We’re pleased to announce the general availability (GA) of the new HashiCorp Terraform Enterprise. Terraform Enterprise enables teams and organizations to safely use Terraform together with collaboration and governance features.
Since the announcement of the [beta release] (https://www.hashicorp.com/blog/hashicorp-terraform-enterprise-beta) in September at HashiConf 2017, we have run a successful beta program with over 100 organizations, from small four-person teams to enterprises with thousands of developers and operators. We’ve incorporated hundreds of feedback tasks throughout the beta phase.
This release brings features out of beta and into GA and introduces several new features and improvements. HashiCorp designates products as GA that we consider ready for broad production use. Highlights of this release include:
- Workspaces replace Environments
- New User Interface
- Comprehensive API coverage
- Policy as code with Sentinel
- Other new features
»Workspaces replace Environments
Our previous “Environment” terminology in Terraform was confusing because it did not align with organizations' models of an infrastructure environment and use of concepts like development, staging, and production. Large organizations often split up those large environments, such as prod, into smaller infrastructure components such as prod-networking, prod-app1, prod-monitoring.
Workspaces enable organizations to decompose complex infrastructure configurations into modular components, or workspaces, that can be delegated and owned by separate teams. This is analogous to having multiple Git repositories which together form a larger application.
Workspaces are built right into Terraform OSS and make it easy for individuals and small teams to manage multiple states for a configuration. Terraform Enterprise moves your workspaces to a central source with a permission model, user interface, history, and more to enable collaboration while meeting the governance needs of organizations.
A workspace can be linked to a VCS repo with a Terraform configuration to automatically plan and apply the configuration after merging or submitting a pull request. It also stores the full configuration and state history as a remote state backend for the Terraform.
»New User Interface
Terraform Enterprise introduces users to a new interface design that is modern, fast, and responsive to improve the user experience. We worked directly with existing customers and practitioners to focus the interface on surfacing important information and workflows. The visual design now matches the overall Terraform look and feel.
