We are pleased to announce the release of HashiCorp Boundary 0.2 and Boundary Desktop 1.0. Boundary provides identity-based access management for dynamic infrastructure. Boundary 0.2 focuses on meeting users’ production adoption needs.
This release includes several key features and improvements:
- OIDC authentication methods: Authenticate to Boundary with your external identity provider (IDP) of choice, including Azure Active Directory, Okta, and many others that support Open ID Connect.
- Boundary Desktop general availability on MacOS: Boundary Desktop gives users the ability to connect to remote targets and view active session details, all from a convenient macOS desktop application. Windows support will be added in a future update.
Given that Boundary 0.2 will be the first time many users evaluate Boundary since its 0.1 launch, it’s worth calling out some of the new capabilities that have been delivered since 0.1:
- Worker tags and filters: Enable target traffic to be effectively “tied” to a given set of workers with worker tags, forcing the session to occur through specified workers for a specific target.
- Boundary upgrades and database migrations: Boundary provides an easy upgrade path with fail-safes in the event of migration issues.
- Resource filtering and listing improvements: Boundary users can navigate their resources more easily by filtering list actions based on resource information.
- Improvements for Kubernetes access,
boundary connect kube: Run Boundary on Kubernetes and/or use Boundary to manage access to your Kubernetes APIs and kube services. - Boundary reference architectures: Learn how to deploy Boundary with reference architectures for popular platforms, including Kubernetes, Amazon Web Services (AWS), Microsoft Azure, Google Cloud, and Docker.
Boundary 0.2 also includes many additional minor features, improvements, and bug fixes. The Boundary changelog provides a full list of all changes.
»OIDC Authentication Method
