GEICO is a juggernaut in the US insurance industry, with an IT infrastructure team that has profoundly transformed its digital architecture over the past decade. Here’s a snapshot:
- 2013: 100% on-premises, the CIO decides to go all-in on public cloud
- 2020: 80% public cloud, distributed across 8 clouds, applications still have to use databases with a client-server model that's “calling back to the closet of IT in the back room”
- 2022: Cost structure is 3x higher with 200K cores of compute, 30K+ VMs; they’re spending $300M+ on infrastructure, but developer productivity is down, and they’ve lost two 9s of reliability
- 2026: Reduced cost to serve, increased portability, improved data quality for eventual AI initiatives, and simplified infrastructure through standardization and centralization
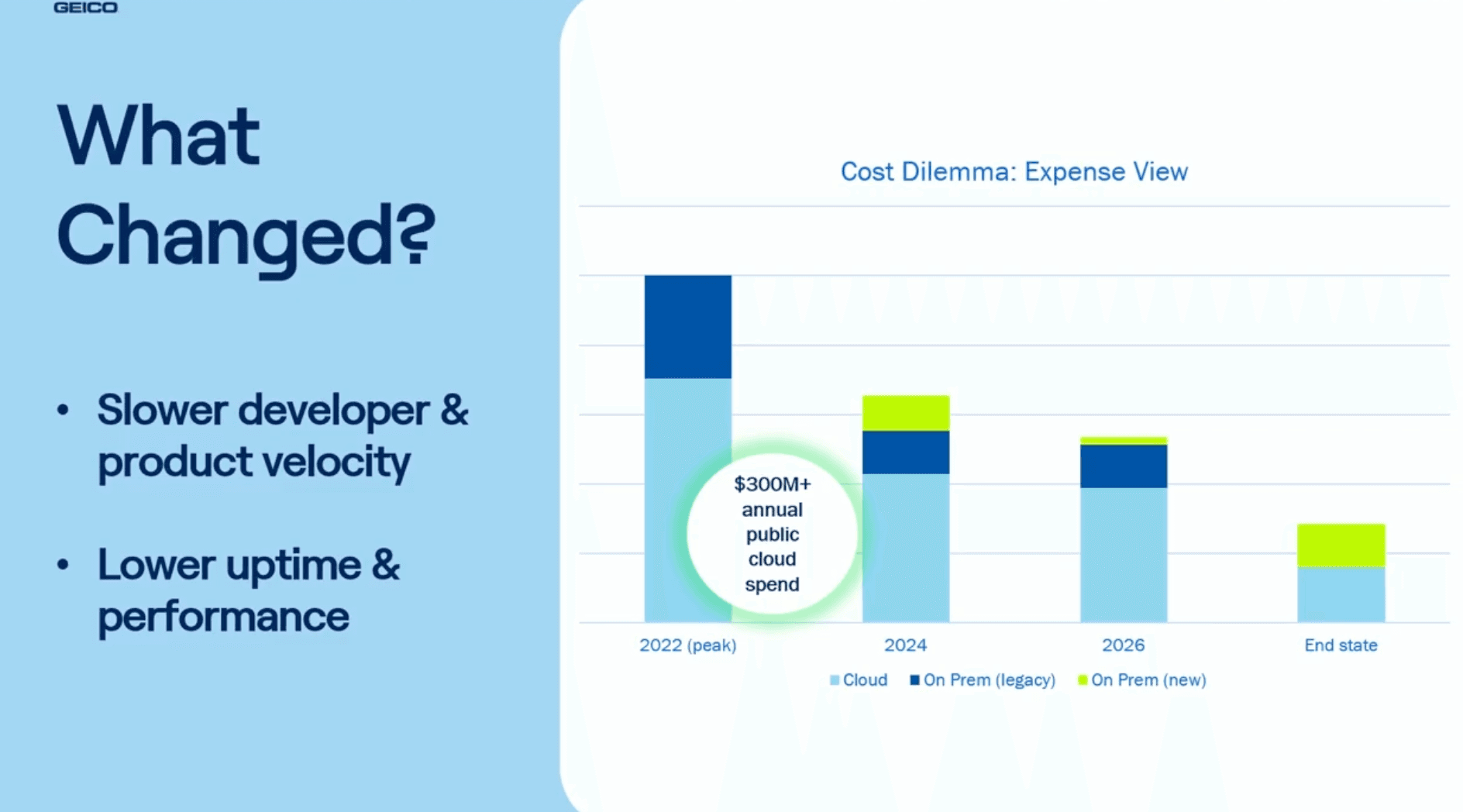
GEICO's cost reduction results and estimations chart.
This is a common journey for enterprises: A lack of standards as you grow the surface area of your cloud for things like network access controls, user authentication, etc. isn't uncommon — just take a look at the recent Cloud Complexity Report.
“Every datacenter was configured differently. Every cloud provider was configured differently. And we have about 30 years of one-offs.”— Ammar Zuberi, Distinguished Infrastructure Engineer, GEICO
So how did GEICO finally set itself on a path to do cloud right and build the right foundation for AI?
