We are excited to announce native Open Policy Agent (OPA) support for Terraform Cloud is now generally available. First launched as a public beta during HashiConf Global 2022, this feature extends the policy as code capabilities of Terraform Cloud to support OPA. OPA is based on the Rego policy language and works alongside Sentinel to increase the number of supported ways customers can adopt a policy as code framework for secure multi-cloud provisioning. Native OPA support helps simplify adopting and maintaining policy enforcement workflows in Terraform Cloud.
»Policy as Code Approaches
Open Policy Agent is an open source general-purpose policy engine. OPA uses a high-level declarative language called Rego that, much like Sentinel, is used to enforce controls using policy as code. HashiCorp Sentinel is a powerful policy as code framework that has been part of Terraform Cloud and Enterprise since their inception. However, organizations that have already invested in OPA may want to leverage those existing skills and policies. Previously, this required Terraform users to create their own tooling to incorporate OPA into their Terraform Cloud workflows. Maintaining these solutions required significant time and effort, potentially reducing focus on security and resource compliance. The native OPA support in Terraform Cloud removes the need for that custom tooling.
»Native OPA Benefits
The native OPA integration allows customers to migrate their existing Rego-based policies into Terraform Cloud with minimal engineering effort. As with Terraform and infrastructure as code, OPA allows users to rely on a single language for policy as code for different configurations and resources. This makes it easy to create and share reusable policies with the rest of the organization.
Teams can now choose their desired policy framework and collaborate seamlessly across their organization. Native OPA support also allows Terraform Cloud users to take advantage of the platform’s mature policy workflows. These workflows help simplify policy enforcement and free users from the burden of using custom or third-party tools to connect OPA and Terraform Cloud.
»Native OPA Support for Terraform Cloud
Adding native OPA support to Terraform Cloud allows teams to have an additional framework choice when adopting a policy as code approach. In some organizations, multiple teams are responsible for different policies, such as compliance or operational best practices. Limiting these teams to a single policy framework can cause less than optimal policy enforcement processes. OPA and Sentinel can operate side-by-side so each team can choose its preferred framework and work together seamlessly.
The native OPA support in Terraform Cloud includes:
- Individually managed or VCS-connected policies: Edit policy code directly in the UI, or use the recommended approach of connecting to a version control repository containing your policies.
- Policy sets: Group policies and enforce them on workspaces.
- Enforcement levels: Define behavior for when policies fail as part of a policy check.
- Policy overrides: Enable users to override a failed policy check and continue the execution of a run.
- Role-based access control (RBAC): Grant team permissions to manage policies and override policy failures.
- Auditing: Policy results are included in audit logs, enabling centralized visibility.
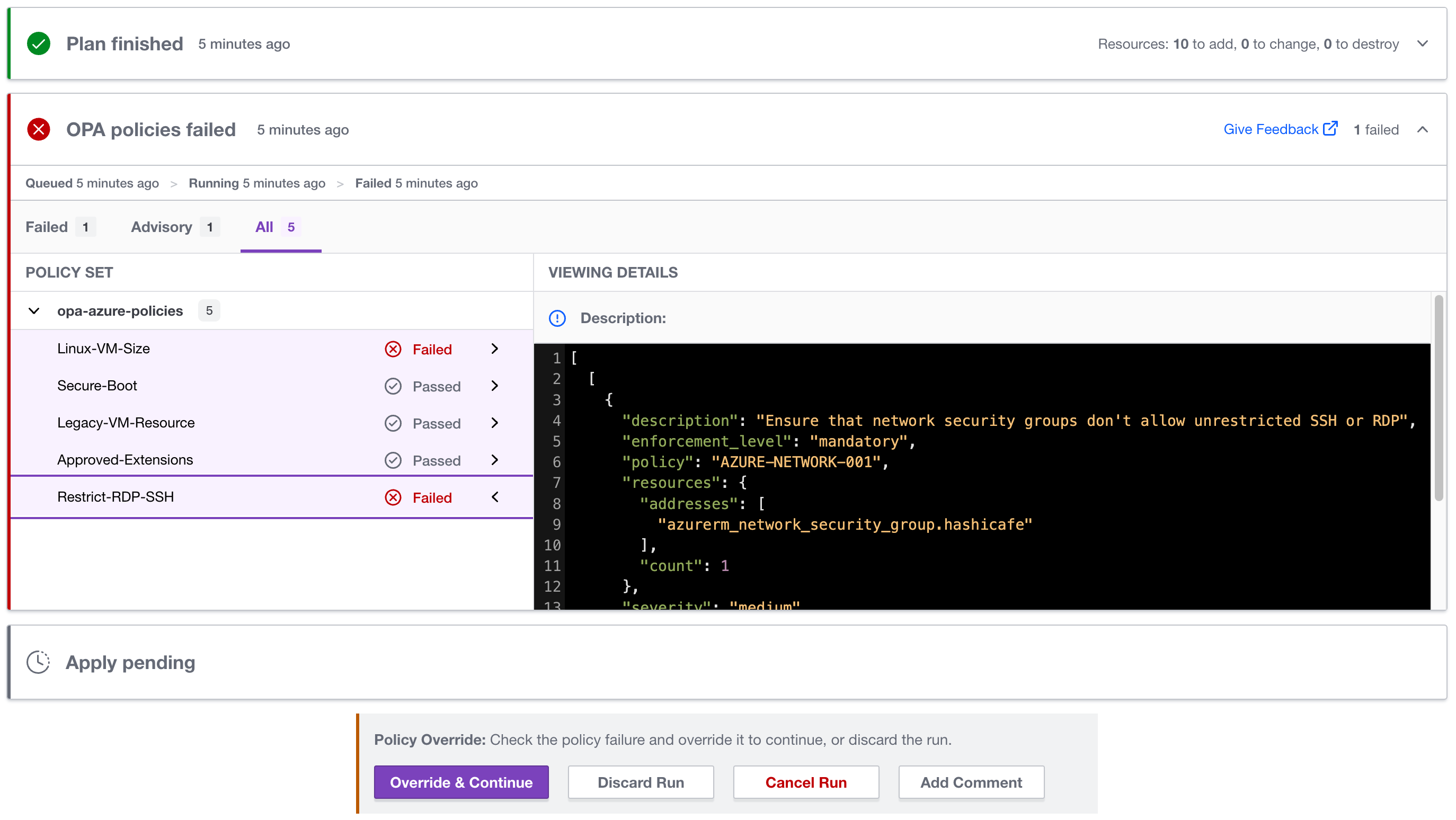
Native OPA support lets you see if your OPA policies have passed or failed within Terraform Cloud.
»Next Steps
Native OPA support gives users more flexibility to adopt a policy as code framework in Terraform Cloud. This integration helps simplify and accelerate policy enforcement workflows across multi-cloud environments.
To learn more about OPA support for Terraform Cloud, check out the documentation on Defining OPA Policies and our tutorial on how to Detect Infrastructure Drift and Enforce OPA Policies.
Get started with Terraform Cloud for free to begin provisioning and managing your infrastructure in any environment.







