At the end of last year we introduced policy sets for HashiCorp Terraform Enterprise. Policy sets are a feature for users to enforce policies on select workspaces of their choice with Sentinel, the embeddable HashiCorp policy as code framework. They enable organizations to create logical groups of policies to apply against different environments and for different components of their infrastructure.
Today at HashiConf EU we are pleased to announce that policy sets may now be configured to source policies from version control systems (VCS), bringing all of the immutability benefits that users currently enjoy with Terraform configuration to Sentinel policies.
Immutability is a guiding principle in all of our products — part of the Tao of HashiCorp. Infrastructure management done responsibly is a versioned, auditable, repeatable, and collaborative process. All of these principles are exactly what Terraform Enterprise provides for infrastructure. With versioned policy sets, these same principles can now be applied to governance and policy management.
»Writing Policies
Policy code can now be sourced directly from any VCS provider configured in Terraform Enterprise. For a complete list of supported VCS providers, see the VCS Integration documentation.
As a very simple and light-hearted example, we'll write some Sentinel policy against Terraform configuration using the random_pet resource from the random provider, which generates random names (e.g.: gentle-reindeer, daring-dodo). We'll store our policy and configuration in a repository on GitHub.com.
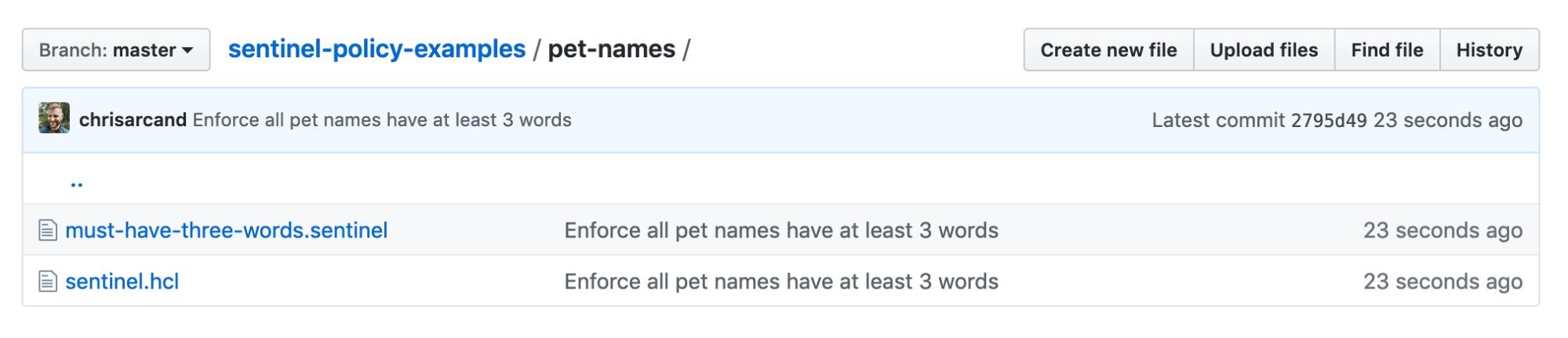
The directory contains two files:
sentinel.hcl- This is the configuration file which identifies Sentinel policy files and provides their configuration, written in HCL. Our configuration file specifies each policy to be checked within the set, as well as the enforcement level of the policy.
policy "must-have-three-words" {
enforcement_level = "hard-mandatory"
}
must-have-three-words.sentinel- This is the policy code itself. In our example, we'll ensure that each pet name resource is configured to generate at least three words (really-superb-toucanwould be valid, butepic-codwould not). Multiple policy blocks may be defined in thesentinel.hclfile to configure more policies.
# Enforces each pet name to have at least three words.
import "tfconfig"
main = rule {
all tfconfig.resources.random_pet as _, pet {
pet.config.length >= 3
}
}
With our policy code pushed to VCS, we're ready to configure Terraform Enterprise to use it.
