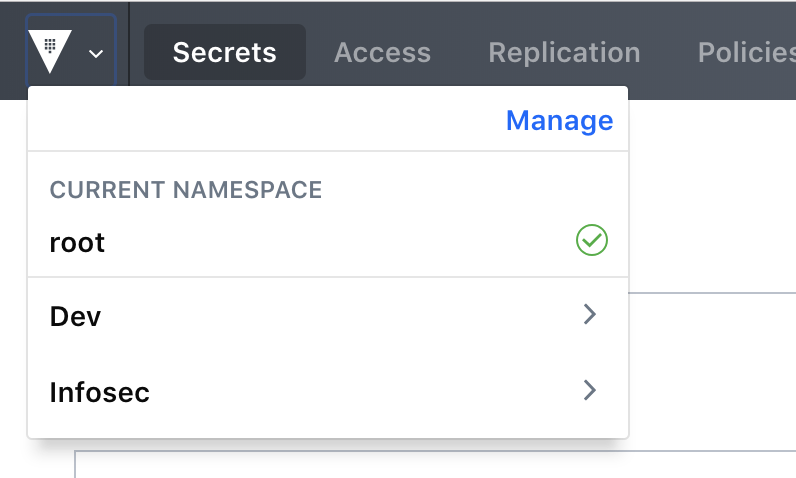
This post will focus on namespaces: a new feature in Vault Enterprise that enables the creation and delegated management of secure multi-tenant environments within a single Vault Enterprise infrastructure.
Over the last two years Vault has become an essential part of many organizations’ production environments. Some of the sensitive information protected by Vault today includes information on upcoming IPO and M&A transactions, credentials to databases containing PII data, and even application tokens and certificates used by defense systems in Multilevel Security (MLS) clearance infrastructures.
Secrets like these are often subject to regulations like GDPR, SEC broker-trade regulations, and NIST SP 800-53 that require strict isolation of this data. Even without these regulations, providing delegated tiers of administrators within Vault is critical to help deal with the human cost of writing/managing policies as Vault Enterprise infrastructures grow.
