We are excited to announce the general availability of no-code provisioning, which gives organizations a self-service workflow in HashiCorp Terraform for their application developers and others that need infrastructure but don’t necessarily know Terraform or HashiCorp Configuration Language (HCL). Initially launched as a public beta at HashiConf Global 2022, no-code provisioning empowers cloud platform teams to set up their modules for push-button self-service, allowing stakeholders with infrastructure needs to deploy those modules without managing Terraform configuration repos or writing any code. This post reviews the details and benefits of this powerful new deployment method and also covers a handful of new features just released.
»New features in GA
During the beta period, we collected a lot of great feedback from customers, which led directly to new features that accompany the GA of no-code provisioning, including:
- Variable input dropdowns
- Variable set assignment to projects
- Project-level permissions scope
»Variable input dropdowns
During the no-code provisioning process, end users must input values for the variables in the module configuration that don’t have a default value. However, this can lead to frustrating provisioning failures due to typos or disallowed infrastructure attributes. Users asked for dropdown options to help avoid confusion around no-code workflows.
Now, admins can create guardrails for what attributes are applied to infrastructure. Module publishers can define the valid options for input variables via a page in the Terraform Cloud UI at the time of enabling the module version for no-code provisioning, or they can do the same via the TFE provider. After this is set, users can select from the pre-defined options during initial provisioning and subsequent updates to inputs on existing no-code workspaces. Examples of input guardrails include approved cloud regions, valid instance sizes, and expected values for metadata, like tags.
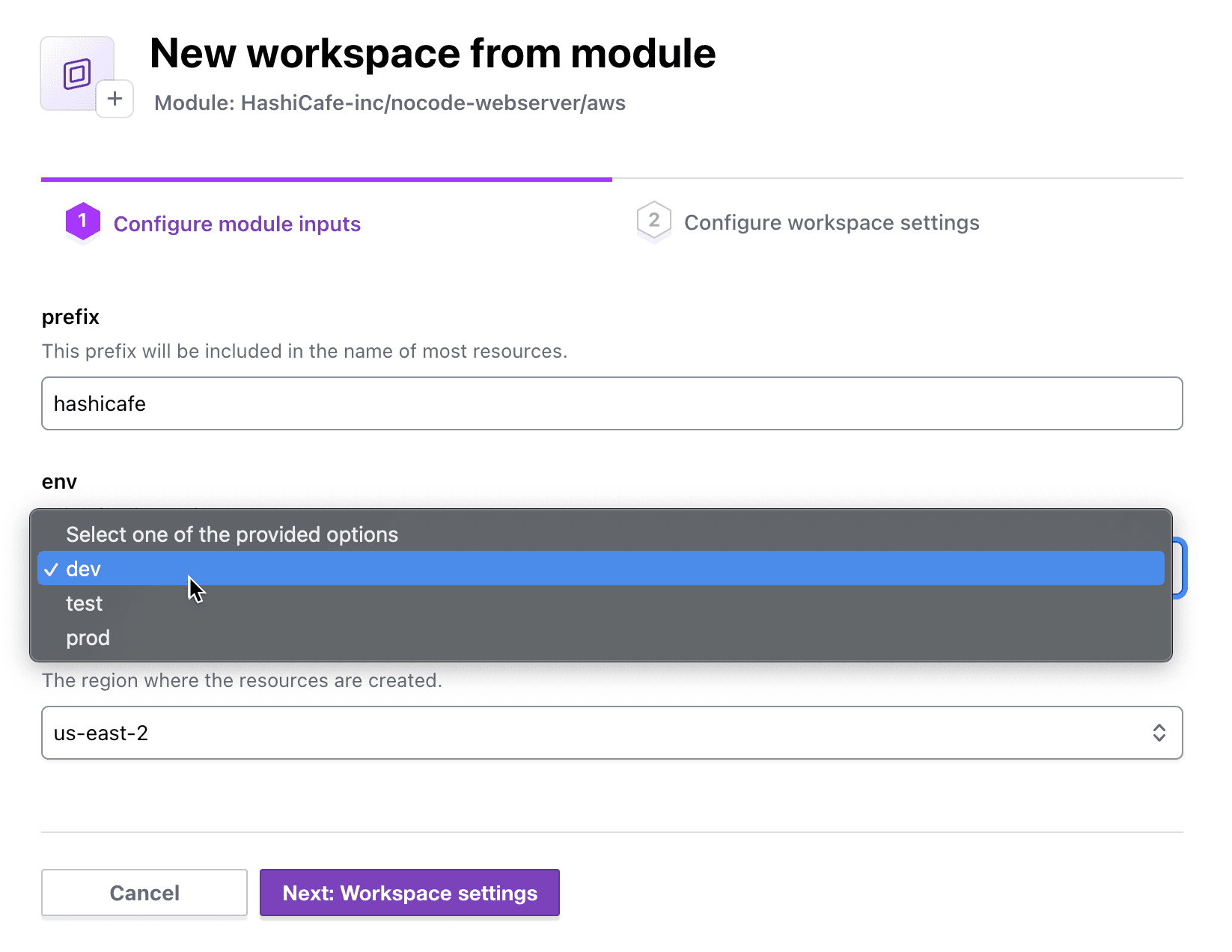
Variable input dropdowns allow no-code module consumers to choose from pre-approved values.
»Variable sets for projects
Previously, you could assign variable sets only with common inputs such as cloud credentials at either the global (organization-wide) or workspace level. This posed a conundrum for no-code provisioning, since the workspace is created at the time of first provision and many organizations need to assign granular cloud credentials for their no-code teams.
Since the introduction of projects as a new usage layer between organizations and workspaces, users can now add these teams to a project and define variable sets limited to only that project. New workspaces created by the no-code provisioning workflow will automatically inherit the variable set(s) assigned to the parent project.
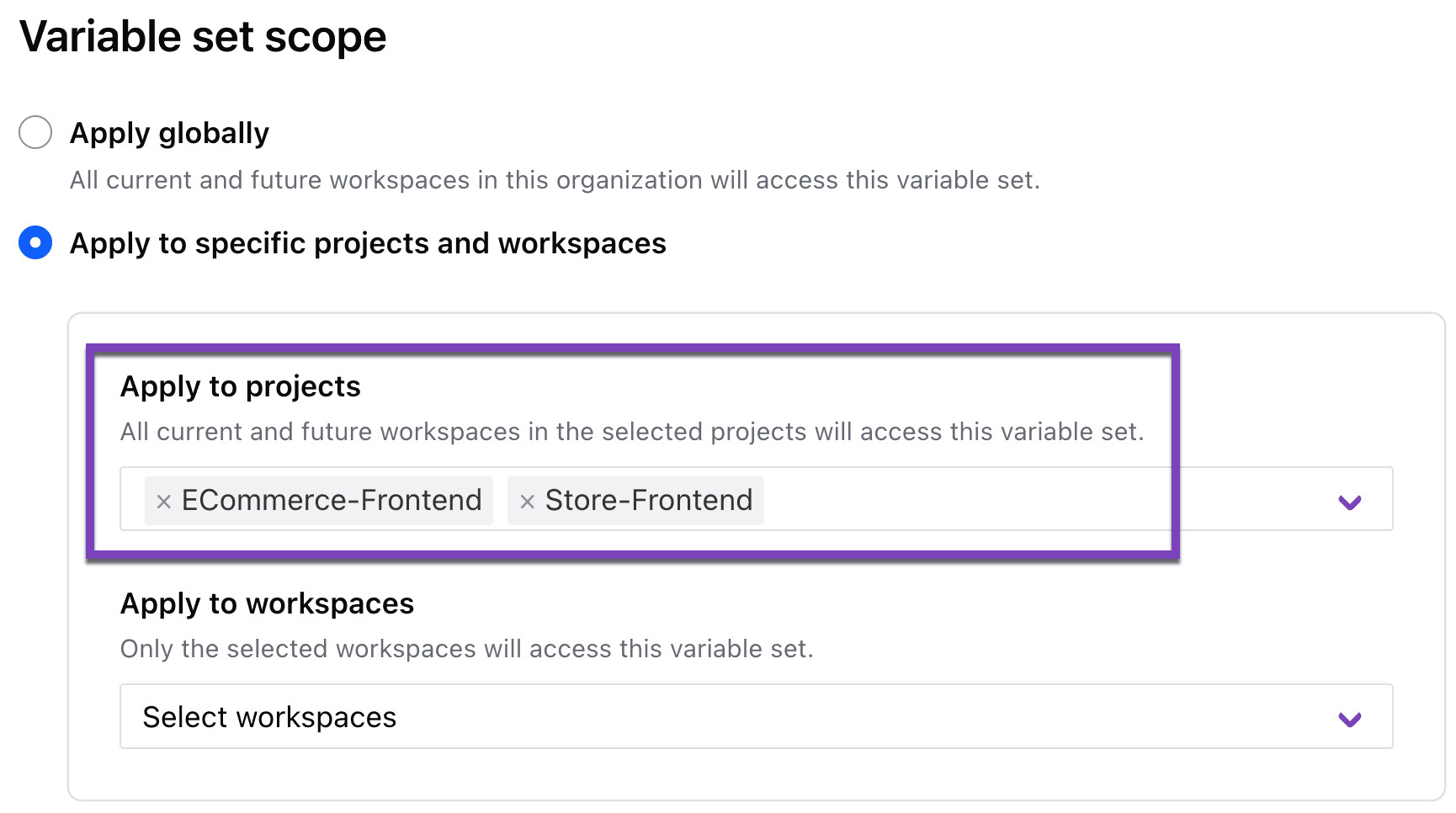
Variable sets can now be assigned to projects.
»Scope “manage workspace” permissions to a project