One of the community’s biggest asks since Boundary’s launch is the ability for users to leverage external identity providers (IDPs) to log into Boundary. Boundary 0.2 adds support for OIDC authentication methods, which allow users to delegate authentication to an OIDC provider. This feature enables Boundary to integrate with popular identity providers like Microsoft Azure Active Directory, Okta, cloud identity management systems such as AWS IAM, and others.
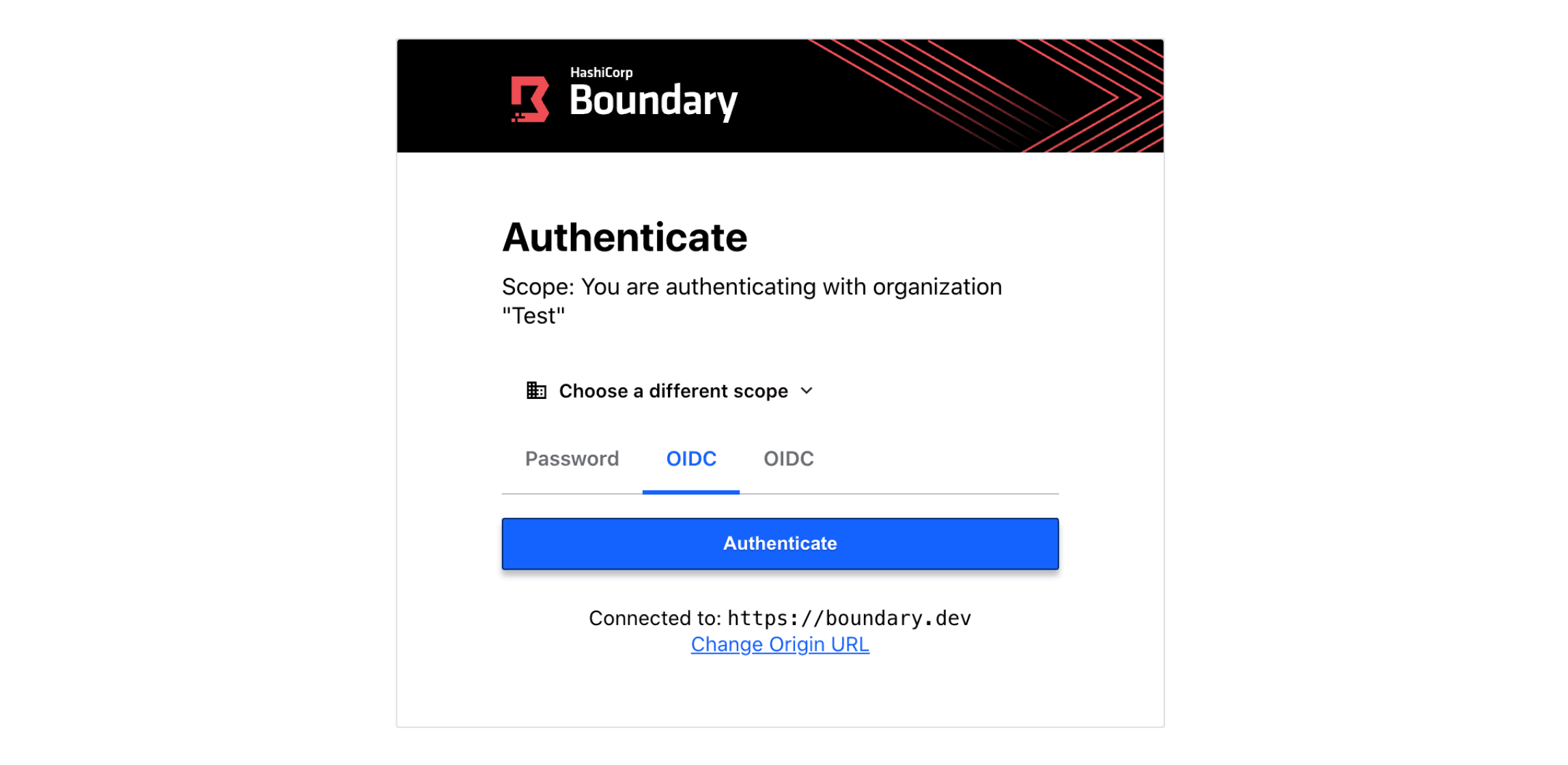
In this release, users can create, read, update, and delete a new OIDC authentication method resource and then use it to login via the CLI, Boundary Desktop, or the Boundary Admin Console. OIDC auth method configuration is initially available via the command line, and in upcoming releases we’ll also be integrating OIDC configuration into Boundary’s Terraform Provider as well as the Boundary administration console..
To get started with creating OIDC auth methods to log into Boundary with common OIDC providers, check out the new Boundary OIDC learn tutorial.
»Desktop Client GA
We would like to say a big thank you to everyone who tried out our beta release of Boundary Desktop for MacOS. We are excited to announce that Boundary Desktop is now generally available. In this initial GA release, we’re introducing some new features and bug fixes, including login via OIDC authentication and AutoUpdate for MacOS.
- OIDC login: Users can now login to Boundary Desktop with an OIDC identity provider.
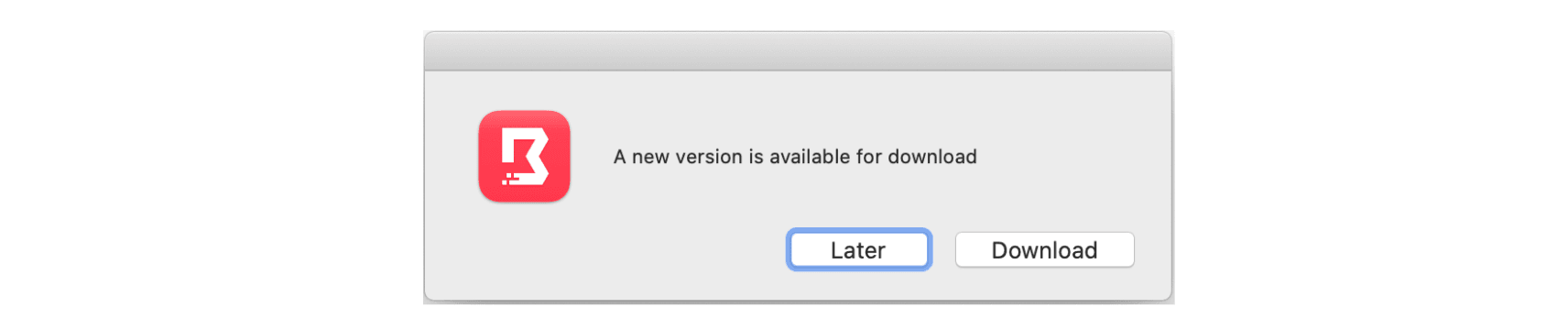
- AutoUpdate for MacOS: AutoUpdate the Boundary Desktop app as new versions become available.
Get started with Boundary Desktop here
»Upgrade Details
Boundary 0.2 introduces significant new functionality. Please review Boundary’s general upgrade guide and Release Notes for details.
As always, we recommend upgrading and testing this release in an isolated environment. If you experience any issues, please report them on the Boundary GitHub issue tracker or post to the Boundary discussion forum. As a reminder, if you believe you have found a security issue in Boundary, please responsibly disclose it by emailing security@hashicorp.com — do not use the public issue tracker. Our security policy and our PGP key can be found on the HashiCorp security page.
We hope you enjoy Boundary 0.2!