Namespaces allow Vault Enterprise users to create isolated namespaces within a centrally managed Vault infrastructure. These namespaces maintain a discrete set of Secret Engines and policies that are invisible to other users and can be managed by delegate admins that are empowered with rights to manage their own tenant environment.
Consider the fictional company Bream/Hall. Bream/Hall is a Managed Security Services Provider for a series of tech company clients.
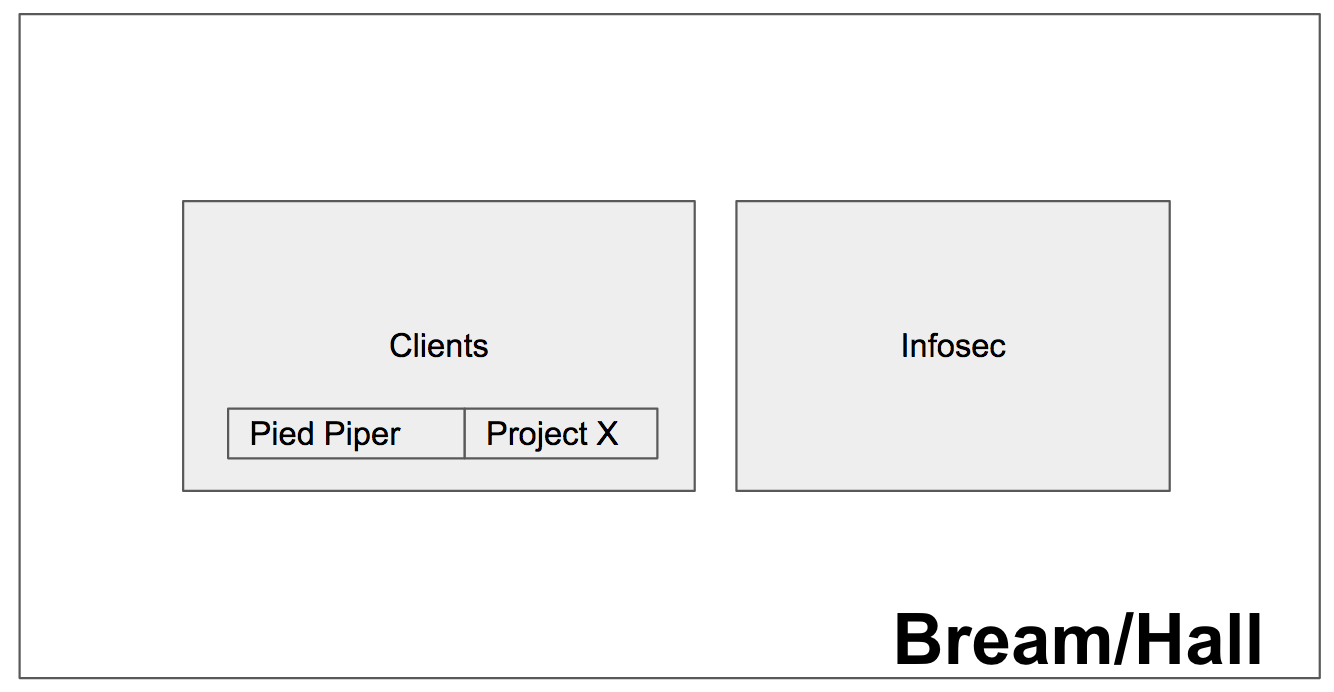
Two of those developers are Pied Piper and Project X, independent companies who contract Bream/Hall to manage their sensitive access credentials and encryption keys. They are competitors and are managed by different teams within Bream/Hall.