During the beta, no-code users needed the organization-wide “manage workspaces” permission. The introduction of projects in Terraform Cloud provided a solution to this problem.
No-code provisioning is integrated with projects, which means teams with project-level Admin or Maintain permissions can provision no-code ready modules directly into their project without requiring organization-wide workspace management privileges.
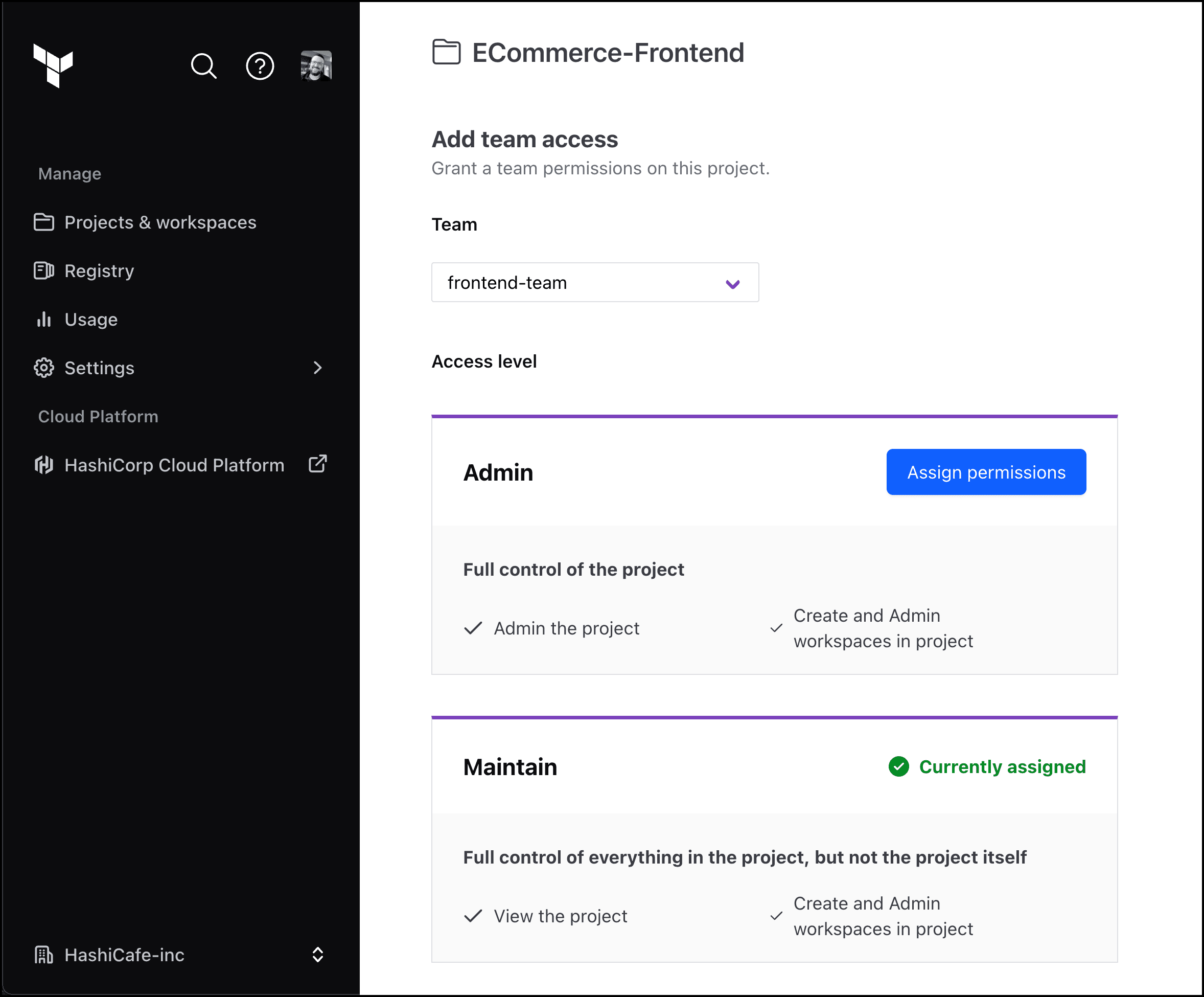
Teams with project-level Admin or Maintain permissions can provision new no-code workspaces into the project.
Here is a simple recommended workflow for setting up no-code-only users in a guardrailed project space:
- Organization admins should create projects for teams that want to self-serve no-code ready modules.
- Add the team to the designated project. Assign project Admin or Maintain permissions to the team at the time of adding it to the project.
- Then in the team’s general settings, make sure the team’s Organization Access is set to “No access” or “View workspaces only”.
»Key benefits
The general availability of no-code provisioning on Terraform Cloud allows cloud platform teams to provide self-service infrastructure without requiring any knowledge of Terraform or HCL from the user. Here are a few of the main benefits of this new feature:
- Increase productivity: Application developers, including those who do not know Terraform, can now provision a selection of infrastructure themselves. No-code provisioning provides a simpler, standardized way to provision with Terraform, bringing even more reusability and enabling faster provisioning velocity. With no-code provisioning, teams can spend less time defining configurations and more time supporting the business.
- Cost efficiency: Platform teams can now enable application developers in multiple business units to provision their own infrastructure in minutes, without significant Terraform training. Application developers can re-use approved no-code ready modules built with best practices to reduce over-provisioned resources.
- Reduce risk: Platform teams can control what infrastructure the teams they serve provision automatically. Administrators and module publishers can manage an allowlist of no-code ready modules for application developers to create workspaces, reducing failed infrastructure builds and costly misconfiguration errors. Project-level admins can maintain permissions in projects allowing application developers to access no-code ready modules without requiring organization-wide workspace-management privileges.
»Get started and try Terraform Cloud
Variable inputs, variable sets for projects, and managed workspace permissions are available today as generally available features. Learn more about no-code provisioning by reading the Designing No-Code Ready Modules documentation, hands-on tutorial: Create and Use No-Code Modules, and watching this demo video:
If you haven’t already, get started for free on Terraform Cloud to provision and manage all your infrastructure.









