HashiCorp Vault 1.10 was released on March 23rd, introducing some exciting new features and enhancements. Now you can visit the Vault 1.10 Release Highlights collection on HashiCorp Learn and start exploring what's new.
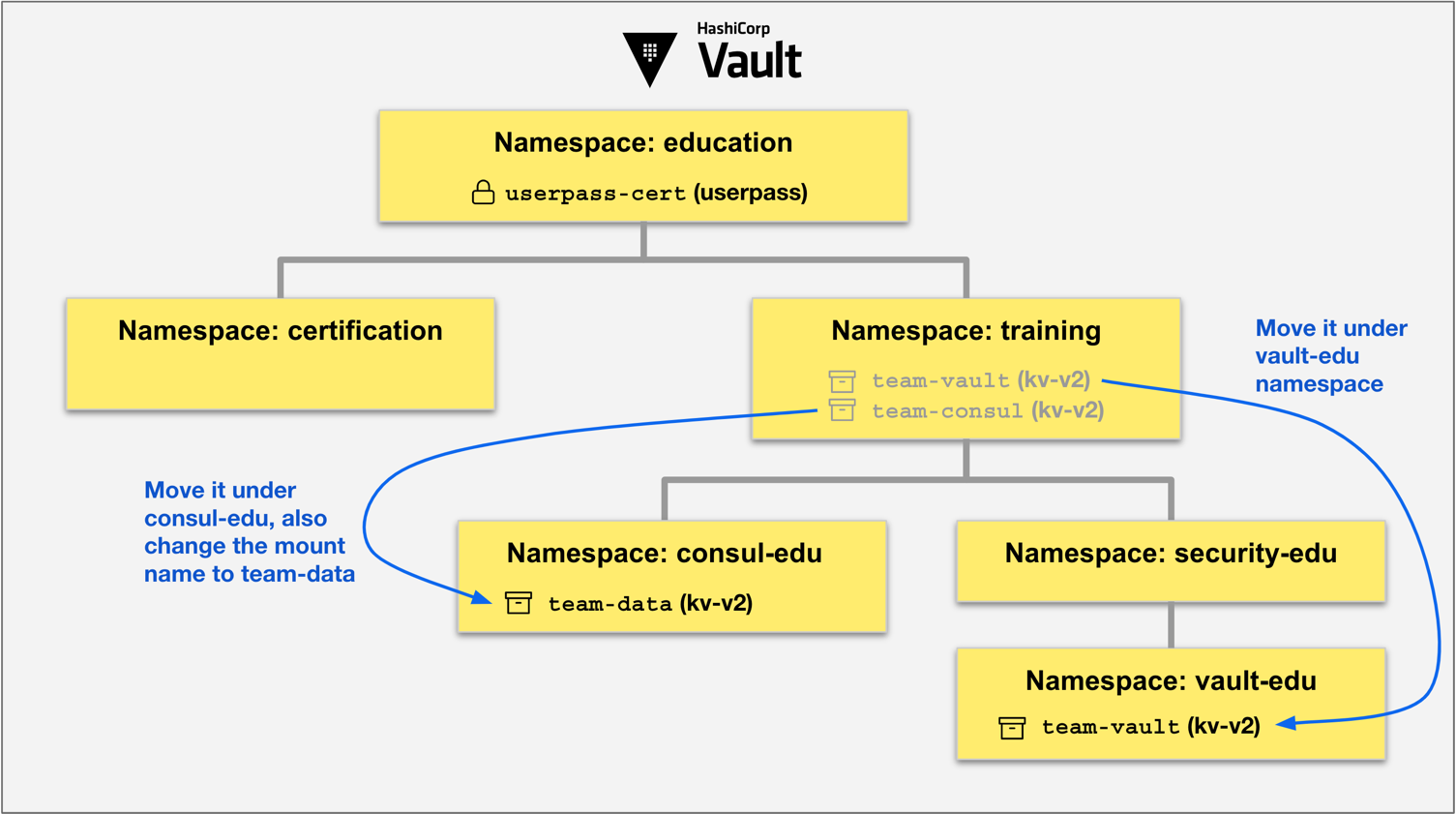
»Move Secrets Engines and Auth Methods Across Namespaces
Vault 1.10 extended the sys/remount API endpoint to support moving secrets engines and auth methods from one mount location to another. If you are running Vault Enterprise with namespaces, you can move them from one namespace to another.
