We’re excited to announce the release of HashiCorp Boundary 0.10, now available for download as well as for use in HCP Boundary beta. Boundary provides identity-based remote access to infrastructure for individuals and teams at any scale.
The 0.10 release adds major new functionality to Boundary. Highlights include:
- Enhanced identity and access management (IAM) workflows in the admin UI: improved controls for granularly managing user permissions via Boundary’s admin UI.
- Support for worker tags in the admin UI: users can now use the admin UI to manage workers tags and control which worker proxies manage connections to targets.
- SSH key credential management: Boundary 0.10 enables users to seamlessly connect to machines remotely via SSH without having to manually enter their brokered credentials.
»Enhanced IAM Workflows in the Admin UI
Boundary exposes a number of identity and access management (IAM) resources, including users, groups, and roles, to configure access policies. A key concept in Boundary is the scope, which allows users to partition resources and set permission boundaries organized in a hierarchy.
Boundary 0.10 introduces enhanced IAM associations to the admin UI, allowing users to expand IAM associations in a project scope to resources such as group members and principals that reside in other scopes within Boundary.
While this functionality was previously available in the API and CLI, the Boundary admin UI supported IAM associations only for the given project scope. The enhanced workflow enables resource sharing across users who may reside in different scopes, opening new collaboration opportunities for teams.
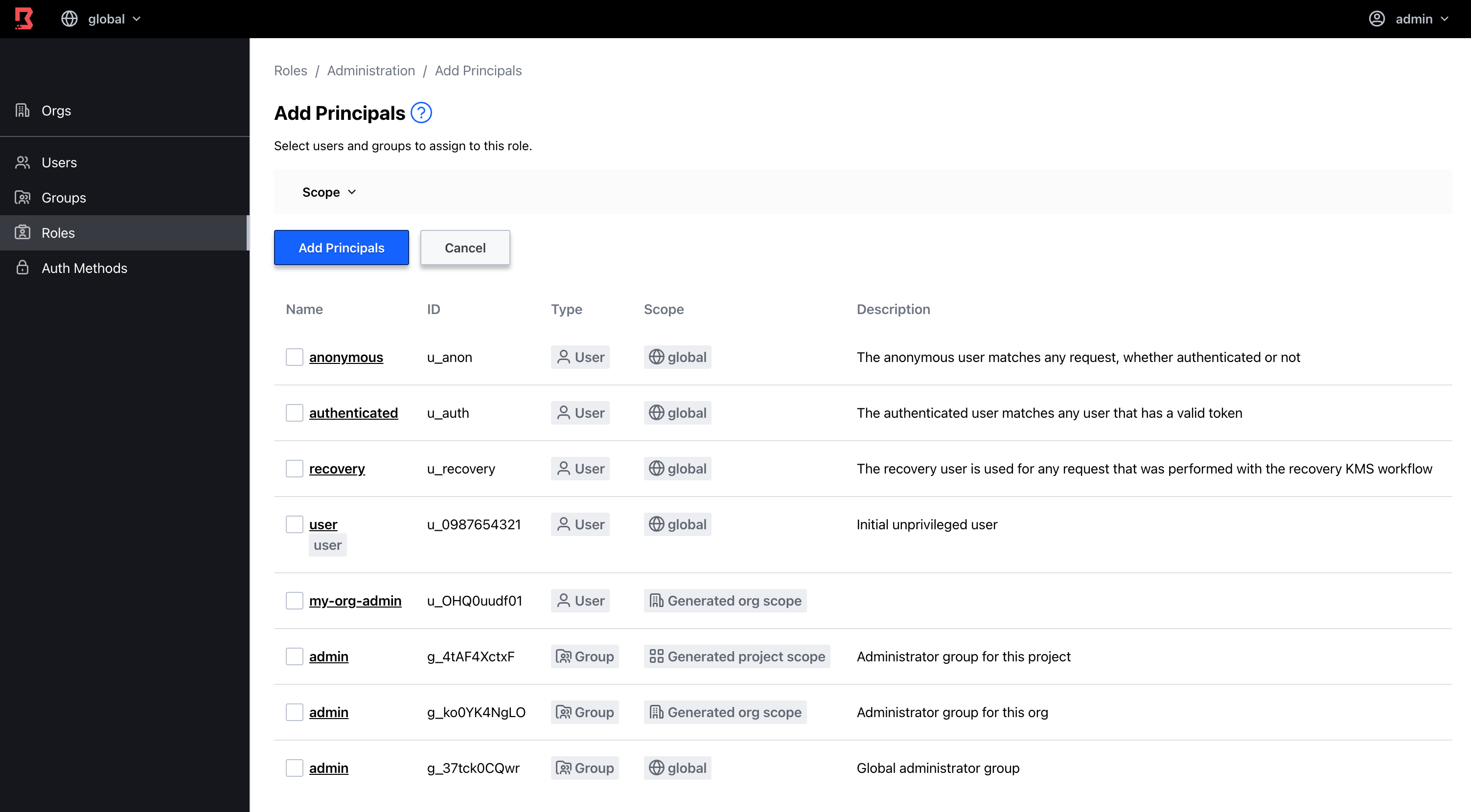
Boundary admin UI example for adding groups and users to roles
»SSH Key Credential Management
Boundary 0.10 includes enhancements to credential management, including added support for management of SSH private keys. SSH key support is included for both Vault credential stores and static credential stores. Additionally, 0.10 includes an SSH brokering helper