The Principle of least privilege is a key tenant in information security. Every member of a team should have access only to the privileges required to complete their tasks at hand. As an organization using Terraform grows in size and complexity, using the Principle of Least Privilege becomes more critical. It can also become more difficult, as cross-functional teams begin to need access that pushes at the edges of the existing preset access levels.
That’s why we’re pleased to announce new Custom Workspace Permissions for Terraform Cloud. Terraform Cloud Organization owners can now specify custom permissions for each workspace using a newly designed and intuitive UI.
Previously, organization Owners had a limited number of workspace permissions to work with -- Read, Plan, and Write. Using Terraform Cloud’s new Custom Workspace Permissions, an organization Owner can now set granular permissions for a workspace’s runs, Sentinel policies, variables, and State Versions.
»Mixing & Matching Permissions
Customers have shared with us their needs to scope back certain access levels for different workspaces. Quite often even the non-sensitive variables that are set on a production workspace just don’t need to be exposed to non-admins. There’s no inherent security risk in letting trusted team members see them, but in the interests of consistency in applying the principle of least privilege wherever possible customers have wanted to provide more fine grained access than our previous “Read”.
Now you can create customized permission that grants read access only to “runs” while explicitly setting the permission to “no access” for workspace variables.
»Restricting Access to State Versions
A long standing request from a lot of customers, especially in regulated environments, has been to add the ability to restrict access to State and State Versions. We’ve now got a permission that helps with restricting that.
»Setting Customized Permissions
