We are excited to announce the release of dynamic provider credentials, a new authentication model now available in public beta for HashiCorp Terraform Cloud. Dynamic provider credentials help users create short-lived, just-in-time (JIT) credentials for HashiCorp Vault and the official Terraform providers for the major cloud vendors. This post discusses the benefits of dynamic vs. static credentials and reviews the details of the new authentication method.
»Credential Management Challenges
Terraform Cloud users typically use static credentials to authenticate with Vault and cloud providers, but this practice brings operational and security challenges. Managing these static, long-lived credentials does not scale well without manual effort. Users must set credentials as workspace variables or variable sets in Terraform Cloud, adding additional steps to their authentication workflow. Manual storage of static credentials introduces security risks, even if credentials are rotated regularly. Manual credential rotation also puts an operational burden on administrators. Users need a way to safely and efficiently authenticate to their cloud providers and Vault.
»Introducing Dynamic Provider Credentials
Terraform Cloud now supports dynamic provider credentials for Vault and official cloud providers. Dynamic credentials are temporary and time-bound, lasting from a few minutes to several hours. They are unique to each Terraform workload and are generated on demand, as opposed to static credentials, which are defined ahead of time and shared. Dynamic credentials do not require manual rotation or revocation when they are no longer needed.
»Standards-Based
The dynamic provider credentials feature is based on workload identity and implementation of the OpenID Connect (OIDC) standard. Organizations start by configuring Terraform Cloud as a trusted identity provider with their cloud platform or Vault. Terraform Cloud generates a signed identity token for every run. This token is exchanged with the provider to obtain temporary, short-lived credentials that are injected into the Terraform run environment. This exchange happens automatically for the supported providers by adding a few simple environment variables to the workspace.
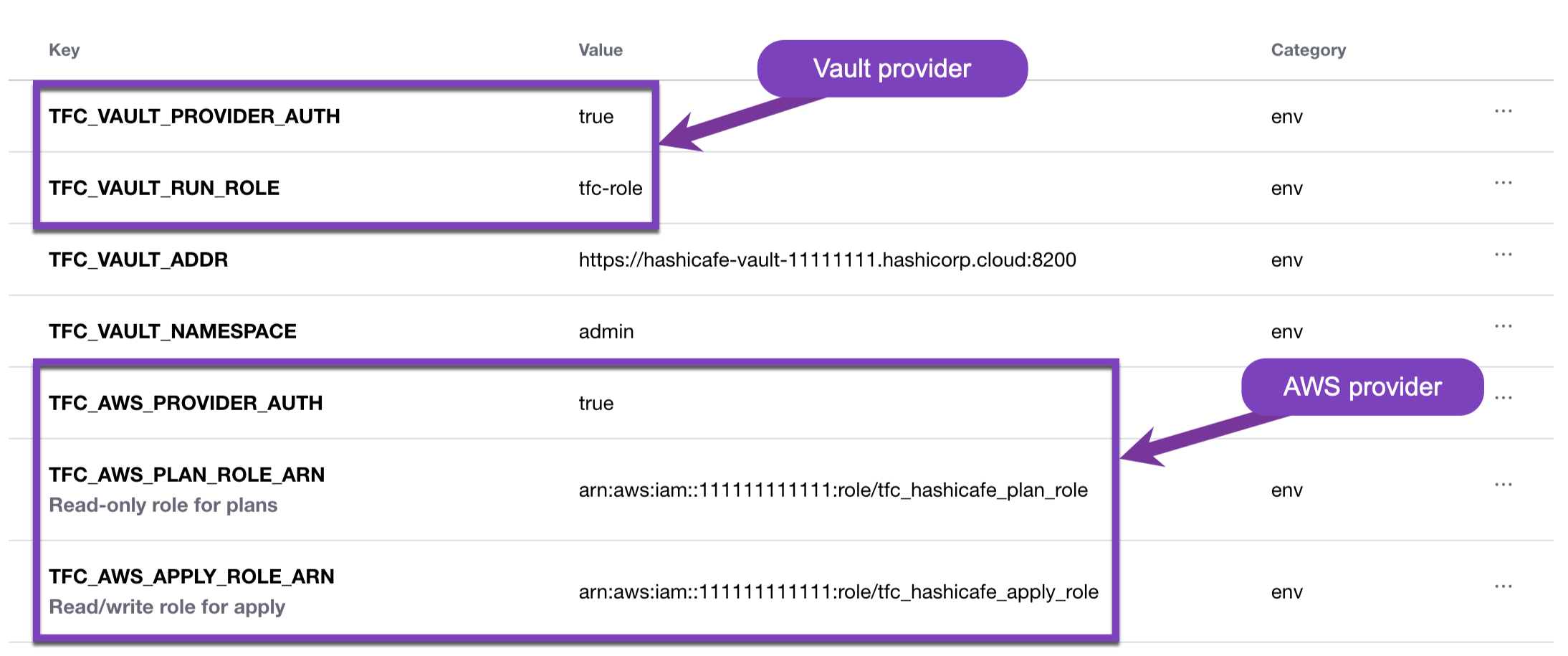
Workspace variables enable the dynamic provider credentials functionality
»Vault Provider
The Vault provider is the primary way users interact with Vault using Terraform. It allows users to configure Vault authentication methods, roles, and policies, and to write and access static secrets for workloads. Administrators need a simple and secure way to authenticate a Terraform Cloud workspace with Vault without having to manually rotate Vault credentials. Dynamic provider credentials for Vault allows administrators to give workspaces access to the exact secrets they need without exposing Vault credentials as workspace variables.
»Cloud Providers
Terraform Cloud dynamic provider credentials natively integrate with the Amazon Web Services (AWS), Microsoft Azure, and Google Cloud providers. Once an OIDC trust relationship is established, cloud admins scope roles with permissions appropriate to each workload. This eliminates the need for long-term API access keys or service principals and ensures that each Terraform Cloud run receives only the permissions it needs.
»Dynamic Provider Credentials Benefits
As users shift from static to dynamic credentials, a few key benefits emerge:
Reduced friction: Managing long-lived credentials requires custom solutions and processes that are typically taken on by the cloud platform team. Dynamic provider credentials remove the need to manage and store long-lived secrets in Terraform Cloud. Instead, temporary credentials are retrieved from a cloud platform on the fly, helping teams avoid the burden of manual secret rotation.
Reduced risk: Storing long-lived static credentials presents severe security risks, as cloud credentials are highly sensitive and can grant powerful privileges. Using temporary, short-lived credentials removes the need to store long-lived secrets in Terraform Cloud and significantly limits the impact of accidental credential exposure and reuse.
Granular permissions control: Dynamic provider credentials allow cloud platforms to scope privileges down to specific Terraform Cloud operations based on the run phase, workspace, project, or organization. For example, administrators can define read-only permissions for plans and write privileges for apply runs. This workflow helps keep permissions tightly scoped without manually managing and rotating credentials across many workspaces. This control gives users additional permissions customization and enables the least privilege principle.
»Get Started with Dynamic Provider Credentials
Dynamic provider credentials help organizations mitigate the security risks of storing long-lived credentials and avoid the operational burdens of manually rotating them. This helps simplify Terraform setup and ensures secure authentication across cloud environments.
To learn more about dynamic provider credentials, check out the documentation and tutorial. Sample code for all four integrations can be found in the setup examples repo on GitHub.
Get started with Terraform Cloud for free to begin provisioning and managing your infrastructure in any environment. And try HCP Vault, the easiest way to get started with Vault. Link your Terraform Cloud and HashiCorp Cloud Platform accounts together for a seamless sign-in experience.







