Announcing HashiCorp Nomad 0.11 Beta
We are excited to announce the availability of the beta release of HashiCorp Nomad 0.11. Nomad is a simple and flexible workload orchestrator that enables organizations to easily deploy and manage containers and non-containerized applications at scale. Nomad is widely adopted and used in production at organizations like PagerDuty, Target, Trivago, and more.
Nomad 0.11 delivers a set of new features including extensible, pluggable storage volumes and autoscaling to enhance its core orchestration capabilities. For enterprise customers, audit logging brings administrative visibility and operational traceability to fulfill compliance requirements.
Key highlights of this release:
- Container Storage Interface (CSI): Deploy stateful applications on Nomad using storage volumes from any third-party provider of choice. Read more here.
- Autoscaling: Dynamically scale application instances based on real-time load or business SLAs without manual intervention. Read more here.
- Task Dependencies: Define and run interdependent workloads in sequence. Read more here.
- Remote Exec (UI): Directly execute commands in a running allocation through the Nomad UI. Read more here.
- Audit Logging (Enterprise): Provide administrators with a complete set of records for all user-issued actions in Nomad. Read more here.
»Container Storage Interface (CSI) BETA
Deploy stateful applications on Nomad using storage volumes from any third-party provider of choice. Users can now run applications that use storage volumes from AWS Elastic Block Storage (EBS), Elastic File System (EFS), GCP persistent disks, Digital Ocean droplets, or any other third-party provider using CSI plugins.
job "plugin-aws-ebs-controller" {
datacenters = ["dc1"]
group "controller" {
task "plugin" {
driver = "docker"
config {
image = "amazon/aws-ebs-csi-driver:latest"
args = [
"controller",
"--endpoint=unix://csi/csi.sock",
"--v=5",
]
}
csi_plugin {
id = "aws-ebs0"
type = "controller"
mount_dir = "/csi"
}
Nomad 0.11 introduces a new csi plugin stanza, with Controller Plugins for communication with each storage provider's APIs and Node Plugins to execute the tasks on each client node. Once the CSI plugins are running, users can then register their storage volumes with the nomad volume register command.
With CSI, users will now be able to freely add and remove storage volumes from their cluster without needing to manually change their Nomad client configurations. In addition, CSI plugins from providers written for Kubernetes will work for Nomad out of the box.
»Autoscaling TECH PREVIEW
Dynamically scale application instances based on real-time load or business SLAs without manual intervention. Available as a tech preview today, the autoscaler arrives as a separate, add-on component to Nomad for extensibility and performance. At a high level, the autoscaler retrieves policies stored in Nomad, queries metrics from an APM, and then taking a scaling action based on the defined strategy.
job "web-app" {
group "example" {
scaling {
enabled = true
min = 1
max = 10
policy {
source = "prometheus"
query = "scalar(avg(haproxy_server_current_sessions))"
strategy = {
name = "target-value"
config = { target = 20 }
}
}
}
This tech preview starts with horizontal application autoscaling (scaling up and down of application instances) and support for Prometheus as the first APM. Over time, the autoscaler will grow to support cluster autoscaling and mature into a plugin-based system with broad APM support and freedom for users to author their own autoscaling strategies.
Autoscaling is being released as a tech preview feature, which means that it may not be functionally complete and we are not providing enterprise support for Nomad Enterprise users using autoscaling in production. We’re excited to release this new architecture with the community to gather feedback, and will officially add it to our support for Nomad Enterprise after the feature is generally available.
Watch the autoscaler preview video from Nomad Virtual Day and read the feature blog to learn more.
»Task Dependencies
Define and run interdependent workloads in their sequential orders. With the introduction of lifecycle hooks, Nomad users can now run initialization and sidecar tasks to achieve intra-application and inter-service deployments.
task "init-service" {
driver = "docker"
resources {
cpu = 200
memory = 128
}
lifecycle {
hook = "prestart"
sidecar = false
}
}
task "primary-web-app-service" {
driver = "docker"
Using Prestart and Poststart hooks, users can deploy initialization applications or scripts to fetch configurations, mount volume, or block an application until its downstream service(s) are running. In addition, the new sidecar parameter enables the running of long-lived applications within batch jobs - opening up the door for monitoring, proxy, or logging services.