This post, based on a talk from HashiConf, outlines the important hybrid cloud management lessons GEICO learned and how HashiCorp Vault played a major role in building its new infrastructure platform.
»Stop securing the network, start securing identity
GEICO’s Rebecca Weekly (VP, Infrastructure Engineering) and Ammar Zuberi (Distinguished Engineer, Infrastructure) explained one of their teams’ first observations: many of their woes were a result of their legacy, network-centric security model.
For decades, GEICO — like many enterprises — used the network to enforce security. Firewalls, VLANs, and point-to-point rules dictated who could access what. That approach worked when infrastructure was static. It breaks down fast in hybrid and multi-cloud environments.
Using the network as a comprehensive security perimeter created fragility, slow change cycles, and security blind spots. There was no single end-to-end view of access or posture, and every change required coordination across teams and vendors.
Their solution: move security up the stack and enforce policy as close to users and workloads as possible.
“We decided that the network only has to do one job, which is move packets from point A to point B. We should do security at higher layers in our network, so we decided that we're going to make our network as simple as possible.”— Ammar Zuberi, Distinguished Infrastructure Engineer, GEICO
They started to shift away from their legacy network security model and adopted a new approach that involves:
- Enforcing policy at the platform and workload layers, tied to identity
- Certificates and identity from an IdP, enabling their new identity-first security approach
- Segmenting traffic at the workload level instead of the network level
"We could move these security requirements into the platform layers where you could get much more granular about what policies you were allowing and what kind of access was allowed. ... As far as security goes, as a workload owner, you're optimizing for a business process. You don't need to care as much about security." — Ammar Zuberi, Distinguished Infrastructure Engineer, GEICO
“Make your policy as close to your user or your workload as possible. That is the only way to scale. Period. Full stop.” — Rebecca Weekly, VP, Infrastructure Engineering, GEICO
Not only did this shift modernize their security posture, it also made the network more reliable and the workload deployment experience much better.
»Centralize identity and secrets to regain control
Once GEICO stopped relying on the network for security, identity became the control plane.
That meant rethinking how secrets, certificates, and workload identities were created, distributed, and governed across a sprawling hybrid cloud environment.
Before this shift:
- Certificates were often handled manually
- There was no consistent certificate management strategy
- Access through a VPN was broad and tied to network location rather than identity
HashiCorp Vault became a keystone of GEICO's new security model, providing an organizationally consistent way to manage secrets and identities across on-prem and multi-cloud environments.
“We use workload identities, certificates, things like that that we got out of HashiCorp Vault to centralize authentication, policy enforcement, and the management of those secrets.”— Ammar Zuberi, Distinguished Infrastructure Engineer, GEICO
Just as importantly, Vault brought standardization to their security practices.
“It forced us to standardize our access policies into a single place where we could actually reason about them.”— Ammar Zuberi, Distinguished Infrastructure Engineer, GEICO
»Build vs. buy
GEICO started its Vault adoption with Vault community edition, but quickly realized that spending time building more features on top of that, which they needed to meet regulations, was going to involve too much time and money spent on features that didn’t differentiate their business:
“'We're going to build it all ourselves. We can do everything.' And then what we found in the process was that there were requirements for auditors in different domains that we could have built, but it probably would have taken us N months, and we needed to be compliant today. And that was really the outcome around controlling our own destiny and making the right decisions for us as a business. So we made the decision to move forward with HashiCorp’s version of Vault, and that allowed us to get these features out of the box versus having to build them for ourselves.” — Ammar Zuberi, Distinguished Infrastructure Engineer, GEICO
These out-of-the-box features that GEICO needed included:
- Integrated FIPS compliance
- Multi-region, high-availability Vault cluster replication
- Automated snapshots for disaster recovery
- Namespace and tenant isolation to manage secrets across multiple teams or business units
- Integrated HSM support for compliance-critical encryption
- Logging, monitoring, and security data needed for audits in one central place
»Building a foundation for the AI era
GEICO is currently in the middle of its five-year transformation, which includes:
- Re-architecting six physical datacenters
- Overhauling 350 edge sites (regional offices and field agents)
- Migrating off bespoke mesh topologies without disrupting the 24/7 business
Decoupling the network and most security functions made it possible to start doing this without major disruptions to the end users. The resulting efficiency so far has allowed GEICO to shift investment from ‘keeping the lights on’ to building value that makes their agents more effective and their customers' lives better.
By standardizing identity, secrets, and access controls across environments, GEICO created the flexibility to place workloads where it made the most sense — based on cost, performance, or future needs like AI.
“Part of getting foundational identity security and network correct is to be able to enable your AI revolution. That was a critical element: how can we reduce our cost to serve and increase our portability, improve our data quality so that we can unlock AI to make our agents that much more effective, that much more productive?” — Rebecca Weekly, VP, Infrastructure Engineering, GEICO
At HashiCorp, we’ve worked with thousands of organizations to help them through their digital transformations. Read what we’ve learned about modern security, and don’t hesitate to get in touch if you’re also in need of a foundational transformation in preparation for AI development and adoption.
Watch the full session on GEICO’s journey here: