Secrets such as API keys, database passwords, tokens, and certificates are needed everywhere in the coding process. It’s incredibly easy for one to be exposed unintentionally through logs, collaboration tools, or in public code repositories.
To plug this gap, open source secret scanning products are often the first tools security teams try. They’re free, widely available, and can be easy to integrate.
Many open source tools are great at detecting obvious plaintext secret commits in your Git repository. But teams will quickly discover that there’s a lot more work to be done after a leaked secret is found. As development environments grow more complex, secret scanning requirements often outpace what open source tools were designed to handle.
We’ll explore how teams can extend the strengths of open source scanning and develop a more scalable detection approach as their environments and architectures grow.
»1. End-to-end secrets visibility and remediation guidance
Detection is only the beginning. Effective secrets management requires a full lifecycle approach that spans detection, prioritization, triage, remediation, rotation, and revocation. Each stage has its own technical challenges, from distinguishing valid credentials from noise, to automating rotations across distributed systems, to verifying that revocation actually closes the exposure.
Most open source scanners focus on the first step. They rely on static regex to flag potential secrets in source code or configuration files. While this can catch obvious plaintext patterns, these tools lack the deeper context needed to evaluate whether a token is active, sensitive, environment-specific, or already mitigated. The result is a high rate of false positives and missed detections of non-patterned secrets.
Vault Radar goes beyond pattern matching by applying layered, context-aware detection models trained on real-world data. This enables Radar to identify secrets across code, pipeline, and data sources, then tie each finding to context such as privilege level, commit history, and blast radius. With this context, Radar can automatically prioritize high-risk exposures and provide step-by-step remediation.
The result is greater precision, fewer false positives, and the ability for teams to close the loop from detection to resolution with confidence and speed.
»2. Continuous coverage, not just point-in-time scans
Open source scanners usually run in narrow workflows and provide a minimal number of intervention points for scanning: a pre-commit hook, a scheduled CI scan, or an occasional repo sweep. These are useful guardrails, but secrets leak at every phase — right from code creation in your IDE, old branches, forgotten configs, or legacy pipelines.
Vault Radar takes a continuous, holistic approach to secret security, by constantly monitoring activity across your entire development ecosystem, from collaboration tools like Slack and Jira to IDEs, repositories, CI/CD pipelines, and configs.
Instead of relying on point-in-time scans, Vault Radar provides real-time visibility and protection, ensuring that exposures are caught and resolved as they happen.
»3. Remediation integrated into the developer experience
Open source tools flag a secret, then leave the rest to you. Developers are left wondering:
- Is this a real issue or a false alarm?
- How do I fix it without breaking something?
- Where should this secret actually live?
This slows teams down and creates unnecessary friction between development, operations, and security.
Vault Radar removes that friction by meeting developers where they work. It integrates directly into IDEs, providing contextual guidance and automated remediation steps. With seamless ticketing, alert integration, and clear prioritization, developers can resolve issues quickly and confidently without breaking their flow.
The result? Faster mean time to remediation (MTTR), better collaboration across teams, and a smoother, more secure development experience.
»4. Enterprise-scale visibility and compliance
Managing secrets across a few repositories is challenging. Managing them across thousands of repos, pipelines, and globally distributed teams is another level entirely. At enterprise scale, visibility, governance, and control become just as critical as detection.
Vault Radar is designed for exactly that scale. It provides unified dashboards for complete visibility, enterprise-grade reporting for audit and compliance needs, and scalable deployment options across hybrid and cloud environments.
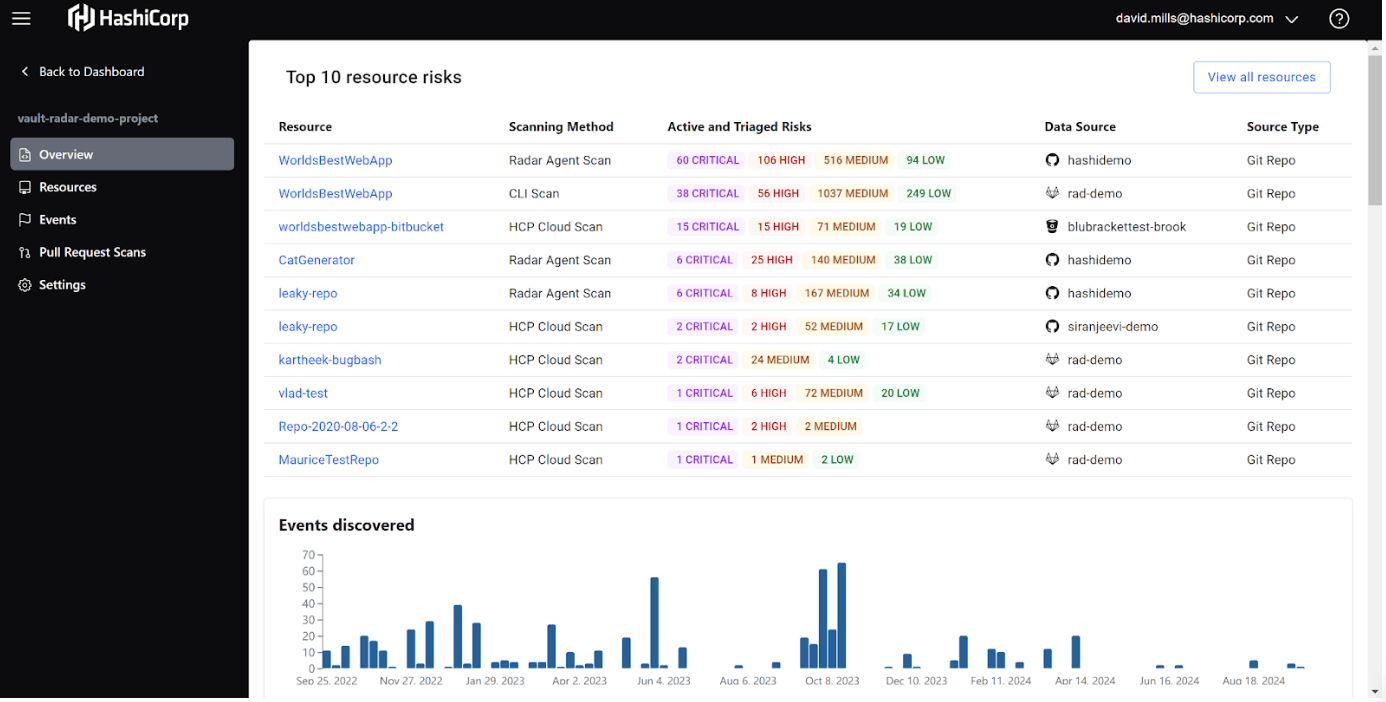
The result: proven control over your most sensitive assets, simplified compliance workflows, and confidence that your secret scanning strategy can grow with your organization.
»When to use commercial vs open source secret scanning
Open source secret scanners have played an important role in helping teams take their first steps toward stronger secrets hygiene. They made secret scanning accessible and easy to adopt, a critical first milestone in modern software development.
Today's development environments look very different. Teams ship faster, collaborate across more tools, and manage sprawling pipelines that span cloud, hybrid, and on-prem systems. Preventing exposures and managing secrets at scale requires a new generation of solutions, ones built for continuous, intelligent, enterprise-grade protection.
»Think of secret scanning as a journey.
What began with open source tools focused on regex detection has now evolved into intelligent systems that deliver real-time monitoring, remediation, and governance. The table below illustrates how organizational needs evolve on this journey from open source secret scanning to commercial, enterprise-grade systems like HCP Vault Radar.
| Category | Open source scanners | HCP Vault Radar |
| Detection accuracy | Regex scanning, which can result in high false positives and missed edge cases | Context-aware detection leading to fewer false positives
|
| Coverage | Point-in-time scans; limited to repos or CI/CD where manually configured | Continuous monitoring across cloud and on-prem environments, covering repositories, CI/CD pipelines, configurations, and developer IDEs. |
| Developer experience | Noisy alerts, manual fixes, low or no guidance | IDE plug-in; contextual remediation guidance; seamless developer workflow |
| Remediation | Stops at detection; teams must figure out rotation and storage | Automated import into Vault; supports revocation, rotation, and governance |
| Integration | Requires manual setup; limited workflow integration | Deep integration with IDEs, CI/CD pipelines, and ticketing systems |
| Scalability | Hard to manage at enterprise scale | Enterprise-grade dashboards, reporting, quick time to onboard, and policy enforcement |
| Compliance Support | Limited audit trails or compliance features | Built-in evidence collection, reporting, and compliance alignment |
| Total cost of ownership | Free license, but expensive in the long run — between engineering effort, false positives, missed incidents, commercial upgrades, and paid add-ons | Lower TCO through automation, reduced incidents, and streamlined audits |
»From detection to full lifecycle protection
Secret scanning has evolved from simple regex-based detection to continuous, intelligent lifecycle management. Vault Radar represents that next stage, combining accurate detection, proactive monitoring, automated remediation, and enterprise governance in a single platform.
Vault Radar helps teams move from reactive detection to proactive protection, reducing incidents, streamlining compliance, and empowering developers to focus on building.
Ready to get started today? Start your 30-day HCP Vault Radar trial today.
Interested in learning more about Vault Radar? Check out our webinar series.