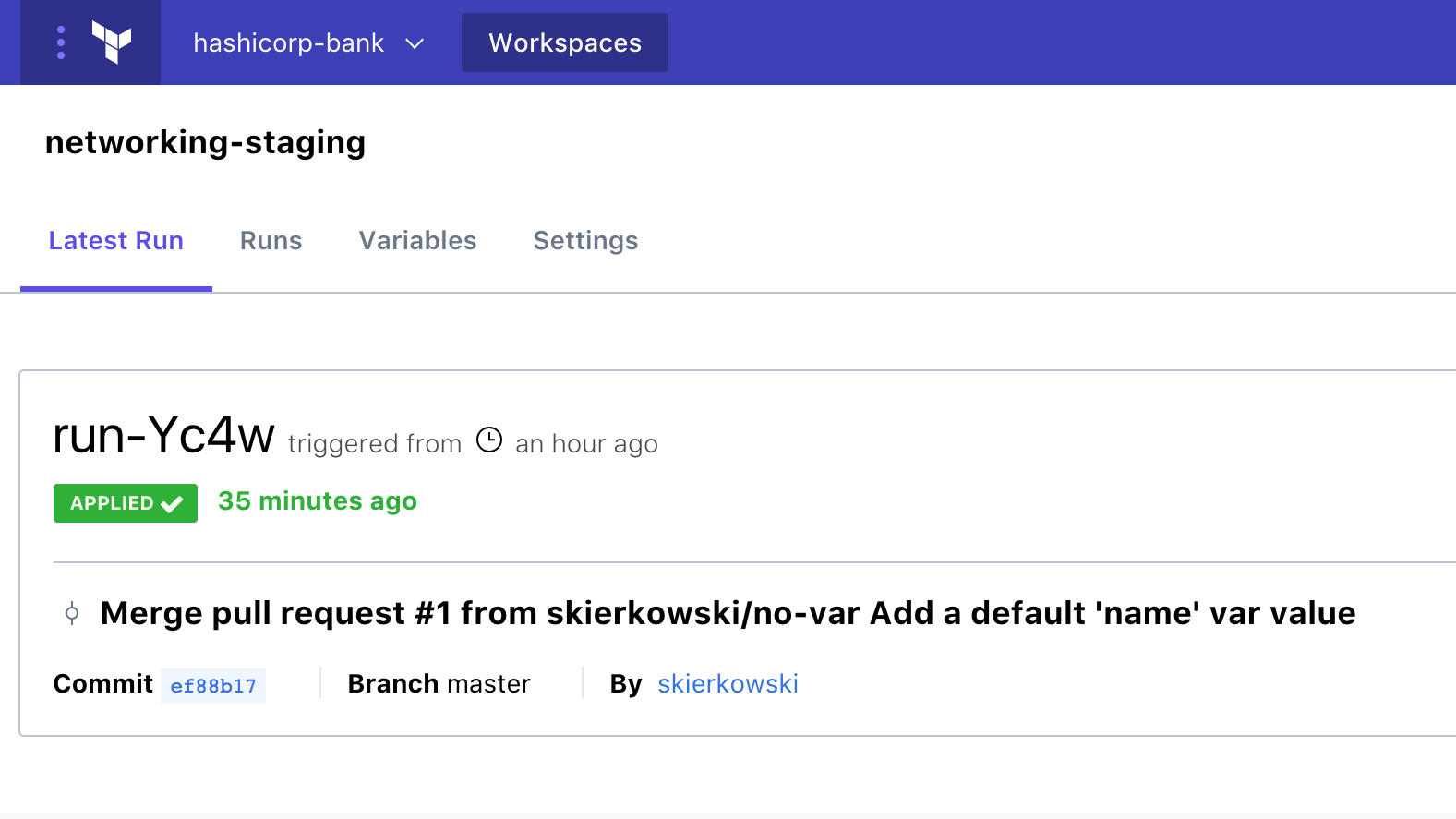
Navigation has improved to put the latest run front and center, letting you edit variables and navigate through Workspace settings.
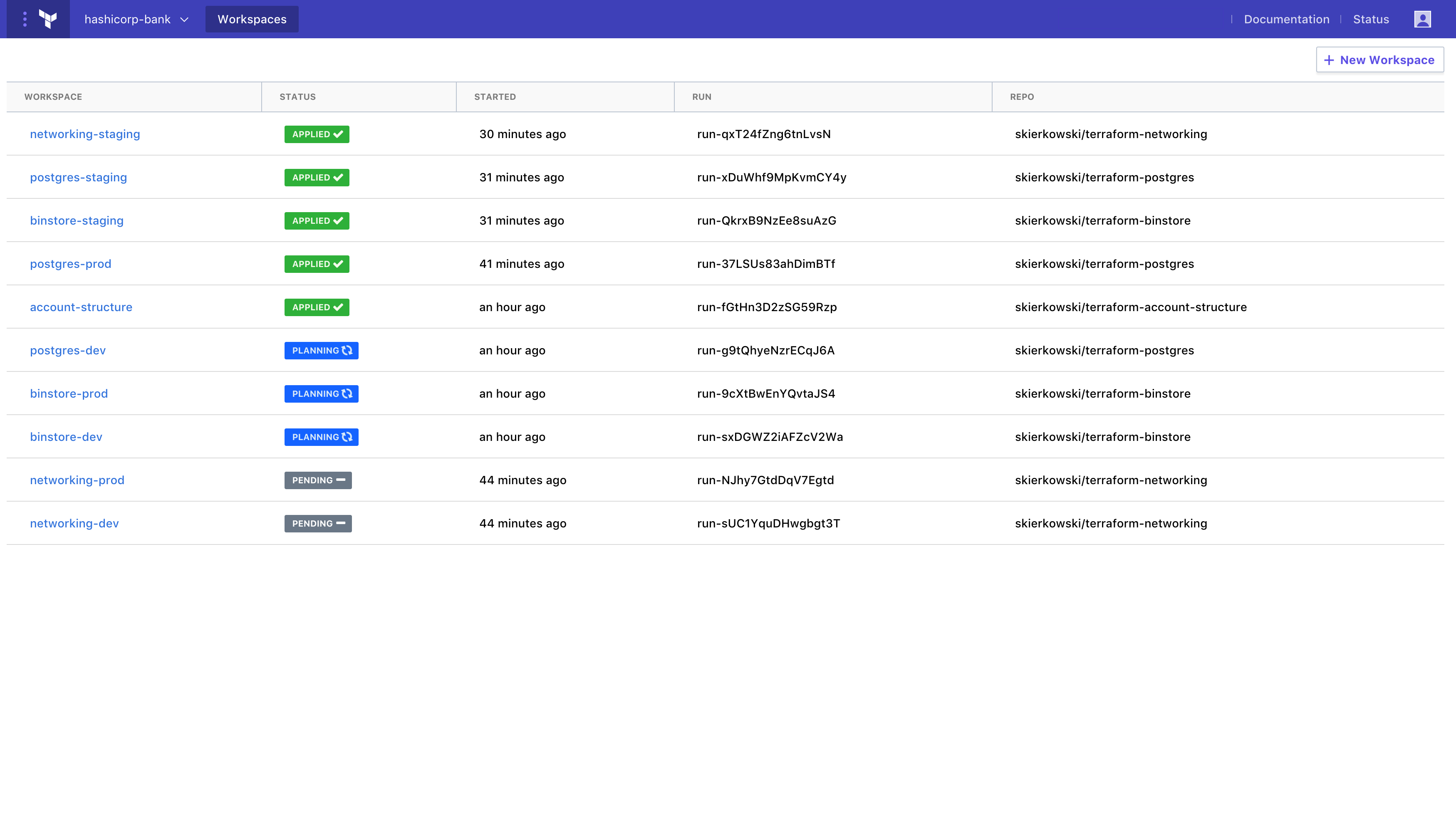
From the Workspace list, you can view all Workspaces, their most recent run status, last update time, environment attribute, and the repository source.
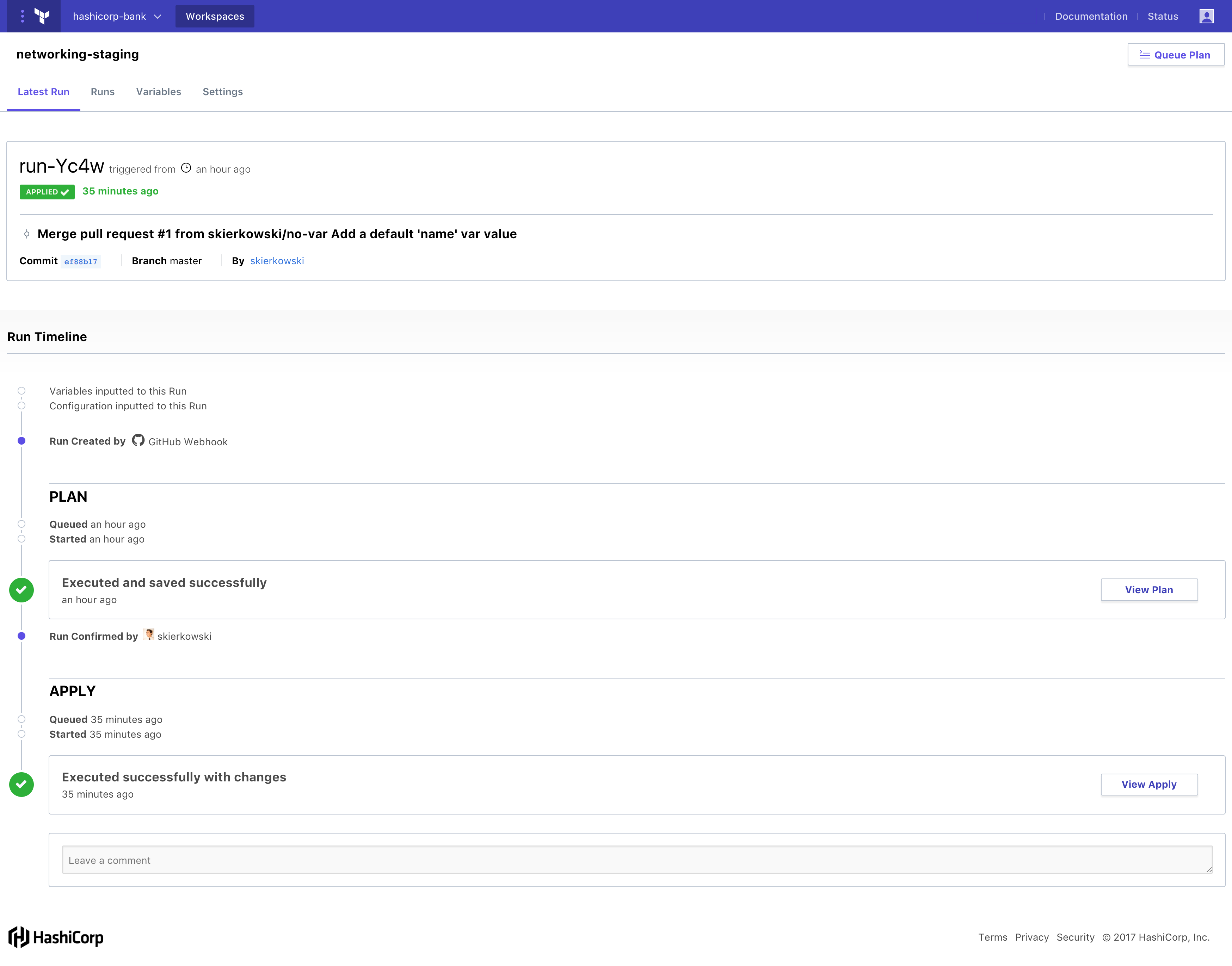
The new run details timeline view makes key information available at your fingertips. You can easily navigate to the configuration, view Terraform plan and apply logs, and approve and apply planned changes.
Organization and Workspace settings have been redesigned to make getting started easier while maintaining the fine granularity of the settings.
The following demo shows the workflow to collaborate on infrastructure using the new UI and Workspaces.
»Comprehensive API Coverage
Terraform Enterprise adds comprehensive API coverage and documentation. Previously, only a subset of features were available via the APIs. With the new Terraform Enterprise, we took an API-first design approach and made all GUI operations driven by the same APIs available to users.
The comprehensive API coverage greatly improves integration with existing investments in tools and services. Customers who use tools for provisioning IT resources will be able to integrate with Terraform Enterprise to programmatically manage Workspaces, teams, and access control. Engineering teams using CI/CD services like Jenkins can push configurations, trigger Terraform plans and applies, and get status via the API to integrate with their existing CI/CD pipeline.
Learn more about the Terraform Enterprise API by reading the documentation.
»Policy as Code with Sentinel
This feature requires Terraform Enterprise Premium.
Sentinel, HashiCorp’s policy as code framework for cloud infrastructure automation, helps organizations safely create and change infrastructure by setting policy guardrails for provisioning resources via Terraform Enterprise.
Large organizations want to enable their individual teams to independently provision and run their application however it becomes necessary for a central IT team to provide some constraints. A policy owner can define the Sentinel policies to apply to all resources provisioned via Terraform Enterprise across their organization. Terraform Enterprise embeds these policies into the provisioning workflow and enforces them between a Terraform plan and Terraform apply. Before it creates, destroys, or modifies any resources, Terraform Enterprise verifies the Terraform plan is in compliance with the policies.