To set your own customized permissions for a workspace, go to the Workspace and click Settings > Team Access. Select the team you wish to manage the permissions for, and within it you’ll see a new option to toggle “Customize permissions for this team”. That will switch between selecting from the preset permissions you’re possible familiar with to the new fully customizable permission groups.
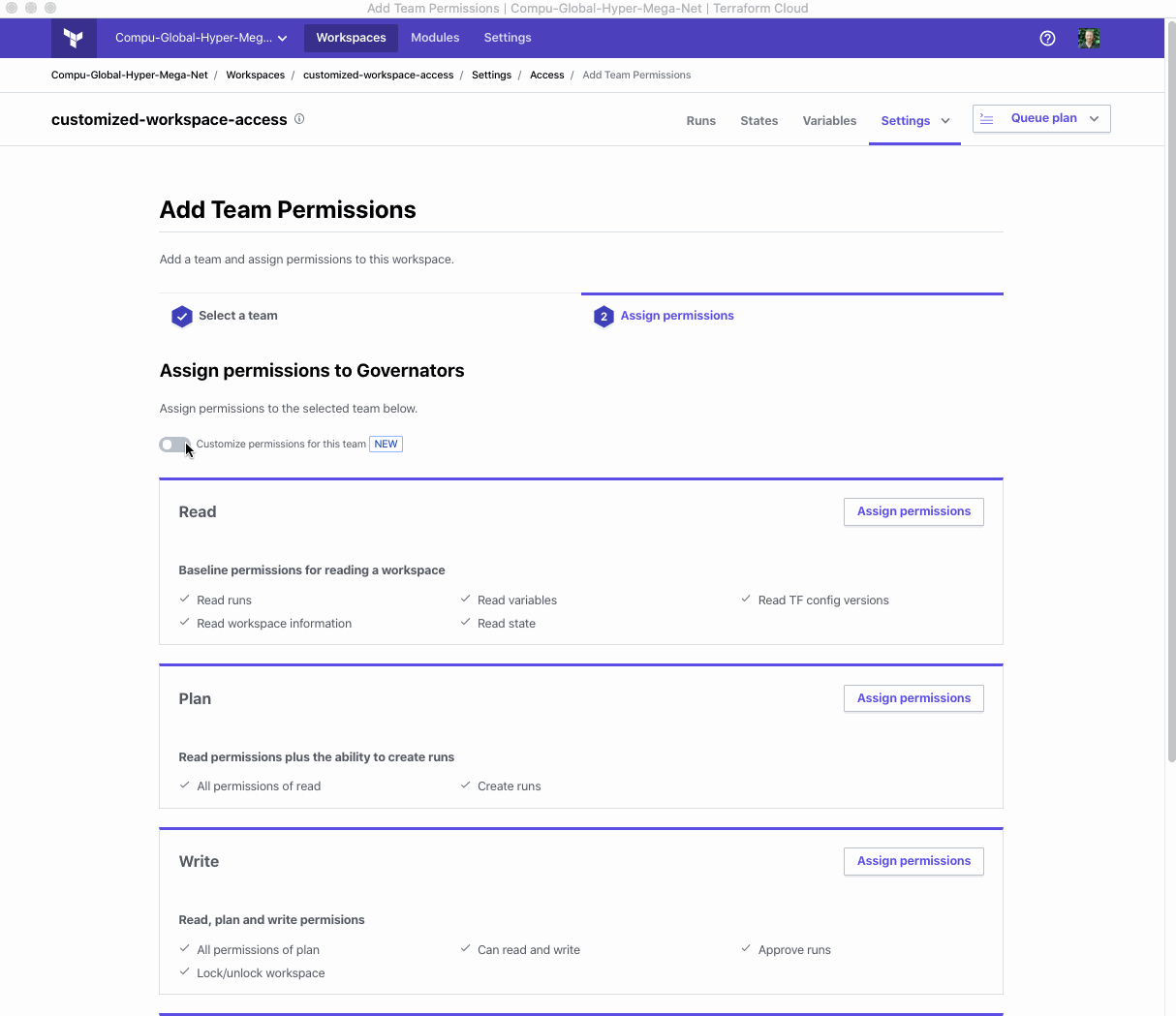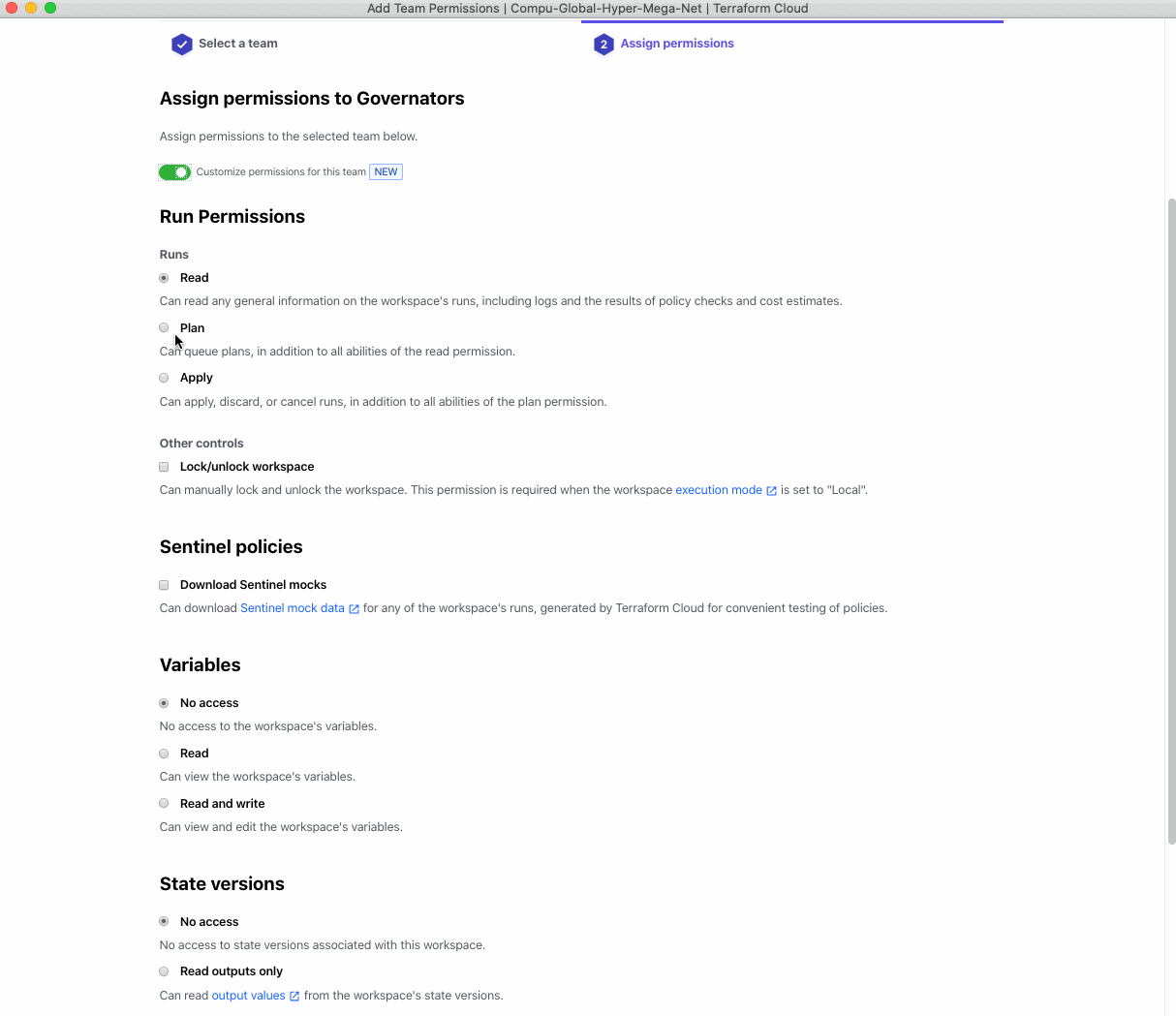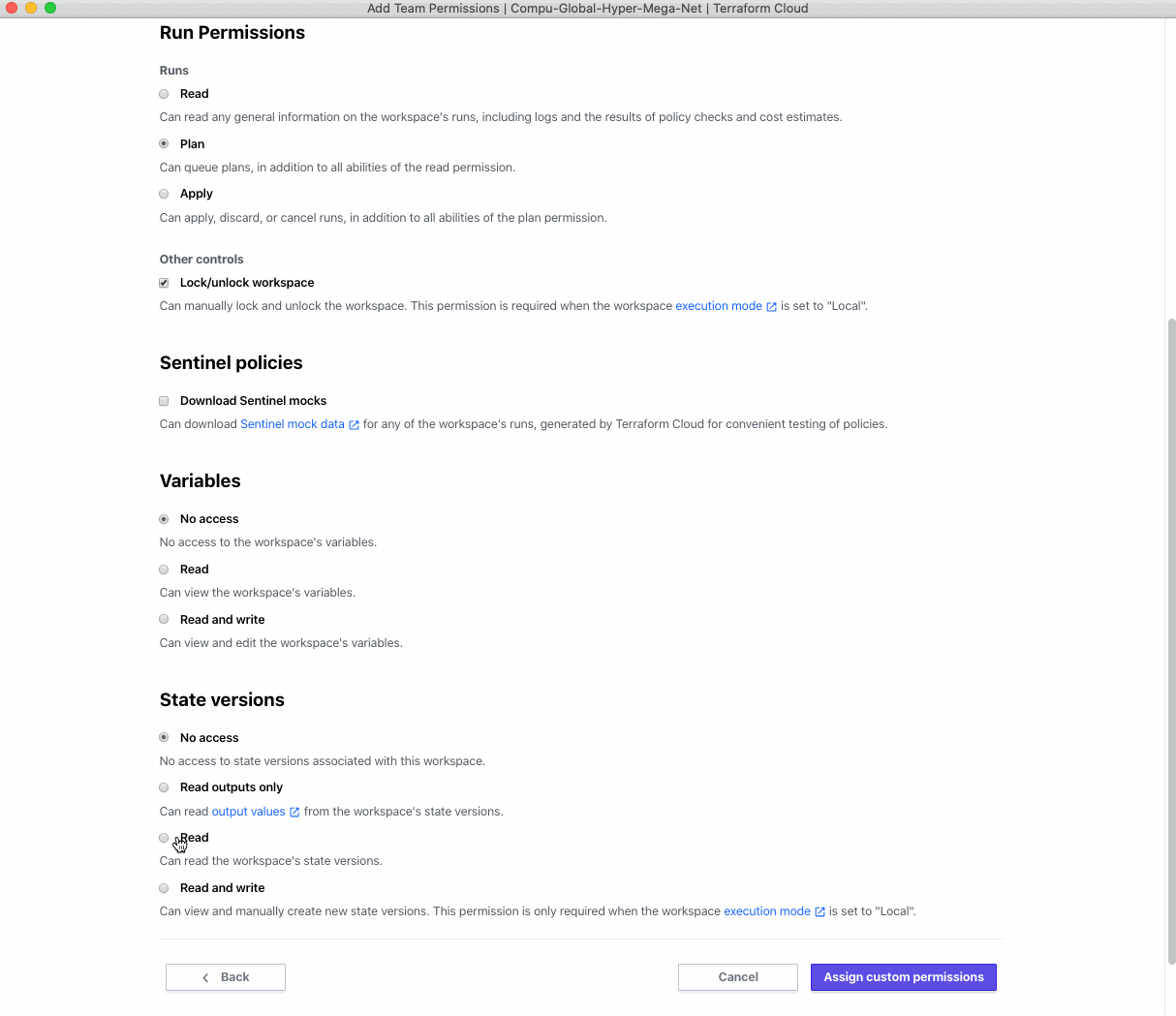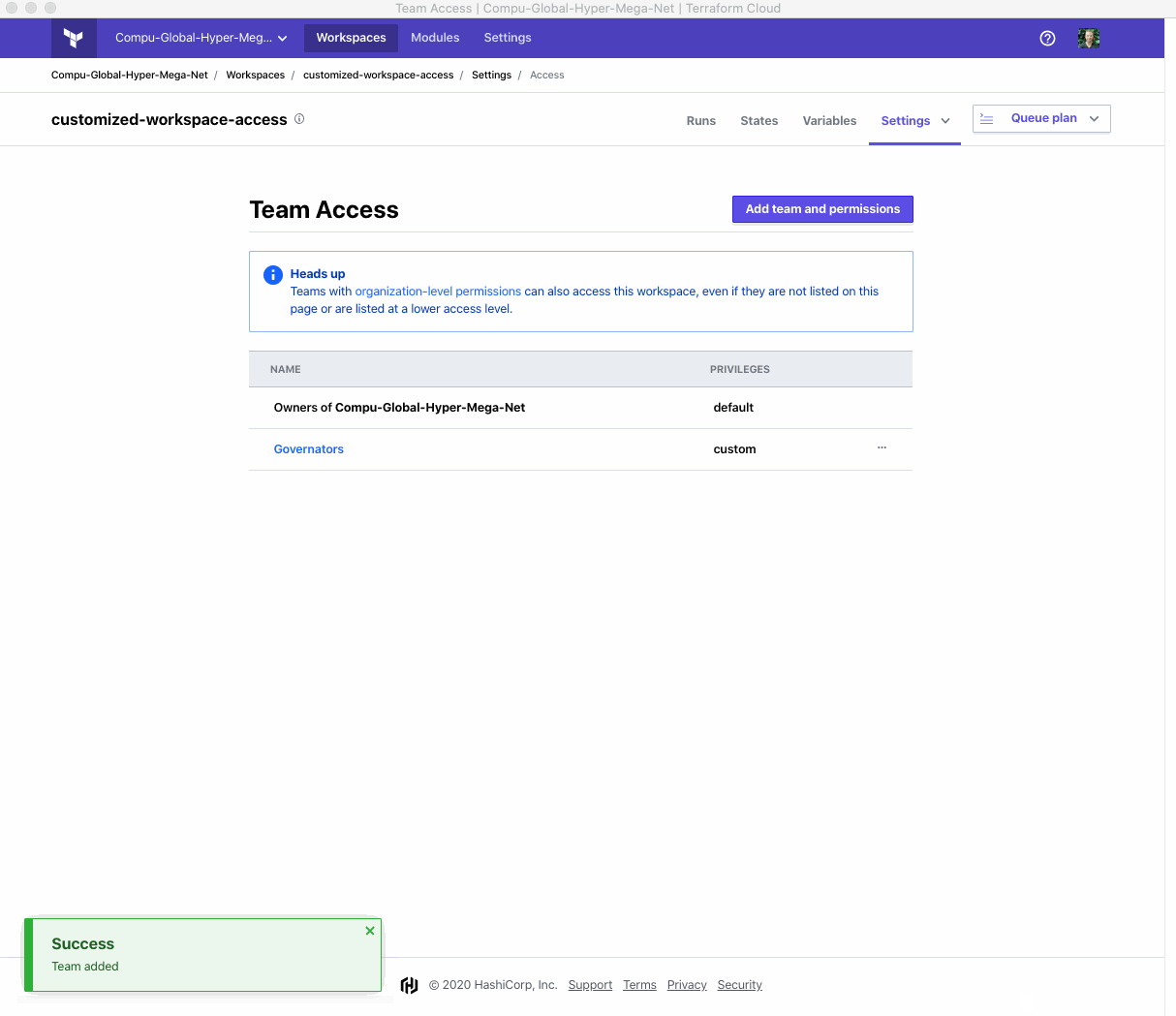 (Navigating through the settings and setting custom permissions)
(Navigating through the settings and setting custom permissions)
»Security Considerations
It’s important that we point out that this new capability is only a small part of what is required to holistically solve the challenges around managing infrastructure state, and needs to be incorporated as part of a larger defense in depth approach. It is specifically addressing the problems customers had highlighted with well intentioned team members, who didn’t need access to state day-to-day, still having incidental access to potentially sensitive infrastructure configuration detail. That in turn increased the operational burden for the teams having to regularly audit and report on such issues. This doesn’t prevent an individual with malintent from intentionally exfiltrating state information into log output or saving the results onto a different system. Terraform itself continues to have access to the state, and sensitive variables, during the process of executing a run. So we continue to advise that customers compliment this additional feature with strong oversight and CI/CD processes, as well as limiting access to Terraform Cloud workspaces to only trusted individuals within your organization.
»Getting Started
This feature is available to any organization on a Terraform Team plan or higher, and can be turned on with the flip of a toggle switch. To learn more and get started, please check out the documentation on Custom Workspace Permissions.