»Creating a Versioned Policy Set
When creating a new policy set, you are presented with a new user interface where you can select a Policy Set Source from your configured VCS providers, or opt to directly upload a new version of the policy code via API:
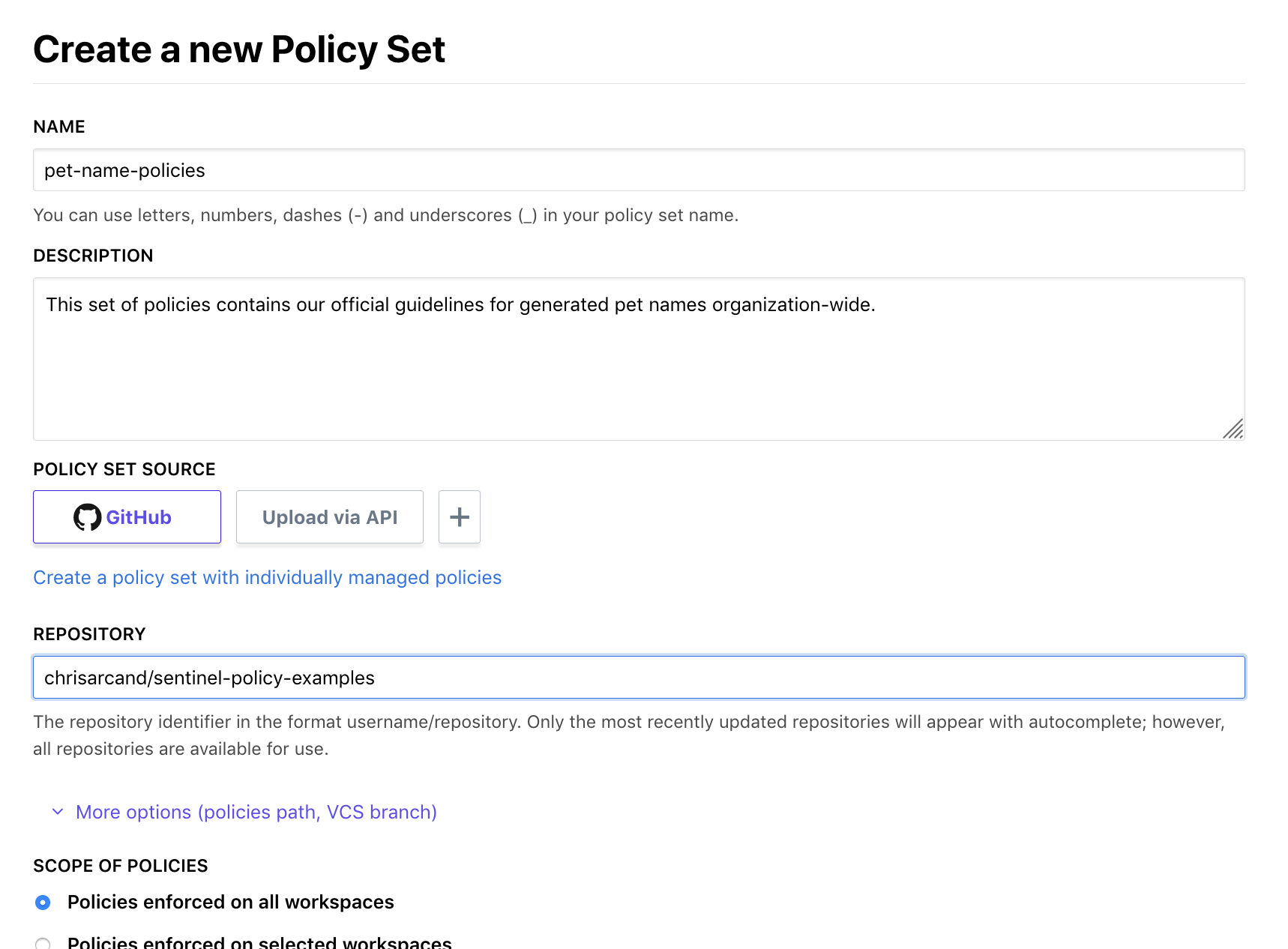
Under "More options", you can also specify a path where your policies are stored in the remote repository (/pet-names in our example) as well as a non-default branch, if applicable.
