This post is the second part of a three-part series showing how VPC Lattice can help achieve private connectivity from Vault self-managed (refers to Vault Enterprise or Vault Community Edition) to resources like Amazon RDS without direct connections to the RDS VPC via VPC Peering or Transit Gateway. Check out Part 1 if you would like to get an overview on the other connectivity patterns available. Alternatively, jump ahead to Part 3: Connecting HCP Vault Dedicated to Amazon RDS using Amazon Lattice if you’re interested to see a demo of how Lattice can achieve private connectivity with the cloud managed Vault service: HCP Vault Dedicated.
»Connecting Vault to RDS using VPC Lattice with Lattice service network endpoints
For this demo, we deploy the following architecture that uses Lattice service network endpoints to connect privately from Vault to RDS.

From the RDS instance Connectivity & security page, note the RDS endpoint. The original endpoint value will be used to connect to the database instance from the consumer VPC.

Navigate to the VPC console and choose Endpoints. View the details of the VPC endpoint with the endpoint type ServiceNetwork. It has Private DNS names enabled and you can see the RDS endpoint listed in the Associations tab under Private DNS.

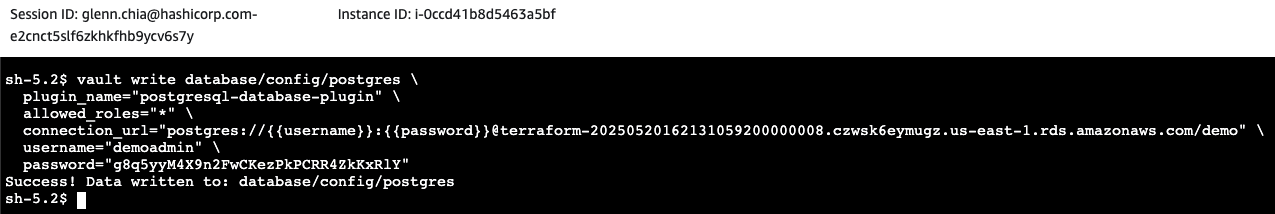
Connect to the EC2 instance via session manager. Once the session is established, run the following commands to enable the database secrets engine.
vault secrets enable database

Configure Vault with the proper plugin and connection information. Vault will use the database user specified here to create/update/revoke database credentials. Replace <RDS_ENDPOINT> with the RDS endpoint retrieved at the start of this section and replace <DB_NAME> with the name of the database you created. In addition, replace <USERNAME> and <PASSWORD> with your database username and password. This succeeds and shows that Vault is able to connect to the RDS instance. Note that in a real environment you should tighten allowed_roles to only include roles that you believe should be allowed to generate credentials. Use this configuration to set those roles.
vault write database/config/postgres \
plugin_name="postgresql-database-plugin" \
allowed_roles="*" \
connection_url="postgres://{{username}}:{{password}}@<RDS_ENDPOINT>/<DB_NAME>" \
username="<USERNAME>" \
password="<PASSWORD>"
Configure a role that maps a Vault role named example to a set of creation statements that create the database credential. The {{username}} and {{password}} fields will be populated by the plugin with dynamically generated values. The {{expiration}} field is also supported in some plugins.
vault write database/roles/example \
db_name="postgres" \
default_ttl="1h" \
max_ttl="24h" \
creation_statements=- << EOF
CREATE ROLE "{{name}}" WITH LOGIN ENCRYPTED PASSWORD '{{password}}' VALID UNTIL '{{expiration}}';
GRANT SELECT ON ALL TABLES IN SCHEMA public TO "{{name}}";
EOF

Generate a new credential by reading from the /creds endpoint with the Vault role named example:
vault read database/creds/example

Use the dynamic secret to connect to RDS. Replace the host with the RDS instance endpoint and replace <DB_NAME> with the name of the database you created. Finally, replace the username with the dynamic username from above. When prompted, enter the password from above.
psql \
--host=<RDS_ENDPOINT> \
--port=5432 \
--username=<DYNAMIC_USERNAME> \
--dbname=<DB_NAME>

Run the following command to view the dynamic user created:
SELECT usename FROM pg_catalog.pg_user;

With this we have shown how Vault can connect to RDS over VPC Lattice using the RDS instance’s original DNS name.
»Learn more
This blog demonstrated how to connect Vault self-managed to RDS directly using VPC Lattice without connecting the two VPCs. You can then leverage Vault’s database secrets engine to generate dynamic credentials for access to RDS. This concludes part 2 of the three-part series on Lattice integrations with Vault. Check out the other parts that highlight more design patterns and demos:








