As organizations accelerate their adoption of cloud infrastructure and applications, they face the increased security risks that come with expanding their cloud footprint. Securing infrastructure with static perimeters and IPs is no longer adequate in dynamic environments. More than ever, organizations need to address issues of least-privileged access, secret sprawl, and long-lived credentials.
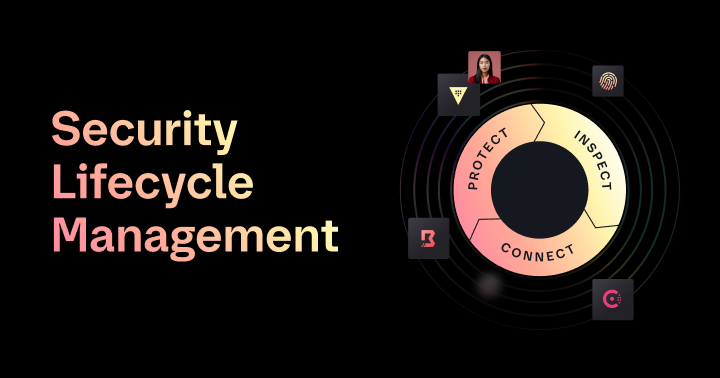
In these dynamic environments, organizations need a new approach to Security Lifecycle Management (SLM). SLM is the process by which organizations manage their most sensitive data, from creation to expiration. The technologies your organization uses for SLM should be built on a zero trust, identity-based access architecture, enabling teams to continuously protect credentials and other secrets, inspect their digital estate for unsecured secrets, and connect authorized machines, services, and people. This blog looks a bit more closely at how organizations can protect, inspect, and connect their environments and work toward full Security Lifecycle Management.
»Protect secrets
To adequately protect their environments, organizations need a system of record and full lifecycle management for secrets (certificates, passwords, keys, etc.). The first step is to gather and store all of the organization's secrets in a central system of record. Then teams should employ secrets rotation and dynamic secrets to mitigate the risk associated with long-lived credentials. With a centralized secrets management system, organizations can set policy and reduce the risk of credential exposure.
»Inspect sensitive elements
Organizations can’t protect what they don’t know is vulnerable, so proper inspection of environments to identify any unsecured sensitive data is crucial. The first step is to scan code repositories to identify any unmanaged or exposed secrets. From there, ensure all access points from the secrets management system are being logged and audited. Next, make sure that all privileged access sessions are recorded and audited. Finally, organizations should use a service registry with real-time visibility into its directory of services.
»Connect machines, people, and networks
Enforcing least-privilege access based on trusted identities across the organization is a critical best practice. Teams must ensure that every request for machine-to-machine, human-to-machine, and service-to-service access is authenticated and authorized based on identity instead of brittle, hard-to-manage IP-addresses. Teams need tools that can manage fine-grained role-based access controls (RBAC) based on security and operations team policies. The platform to manage identity-based access also needs to integrate with the organization's preferred identity access management (IAM) or Active Directory providers.
»SLM and The Infrastructure Cloud
Earlier this year, we launched The Infrastructure Cloud, an approach powered by the HashiCorp Cloud Platform (HCP) that unifies Security Lifecycle Management and Infrastructure Lifecycle Management (ILM) on one platform. The SLM side of The Infrastructure Cloud enables your platform and security teams to have the systems in place to protect, inspect, and connect the sensitive elements of your environment. HashiCorp offers a portfolio of products managed on HCP that help with different aspects of your security strategy, including HCP Vault, Boundary, and Consul.
»Vault for machine authentication and authorization
HashiCorp Vault is the industry standard for brokering trusted identities and automating access to secrets, data, and systems. Vault uses your preferred IAM providers to ensure that people and machines are who they say they are, and get access to only what they need to access based on fine-grained controls. Vault then acts as a system of record to centrally store secrets and sensitive data.
Vault not only authenticates and authorizes access but also helps manage the entire lifecycle of the credentials used in your environment. First, HCP Vault Radar scans code and other repositories to find potential unsecured secrets that exist in plaintext. Then it helps prioritize actions based on whether the secret is actively being used or if it’s already stored in Vault.
Once you’ve identified where your secrets are living, organizations then need to store these secrets, certificates, and keys securely in Vault, enforcing a least-privilege architecture where only people and applications that need access, get access. With Vault, you can set policy on your secrets and certificates, expire them, rotate them, or dynamically generate short-lived credentials. Once your secrets are stored and managed in Vault, you can authenticate and authorize every access request based on user identity.
»Boundary for human-to-machine access
HashiCorp Boundary is a modern privileged access management (PAM) solution for dynamic resources. It provides a consistent experience for users to securely access resources in any public or private cloud. With Boundary, end users no longer need to handle credentials or resources when accessing infrastructure resources, reducing the potential of a breach. Instead, users have a passwordless experience via integration with Vault, which generates short-lived, single-use credentials that are useless to attackers if exposed. Administrators can pre-authorize users to access target resources based on their identity and limit users from accessing other resources.
Boundary allows organizations to manage the lifecycle of session connections, credentials, and target resources by automating the discovery and cataloging of host resources. Access to resources is protected and gated by Boundary, providing a consistent way to authenticate users in any multi or hybrid cloud environment.
Administrators have full control to inspect the environment by monitoring and auditing all user activity. Sessions are recorded to deter malicious behavior and to meet compliance requirements. Any suspicious user or session can be immediately terminated. Boundary audit logs can be streamed to centralized event monitoring tools. Lastly, session recording lifecycle management prevents recorded sessions from being accidentally or maliciously deleted before the expiration date.
»Consul for machine-to-machine access
HashiCorp Consul provides organizations with identity-based service networking for service discovery, secure service-to-service communication, and network automation across multiple cloud and runtime environments. Consul's secure service mesh ensures secure and authorized service-to-service communication, offering encryption, observability, and resilience for application traffic. By automating complex networking tasks like load balancers, firewalls, gateways, and VPNs, Consul streamlines application deployment and Day 2 operations. Consul enables scalable service networking solutions for organizations dealing with the challenges of secure networking across multiple datacenters while ensuring global visibility and control.
»Get started with Security Lifecycle Management
By leveraging HashiCorp’s Security Lifecycle Management offerings, organizations can trust that their most sensitive data is protected from start to finish. To start implementing Security Lifecycle Management in your organization, sign up for a free HCP account today.