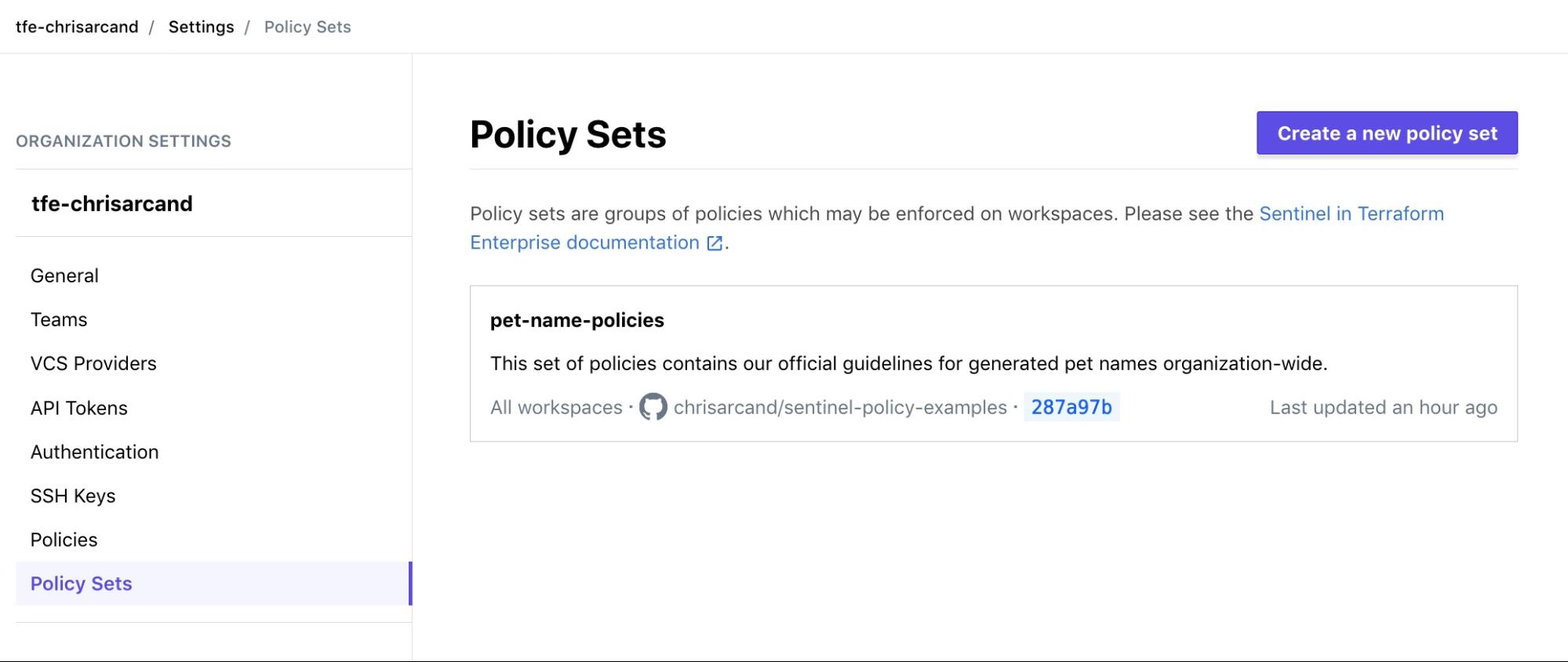
After creating the policy set, you'll see it appear in the Policy Sets screen along with information like the repository name and latest commit SHA that policy code was sourced from.