Bream/Hall also has an independent Infosec group that manages internal security for Bream/Hall, their own credentials and cryptography infrastructure, and protects the overall infrastructure for their clients.
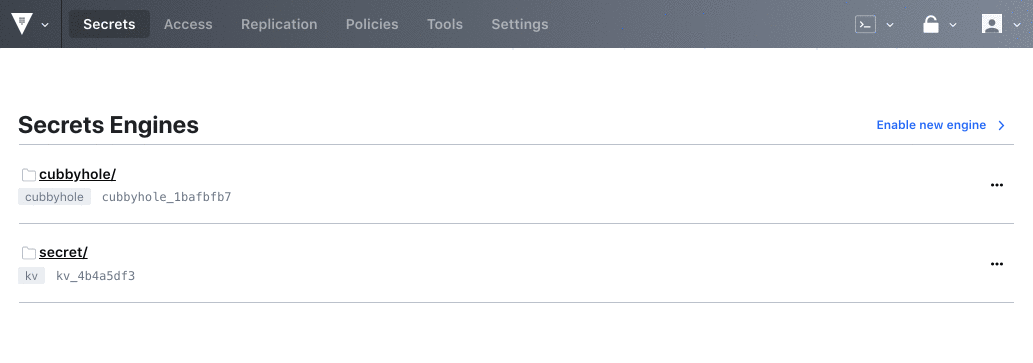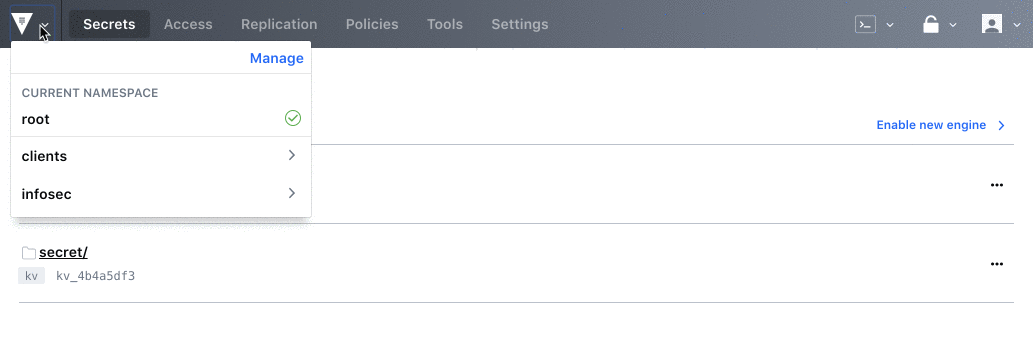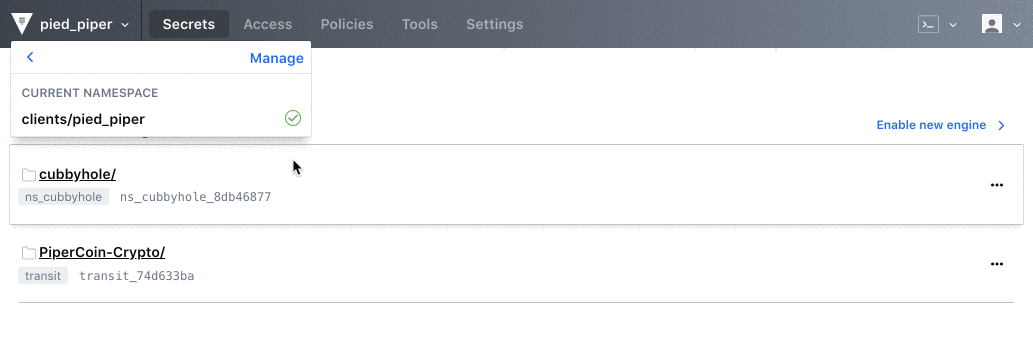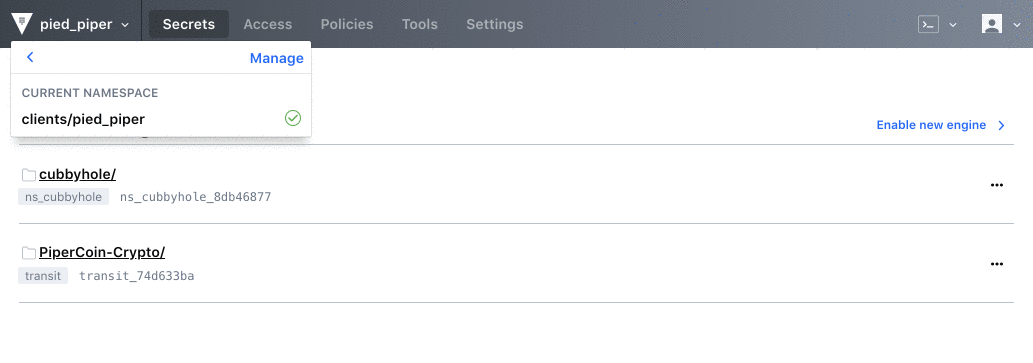
Namespaces allow Bream/Hall to create isolated tenant environments for their clients’ account teams. The teams managing security credentials for Pied Piper and Project X cannot see each other or each other’s infrastructure.
Namespaces can create and manage separate versions of the following:
- Secret Engines
- Auth Methods
- Identities (Entities and Identity Groups)
- Policies
- Tokens
Additionally, users in a namespace log in via a separate login path. For all intents and purposes, they are presented with their own “Vault within a Vault."