For example, the policy owner can create policies that:
- do not allow resources to be provisioned without tags
- restrict which types of cloud resources can be provisioned
- enforce secure defaults for network ingress/egress rules
The “Sentinel and Terraform Enterprise: Applying policy as code to infrastructure provisioning” article covers Sentinel and Terraform Enterprise announcement in depth.
Learn more about Sentinel by reading the documentation.
»Other new features
»Service Accounts
With the addition of comprehensive API coverage, we’ve added support for new API-driven use cases. In many of the API-driven use cases, calls are made from other services, not from individual users. To better address these cases, Terraform Enterprise adds two types of service accounts: organization-based and team-based. These accounts can be granted permission to access Terraform Enterprise APIs but cannot be used interactively. The service accounts are designed to support server-to-server API calls using the service identity, as opposed to individual user identities. You can read more about organization and team based accounts in the Service Account documentation and the corresponding API docs for organization tokens and team tokens.
»Bitbucket Server
Terraform Enterprise provides integration with version control systems (VCS) to facilitate collaboration on infrastructure as code. Terraform Enterprise users have been doing version-controlled infrastructure with VCS providers including Github, Github Enterprise, Gitlab, Gitlab EE/CE, and Atlassian Bitbucket Cloud. We are pleased to announce the addition of Atlassian Bitbucket Server as a VCS integration with Terraform Enterprise.
The addition of Bitbucket Server will give you the ability to search for repos in Bitbucket Server when creating new workspaces, automatically start new runs on new commits to a chosen branch, and automatically update merge requests with the status of a Terraform plan.
To learn more, visit the Configuring Bitbucket Server Access documentation.
»SSO with SAML
Terraform Enterprise now supports single-sign-on with SAML so users can login to Terraform Enterprise using their corporate SAML identity provider. Additionally, you can configure Terraform Enterprise to use SAML assertions to automatically map users to teams so you can use your identity store to manage authorization in Terraform Enterprise.
To learn more, visit the SAML SSO Documentation.
»Upgrading
Terraform configurations built for the previous version of Terraform Enterprise (formerly under the Atlas name) are compatible with the new Terraform Enterprise. However, Terraform Enterprise (Atlas) organizations and environments are not compatible with the new Terraform organizations and workspaces. The Upgrading From Terraform Enterprise (Atlas) guide walks through migrating environments and associated state files to workspaces.
The Atlas version of Terraform Enterprise will be decommissioned on Friday, March 30, 2018, by which time all environments must be migrated to workspaces. The legacy environments will be locked out and removed thereafter.
»Decommissioning Atlas
The Packer and Artifact Registry features of Atlas will no longer be actively developed or maintained and will be fully decommissioned on Friday, May 31, 2018. "Atlas" has been renamed to Terraform Enterprise and the features being developed are focusing on Terraform.
While the hosted Packer offering and Artifact Registry will be decommissioned, Packer as an open source project continues to exist as a standalone offering with an active development team and vibrant community.
This is the final step in the path we began 18 months ago to split Atlas into a suite of smaller, module enterprise offerings to mirror the open source suite of tools. Vault, Consul, and Nomad were removed from Atlas early in 2017.
We understand that removing features can be painful and we are sorry for any disruption that this may cause you. For those of you currently using hosted Packer or the Artifact Registry, we’ve prepared the guide “Building Immutable Infrastructure with Packer in CI/CD” to walk through building images with Packer in CI/CD, uploading the image to an artifact store, and creating a new run in Terraform Enterprise.
The Packer and Artifact Registry features within Atlas will continue to work with Terraform Enterprise until March 30, 2018. To migrate from Atlas to Terraform Enterprise, see the "Upgrading" section above.
»Conclusion
Terraform Enterprise GA is available today. For more information or to request a free trial, visit https://www.hashicorp.com/products/terraform.