»Enforcing policy
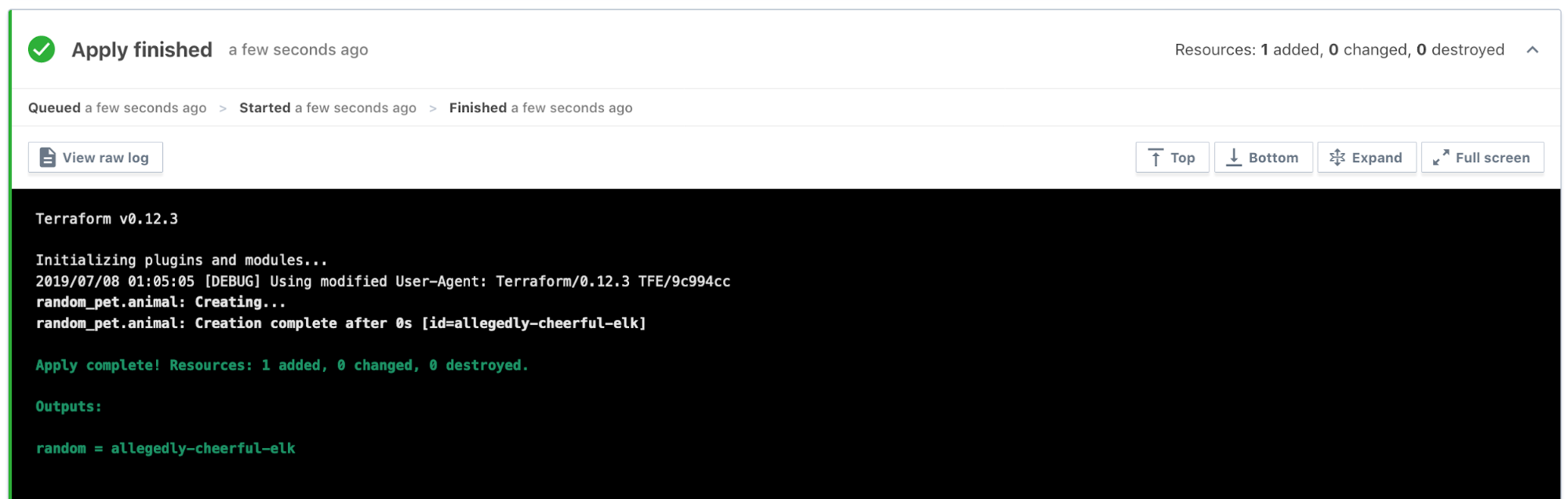
With the policy set configured, Terraform Enterprise has sourced our policy from version control and will enforce it on a run. Given the following simple Terraform configuration in a workspace:
resource "random_pet" "animal" {
length = 3
}
output "random" {
value = "${random_pet.animal.id}"
}
Our policy check passes:
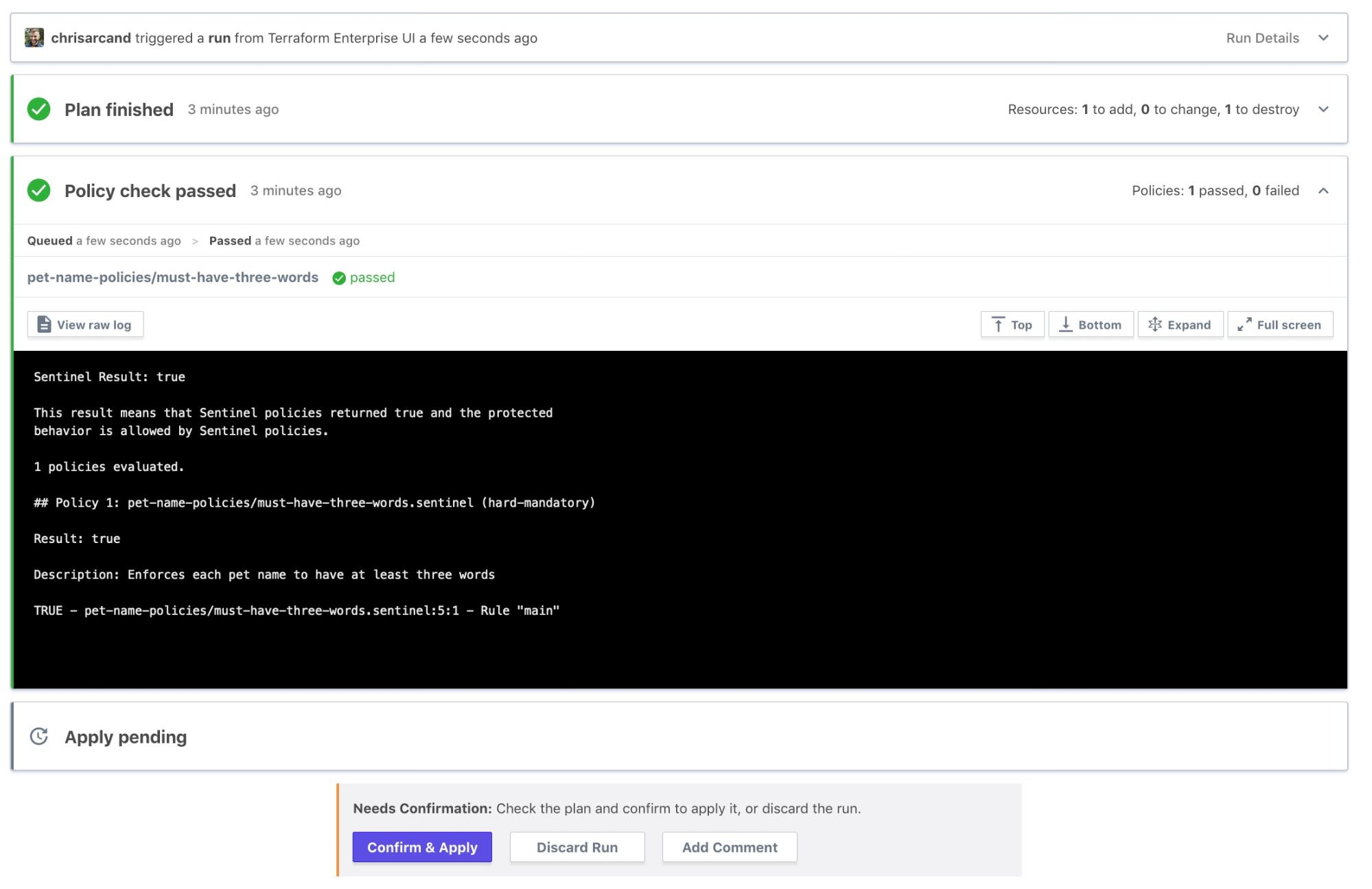
The policy ensures that the random_pet resources in this run are configured to yield at least three names, which are generated after the run is applied:
As commits are pushed and merged to our policy source, Terraform Enterprise will receive those changes automatically and use the latest version of our policy as it evolves in subsequent runs. If your VCS provider fails or you have a custom CI/CD pipeline, you can easily configure the policy set to manually create new versions via API and upload the policies and configuration file in a single tar file (tar.gz).
»Summary
With VCS integration and direct API uploads, versioned policy sets provide a first-class policy as code experience and are now the recommended way to manage Sentinel policies in Terraform Enterprise.
Versioned policy sets are now available in Terraform Cloud and will be available in the upcoming release of Terraform Enterprise. Documentation and further examples can be found in the Terraform Cloud Sentinel documentation. For more information on Terraform Cloud and Terraform Enterprise or to get started with your free trial, visit the Terraform product page.








