Organizations have invested heavily in secrets management, using platforms like HashiCorp Vault to centralize API keys, passwords, and certificates. These systems are critical for enforcing access controls, automating secret rotation, and meeting compliance requirements.
But there’s a gap: Secrets management only secures the secrets you already know about.
Even in well-managed environments, secrets can still end up scattered across code, repositories, pipelines, collaboration tools, and legacy systems. And, with the rise of AI-assisted coding, the attack surface is expanding in ways traditional controls weren’t designed to handle. Without visibility, these blind spots remain unmanaged, making them one of the most persistent and costly risks in modern infrastructure security.
When those secrets leak, organizations are slow to respond. Recent research found that the median time to remediate leaked secrets discovered in a GitHub repository was 94 days, more than three months in which attackers could exploit exposed credentials. The consequences aren’t theoretical. The 2024 Snowflake data breach underscored just how damaging unmanaged secrets can be.

How do you remove the blind spots of secret lifecycle management and give your teams visibility, detection, and guardrails that minimize secret exposure? This post looks at how secret scanning provides the final puzzle piece.
»How secret scanning complements management
Secret scanning extends the reach of secrets management products, by adding observability outside of the secret storage platform.
Secret scanners like HCP Vault Radar uncover the hidden secrets scattered across code, pipelines, infrastructure, and collaboration tools. These are the secrets that security teams rarely see, but attackers actively hunt for. Vault Radar enables security and development teams to gain:
- Full visibility into secrets, PII, and NIL across your environment, not just the ones you already track.
- Real-time awareness, detecting new secrets as soon as they’re introduced rather than months later.
- Remediation context that distinguishes between a dormant test key in a private repo and a production database password exposed publicly, so teams can prioritize remediation based on actual risk.
- Integration with Vault, ensuring that once a secret is discovered, it immediately becomes a managed asset.
»Building your secrets lifecycle strategy
A mature secrets program doesn’t treat discovery and management as separate steps, it weaves them into a continuous lifecycle.
- Detect: Continuously scan repos, pipelines, and infrastructure to identify unmanaged or leaked secrets.
- Notify: Alert teams in real time with the data and remediation steps they need to act quickly.
- Import: Bring discovered secrets into Vault for centralized security and governance.
- Clean up: Remove the exposed secret from code or config to eliminate the immediate risk.
- Rotate: Automatically rotate credentials to ensure they are short-lived, dynamic, and no longer exploitable.
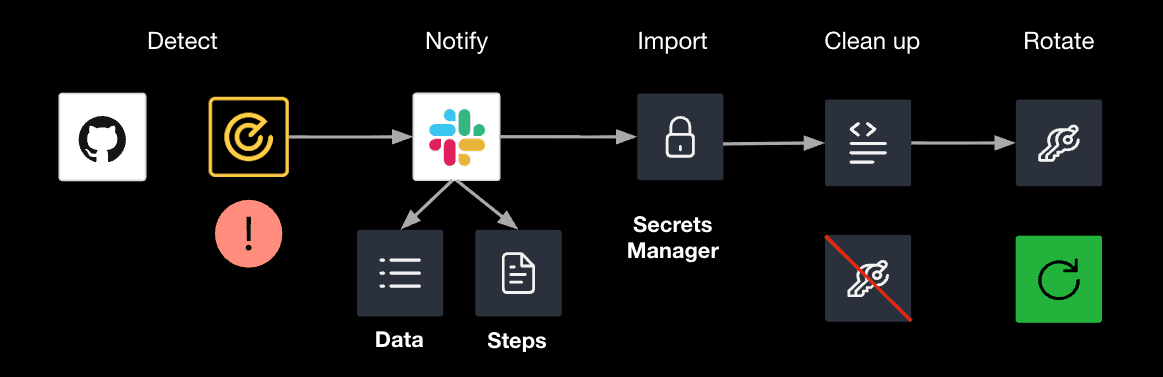
When scanning and management work hand in hand, the security and operational gains are tangible.
The most immediate impact is a reduced attack surface. Every hidden secret uncovered and secured removes a potential entry point for attackers. This visibility also builds audit and compliance confidence.
Operationally, automation replaces the grind of manual audits and fragmented processes, freeing security teams from repetitive work. And for developers, guardrails built into the process allow them to move quickly without sacrificing security, enabling speed with safety. Together, these outcomes create a security program that is both resilient and efficient.
»Closing the loop
On its own, secret scanning is just a spotlight. On its own, management is only partial control. But together, they form a complete, closed loop: uncovering what exists, securing what matters, and preventing secrets from slipping back into the shadows.
In today’s landscape, where attackers actively hunt for exposed credentials, ignoring secret visibility tools leaves a dangerous blind spot. By pairing the centralized control of HashiCorp Vault with automated secret scanning from Vault Radar, organizations can achieve end-to-end protection: find every secret, secure every secret, and never fall behind again.
Ready to see how secret scanning and management work together? Watch our secrets detection webinar to learn how Vault Radar together with Vault can provide you with complete visibility and control across your secrets landscape.
Want to quantify the costs associated with secret sprawl? Read our free eBook: The cost of secret sprawl and learn how leading organizations are tackling secret sprawl.








