Exposed secrets account for nearly 30% of all data breaches, with the average incident costing organizations $4.45 million. Despite heightened awareness, secret sprawl remains one of the most persistent and underestimated security risks.
API keys, tokens, and credentials govern how systems trust one another. When exposed, they allow attackers to operate with the permissions needed to quietly move across environments, clouds, and production systems. What starts as a single leak often becomes a chain reaction impacting multiple layers of infrastructure.
Understanding where secrets typically hide and how to detect them is the first step toward building a proactive security posture. Below, we examine the five most common sources of secret sprawl, how attackers exploit them, and what organizations can do to eliminate these vulnerabilities before they escalate into full-scale breaches.
»How attacks unfold: one exposed secret, multiple breaches
Most attacks don’t begin with ransomware or data theft – they begin with access. A typical sequence looks like this:
- Phishing or credential theft: Attackers gain access to a collaboration tool such as Slack or Jira
- Discovery of exposed secrets: Tokens or links lead them into repositories or CI/CD systems
- Lateral movement: Compromised credentials unlock databases, cloud services, or production workloads
- Impact stage: Data exfiltration, service disruption, or ransomware deployment
At the center of this progression is often the same root cause: a secret that was never meant to be exposed. This is why leading security teams are adopting a shift-left approach, identifying and remediating secrets early in the development lifecycle.
Secrets rarely leak from a single point. They sprawl across tools and workflows designed for speed. Understanding their origins is key to breaking the attack chain before impact.
»Source 1: Collaboration tools (Slack, Jira, Confluence)
What makes collaboration tools risky isn’t just the data they contain, but the trust they inherit. These platforms capture every exchange, from troubleshooting discussions, configuration notes, and environment details, creating a rich trail of context for anyone who gains access.
Secrets commonly surface when:
- Troubleshooting logs or credentials are shared in Slack messages
- Jira tickets contain code snippets or environment variables
- Confluence pages document setup steps with sensitive data
- Log files or configuration files are uploaded for convenience
Because these systems are designed for openness, not restriction, secrets shared in the moment often persist long after they’re needed. Attackers who compromise a single workspace can quickly map dependencies and move laterally across connected systems.
Risk: Collaboration tools are rarely integrated into secret scanning programs, yet they often store high-value, long-lived credentials that enable deep system access.
»Source 2: Code repositories (GitHub, GitLab, Bitbucket)
Repositories are the backbone of modern development, but also one of its most enduring sources of exposure. Under delivery pressure, developers frequently commit sensitive information by accident.
Common examples include:
- API keys or credentials left behind after testing
- Configuration files with embedded passwords
-
.envfiles accidentally committed to source control - Example or sample code promoted to production branches
Once a secret is committed, it rarely disappears. It propagates through forks, clones, pipelines, and backups, living in every branch and cache that touches the codebase.
Risk: Code repositories were never designed to manage secrets, yet they’ve become de facto storage systems for them. Without continuous scanning and automated remediation, repositories become easy targets for finding vulnerabilities.
»Source 3: Container images
Containers revolutionized delivery speed but also introduced new layers of hidden risk. Secrets embedded during image creation can get endlessly replicated across environments, often outside traditional visibility.
Typical exposures include:
- Hard-coded credentials in Dockerfiles
- Configuration files copied directly into images
- Environment variables defined during build instead of runtime
- Dependencies or package managers carrying embedded secrets
Because of container layering, deleting a secret later doesn’t always remove it. Older layers still contain the data, which can be extracted with simple inspection tools.
Risk: Every container image has the potential to distribute secrets organization-wide, amplifying risk each time it’s pulled, shared, or reused.
»Source 4: CI/CD pipelines
In a CI/CD pipeline, secrets are needed at many points to keep builds and deployments moving, leading to secrets duplicated across configs, scripts, logs, and tools over time. As those secrets spread, rotation and revocation become risky and slow, increasing the blast radius when a credential is exposed and turning a single mistake into a broader security incident.
Secrets often proliferate when:
- Credentials are embedded directly in pipeline configuration files
- Secrets are logged during build or deployment
- Shared templates replicate the same credentials across multiple projects
The result is a hidden web of dependencies where one leaked token can compromise dozens of applications or services.
Risk: CI/CD pipelines are the connective tissue of modern delivery. A single exposed pipeline secret can grant attackers privileged access across an entire ecosystem.
»Source 5: Cloud storage buckets (S3)
Misconfigured cloud storage remains one of the most frequent root causes of credential exposure. Secrets often end up in buckets or blobs as part of automated workflows that prioritize speed instead of oversight.
Common exposure paths include:
- Buckets left publicly accessible due to misconfigured permissions
- Backups containing
.envfiles or configuration data - Log exports with tokens or service credentials
- Application snapshots containing embedded secrets
Once an attacker discovers an exposed storage location, they can often extract both sensitive data and reusable credentials. From there, the compromise can expand into connected systems or cloud services.
Risk: Storage buckets often sit outside routine code or pipeline scans, leaving them unmonitored. Aligning secrets visibility across repositories, pipelines, and storage layers is critical to close this gap.