function that allows users to seamlessly connect to machines remotely without having to manually enter their brokered credentials. Boundary users will be able to more easily establish connections to targets without having to constantly copy and paste credentials.
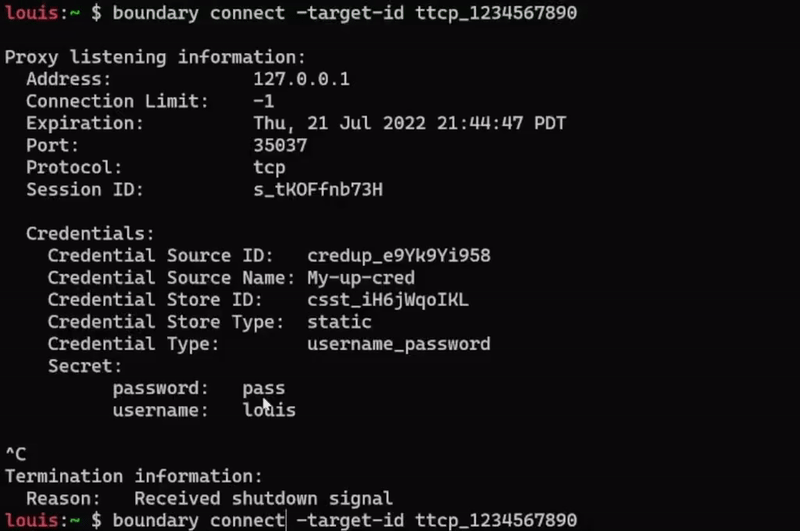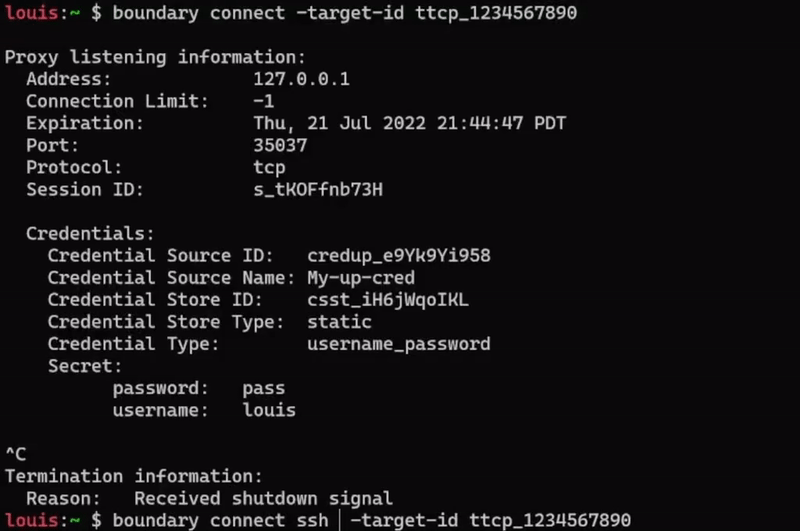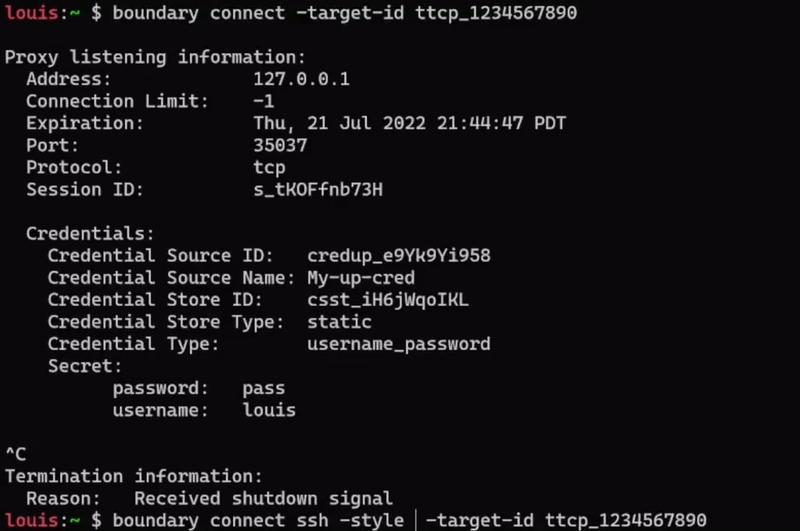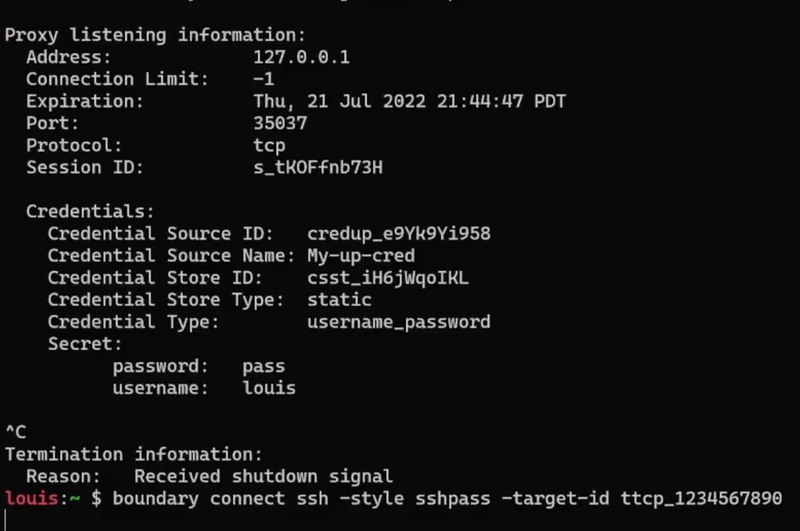
Example of passing brokered target credentials through SSH
»SSH Credential Injection (HCP Boundary Beta)
Both Boundary OSS and the HCP Boundary cloud service support the notion of credential brokering where a Boundary controller retrieves a credential from a credential store, and returns the credential back to the user. The user then has to manually enter those credentials to authenticate to their remote machine. As of 0.10, HCP Boundary now supports SSH credential injection, an active method of injecting credentials into an established connection, so that credentials are never exposed to users.