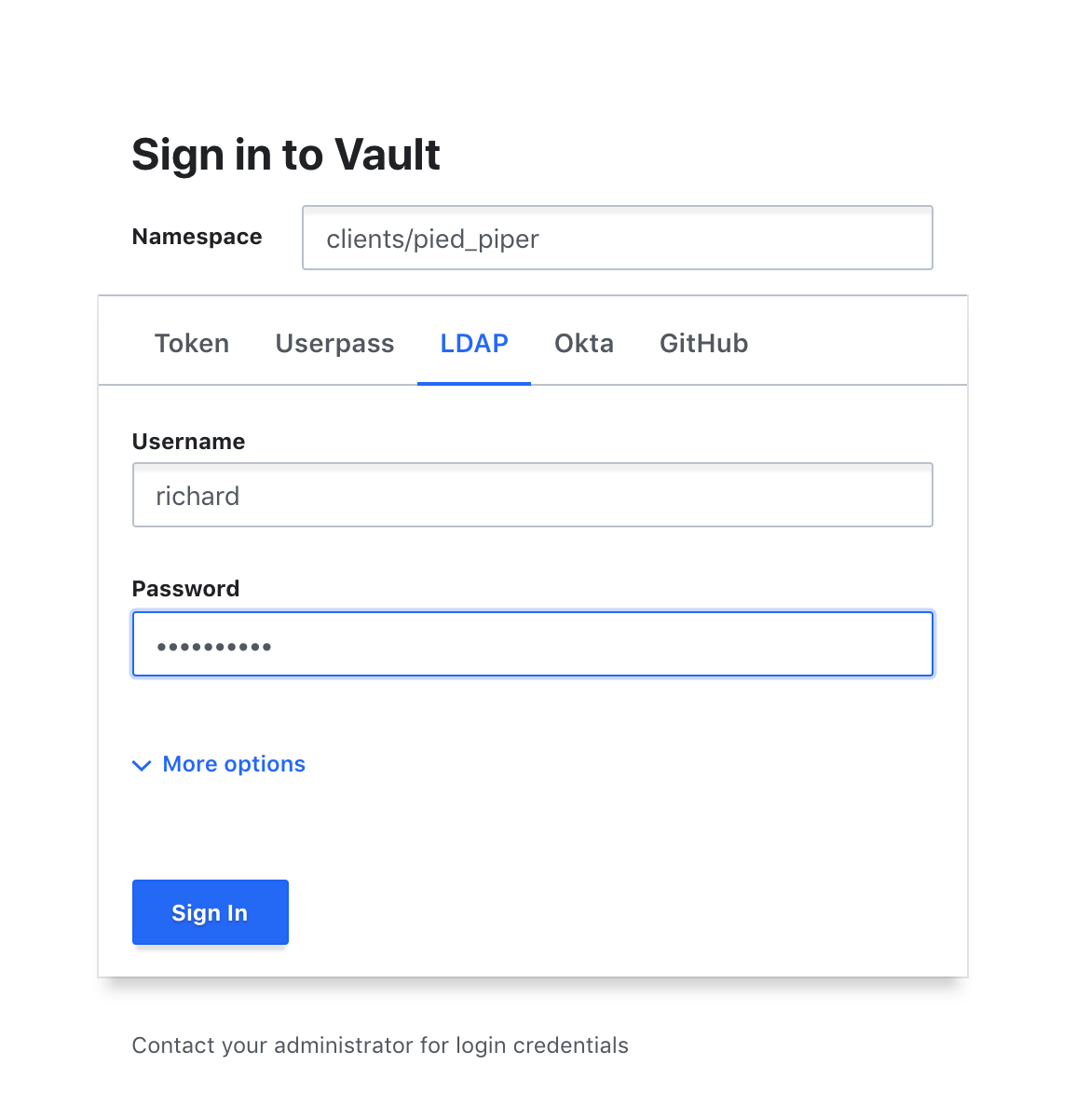
These isolated namespaces can still leverage the benefits of centralized management within Vault. Teams within Pied Piper and Project X can use existing Auth Methods configured for Bream/Hall’s Vault, and the Bream/Hall Infosec team can be configured to enforce Sentinel requirements for some or all of Bream/Hall’s teams when they use Vault. Namespaces can also be configured to inherit select secrets mounts in order to streamline the process of creating and managing namespaces.
Delegated admins can also be created to manage namespaces. These admins can create ACL policies that apply only within their namespace, and higher level admins authorize which powers are given to their delegated admins. Delegate admins can even create their own namespaces—and grant access to other users to manage those namespaces.
»What’s Next?
Namespaces is just one of many new features coming soon in Vault 0.11. In our next feature preview we will be looking at Vault Agent: a new open source application we are releasing with Vault 0.11 to streamline secure introduction and accessing of secrets locally by users and applications.