»From visibility to control
Reducing secrets risk requires more than periodic scans. Secrets don’t appear once; they move with code, artifacts, and infrastructure. Protecting them demands continuous visibility across the entire software lifecycle.
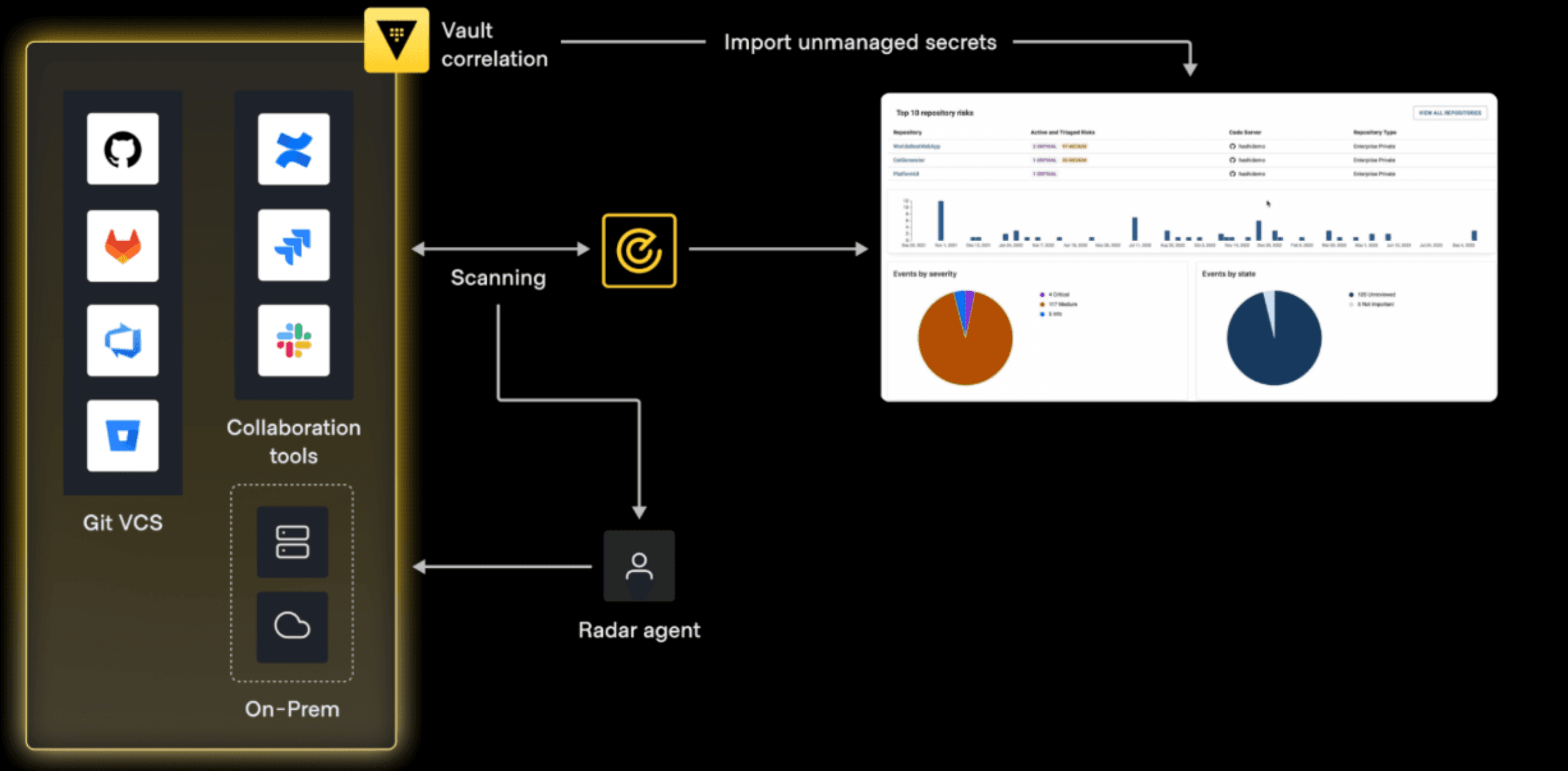
Traditional tools detect exposures after the fact. Products like HashiCorp Vault Radar are designed to surface exposed secrets in real time.
With Vault Radar, organizations can:
- Continuously monitor source code and CI/CD pipelines before secrets reach production
- Extend visibility to collaboration tools, logs, and file servers like cloud storage buckets where secrets are often shared under pressure or by accident
- Monitor runtime environments, identifying credentials wherever they persist
- Treat secrets as dynamic assets that are detected, prioritized, and managed throughout their lifecycle
This lifecycle-based approach shifts security from reactive cleanup to proactive control.
Organizations that adopt Vault Radar reduce breach risk by removing exposed secrets in real-time by:
- Limiting lateral movement by narrowing attacker access paths
- Improving operational resilience without slowing development velocity
Thousands of breaches begin with a single exposed secret. The organizations that prevent them aren’t responding faster; they’re seeing it sooner. Vault Radar enables that visibility, transforming secrets from a hidden liability into a managed credential through Vault.
»Start your free trial
Experience Vault Radar’s 30-day free trial to see how continuous detection transforms secrets management from reactive to proactive.