To get started, sign up for HCP Boundary for free and check out the HCP Boundary getting started tutorial on HashiCorp Learn. You can then try out credential injection with your HCP Boundary environment using our new ssh credential injection tutorial.
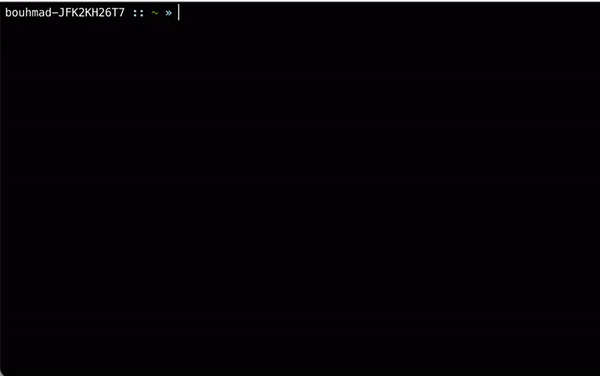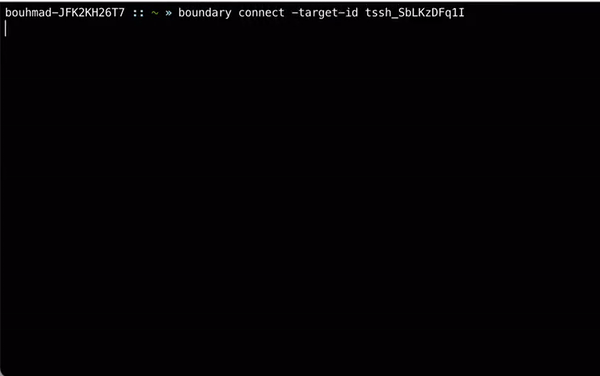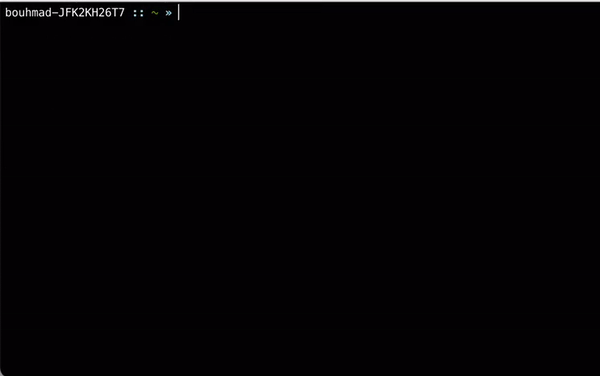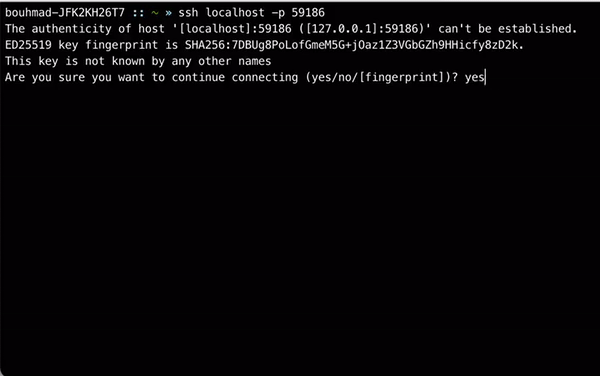
SSH credential injection for HCP Boundary
»Private Worker Upgrades (HCP Boundary Beta)
If you are planning to use self-managed workers with HCP Boundary in version 0.10 and above, you need to download the HCP-specific worker binary from the Boundary downloads page. The HCP control plane version must also be up to date with the workers, otherwise new features will not work. The control plane version can be verified in the HCP Boundary portal.
»Get Started with Boundary 0.10
- Download the Boundary 0.10 release.
- Sign-up for a free HCP Boundary beta account.
- Get up and running quickly with our Get Started with Boundary tutorial.