The new Move Secrets Engines and Auth Methods Across Namespaces tutorial demonstrates how easily you can move secrets engines and auth methods from one mount path to the new target path across namespaces.
»IBM Db2 Credential Management
Many large enterprises that use IBM Db2 databases are delegated to using local usernames and passwords for access into Db2 databases. Using Vault's OpenLDAP secrets engine, you can let Vault manage the credential lifecycle for Db2 environments.
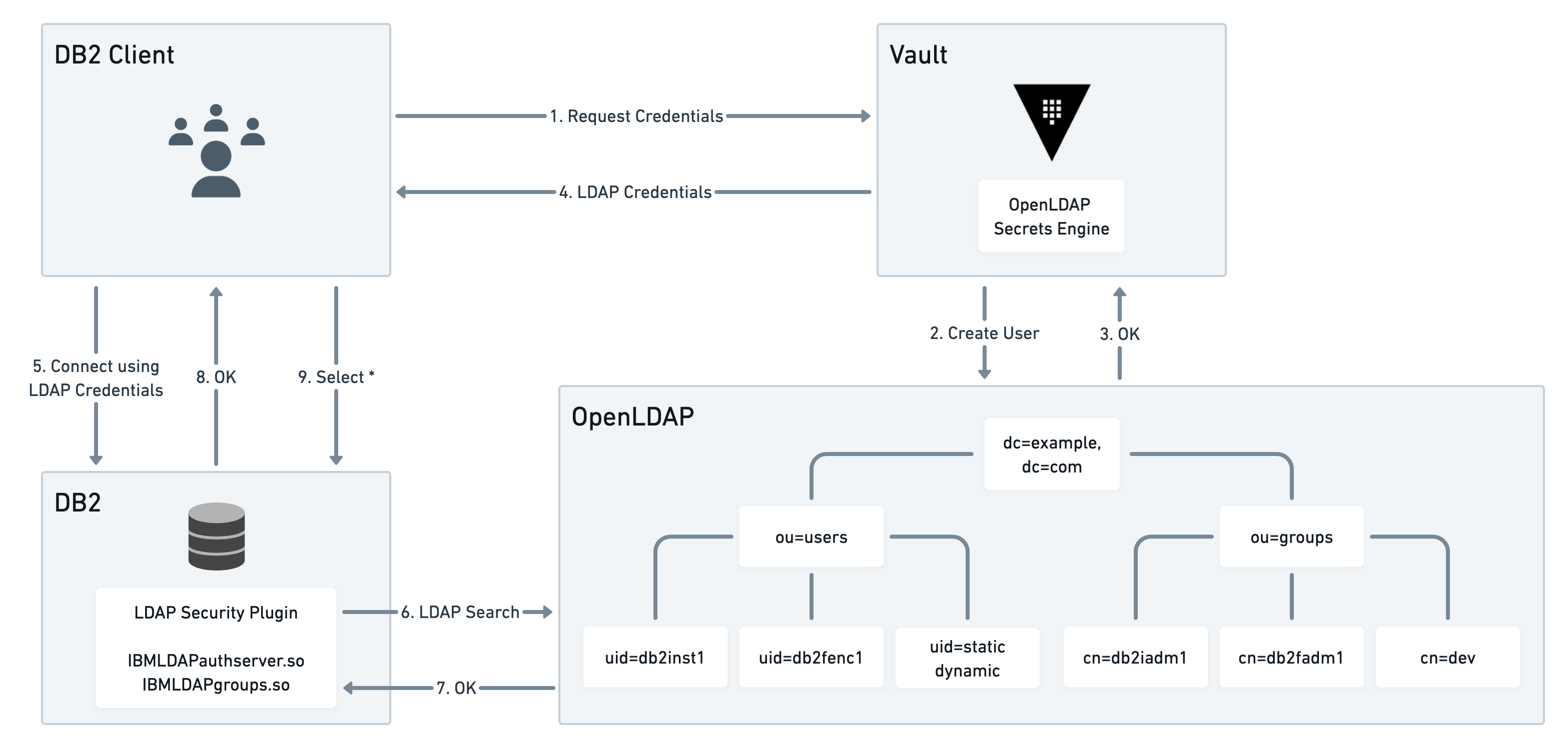
The IBM Db2 Credential Management tutorial demonstrates how to use the OpenLDAP secrets engine to solve the Db2 credential management challenge.