Watch the preview demo from Nomad Virtual Day
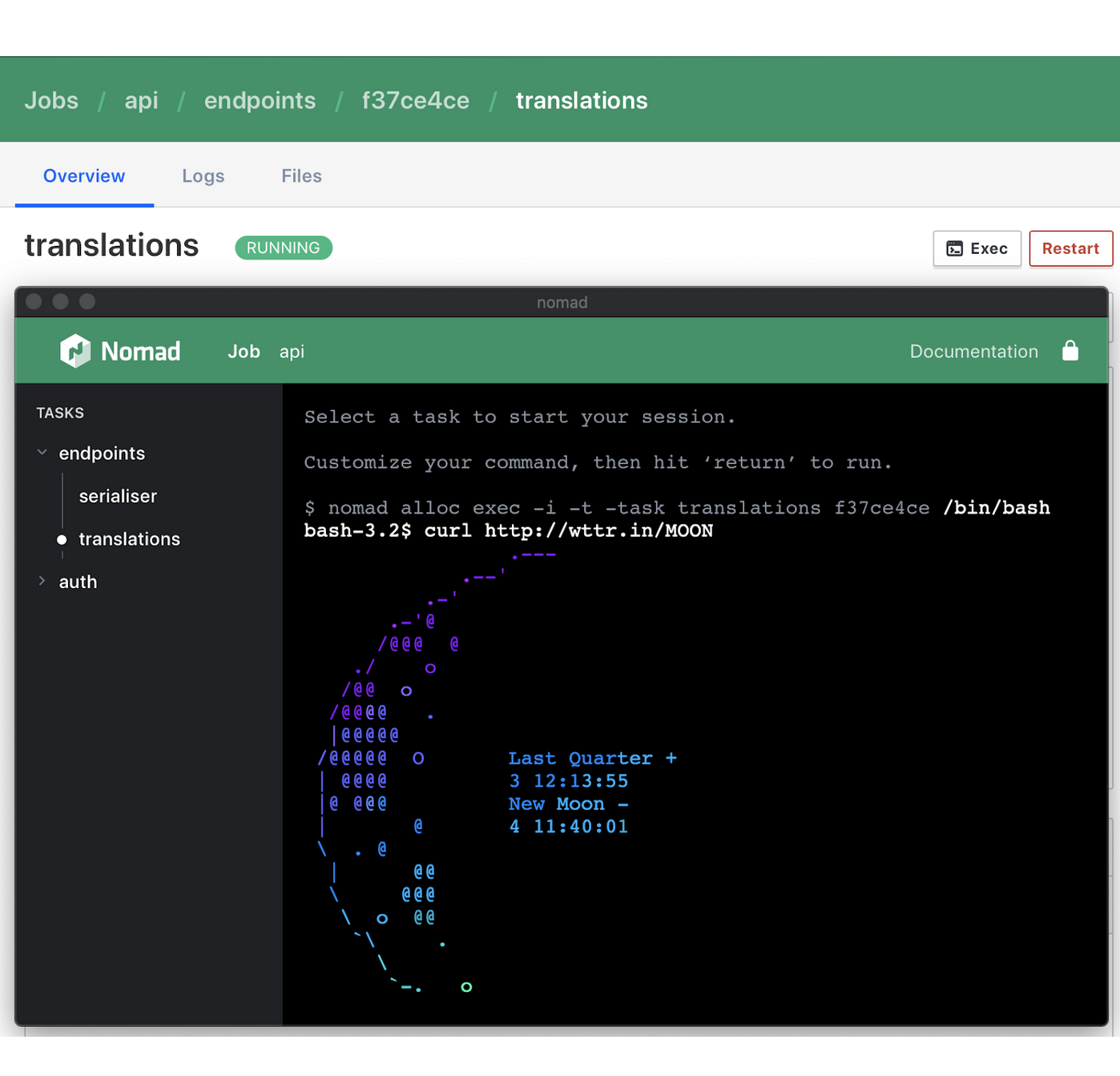
»Remote Exec (UI)
Directly execute commands in a running allocation through the Nomad UI. Users can now easily inspect container states and debug deployment failures through the web interface without the need for CLI or SSH machine access. First introduced in Nomad 0.9.2, this feature is now part of the Nomad UI to empower users with faster operability and debuggability.
»Audit Logging (Enterprise)
Secure clusters with enhanced risk management and operational traceability to fulfill compliance requirements in sectors such as finance, healthcare, and e-commerce. This Enterprise feature provides administrators with a complete set of records for all user-issued actions in Nomad.
“type”: “HTTPEvent”,
“stage”: “OperationComplete”,
"version":"v1",
"timestamp":"2006-01-02T15:04:05Z07:00",
"auth":{
"accessor_id":"d657234a-58ec-39c3-435d-9e012",
"name":"user@hashicorp.com",
"type":"client",
"global":false,
"create_time":"2020-02-12T20:13:06.798371996Z"
},
"response":{
“status_code”: 200,
"error":””
}
With Audit Logging, enterprises can now proactively identify access anomalies, ensure enforcement of their security policies, and diagnose cluster behavior by viewing preceding user operations. Designed as an HTTP API based audit logging system, each audit event is captured with relevant request and response information in a JSON format that is easily digestible and familiar to operators.
»What's Next?
Over the next few days, we'll publish a series of blogs with detailed information for each of these critical features. To watch the new capabilities in action, please register for the upcoming live demo session.
We encourage you to experiment with these new features, but as usual with beta releases, we recommend against using this build in a production environment.
We're excited about this release and can't wait to see how these new features enhance your core Nomad experience. If you encounter an issue, file a new bug report in GitHub and we'll take a look.
On behalf of the Nomad team, thank you to our community members! Your dedication, bug reports, and documentation fixes help us make Nomad better. We are grateful for your time, passion, and support.
Sign up for the latest HashiCorp news
More blog posts like this one

Nomad secrets consumption patterns: Nomad variables
Learn about HashiCorp Nomad variables — why they matter, how to create them, how to make apps use them, and how to encrypt their KEKs.

Automating workload identity for Vault and Nomad with Terraform
Learn how to use HashiCorp Vault and workload identities in your Nomad-orchestrated applications.
Terraform ephemeral resources, Waypoint actions, and more at HashiDays 2025
HashiCorp Terraform, Waypoint, and Nomad continue to simplify hybrid cloud infrastructure with new capabilities that help secure infrastructure before deployment and effectively manage it over time.