»Vault Usage Metrics
The Vault usage metrics dashboard in Vault 1.10 enables you to select a billing period more easily than before.
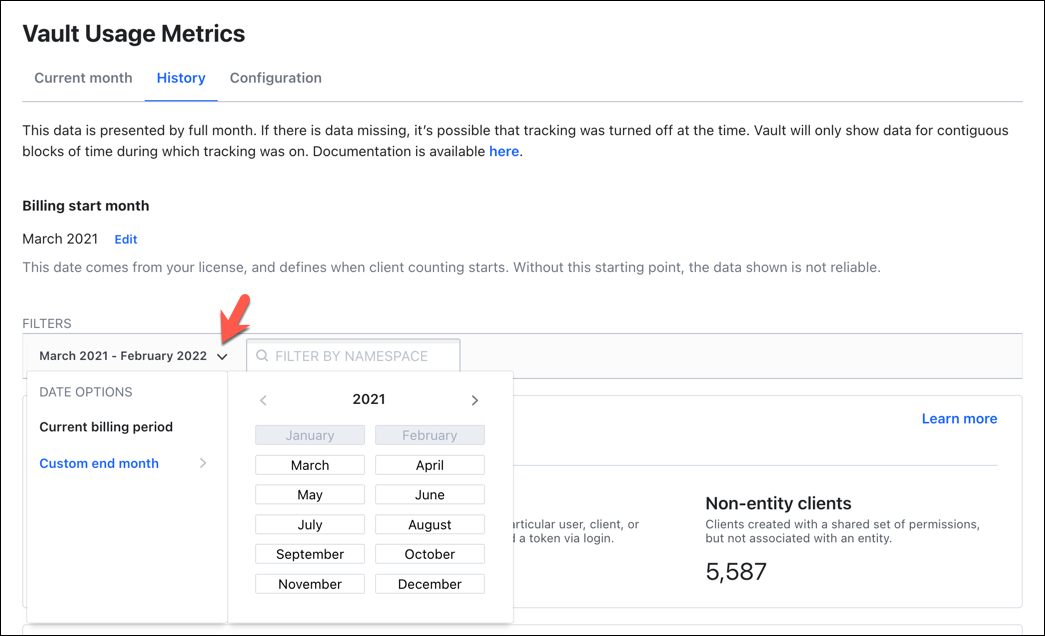
In addition, you can view client count per auth mount. You can also view month over month changes to clients via the API.
See the updated Vault Usage Metrics tutorial to learn more about this enhanced experience.
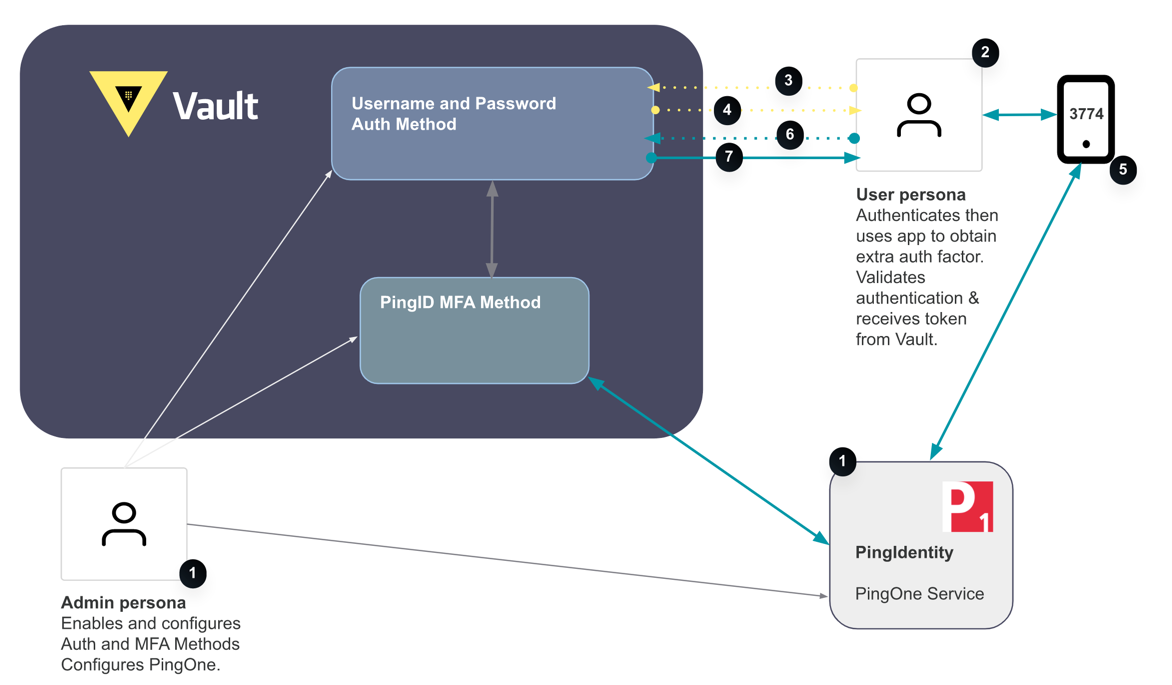
»Multi Factor Authentication (MFA)
Multi-factor authentication (MFA) is a mechanism for outsourcing secondary authentication for your website (or other product) to a third-party one-time key provider.
Vault 1.10 added an open source login MFA integration for additional authentication (authN) using time-based one-time password (TOTP), Okta, Duo, and PingIdentity.
The Enable Login Multi Factor Authentication (MFA) tutorial demonstrates MFA with PingID.
»Server-Side Consistency Tokens
Vault 1.10 introduced an updated token format to enable greater control over the consistency model, allowing performance standby nodes to decide whether to forward requests.
See the Tokens tutorial to learn about the new token format. If you are a Vault Enterprise user, refer to the Performance Standby Nodes tutorial, which describes the server-side consistent token.
»Automatic Key Rotation
If you are storing encrypted data, you should periodically rotate the encryption key to make it difficult for a malicious user to make unauthorized attempts to decrypt the data.
Vault 1.10 introduced the capability to rotate your encryption key automatically. Check the updated Encryption as a Service: Transit Secrets Engine tutorial, which demonstrates the automatic key rotation feature.
»Vault AWS Lambda Extension
The Vault AWS Lambda Extension tutorial was updated to demonstrate the caching configuration for the Vault Lambda extension local proxy server so that it does not forward every request to the Vault server.
»Vault as an OIDC Identity Provider
Vault 1.9 introduced the ability to configure Vault as an OIDC identity provider as a Technical Preview. It is now generally available in 1.10. This lets users leverage pre-existing Vault identities for authN into their applications.
See the Vault as an OIDC Identity Provider tutorial for step-by-step instructions.
»More to Learn
For other tutorials on all the features of Vault, including videos and in-browser hands-on lab environments using real cloud compute resources that we provide for you, visit HashiCorp Learn.








