When the Cloud Native Computing Foundation (CNCF) Technology Radar team started work on its latest edition focusing on secrets management, they “expected the results to overwhelmingly show that organizations are using the offering of the public cloud they are already using,” recalled Steve Nolen, a site reliability engineer (SRE) at RStudio and a Radar team member, in the CNCF Radar report. But the survey results upended that expectation.
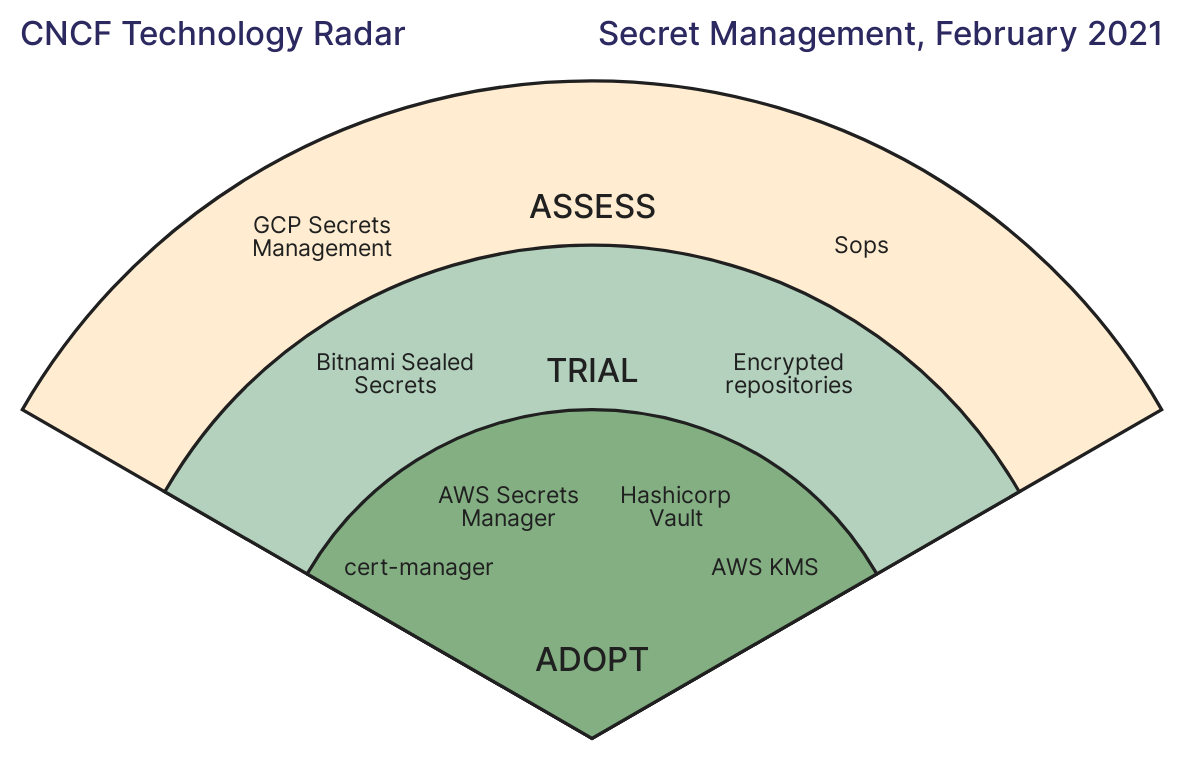
The survey asked CNCF end users what they currently use and recommend internally for secrets management, revealing HashiCorp Vault as the clear winner, garnering the most votes of any solution. Vault was one of only four products landing in the (highest) Adopt category, along with AWS Secrets Manager, AWS WS Key Management Service (KMS), and AWS Certificate Manager, and Vault was noted “to be popular with organizations using a cloud-agnostic or multi-cloud approach.”
»Vault: Broadest Adoption, Cloud Agnostic
The Radar report concludes that “Vault has the broadest adoption across many companies and industries.” Despite being a “rather complex tool,” the Radar team said its “broad adoption makes sense when you consider many smaller organizations likely would prefer to outsource their secrets management rather than creating and maintaining an in-house solution. This is backed up by our conclusion that commercial tools have a higher adoption rate since they remove the complexity of creating an in-house tool.”
In addition, Vault “addresses secrets management in a cloud-agnostic way. If an organization has a decent amount of information to protect and is not already locked into a cloud provider, Vault provides a comprehensive solution whose complexity is matched by a robust feature set.” Critically, “it also appears to be a convenient solution for multi-cloud environments,” the team added.
Note that when the CNCF conducted the secrets management Radar in February 2021, HCP Vault — the cloud-managed version of Vault — was still in beta. HCP Vault is now generally available to help companies that want to reduce complexity and workload by having HashiCorp manage the installation and operations of Vault.
»Why Now for Secrets Management?
The Radar team chose to investigate secrets management for a number of reasons: Radar team member Andrea Galbusera, Engineer and Co-Founder at AuthKeys, explained in a CNCF Radar video that “as soon as a company needs to automate its operation process, it needs to deal with how to store secrets. Secrets management is basically the set of techniques used for keeping those secrets safe, usually by storing them encrypted somewhere.”
In a podcast featuring the Radar team, The New Stack said that “secrets management tools are largely seen as essential in the DevOps world, especially whenever code and data are shared among software developers and in distributed working environments.” In that podcast, Nolen put it this way: “In the level of the technical world that we’re all kind of operating in, it’s pretty difficult to really do much of anything without secrets. Every company that’s building up a software stack and having interaction between those applications requires a pretty distinct need for secrets at all of these levels. And so, with secrets comes a requirement to manage them and hopefully manage them securely.” As for Vault, “it is really like the go-to, comprehensive, end-to-end, already-adopted, solution,” Nolen said.
»For Those Not Using Vault
“After Vault, groups tend to use the native solutions provided by their public cloud provider,” the Radar report concludes, which is “not surprising since it is much easier for an organization to use a service if that same provider is already managing the infrastructure.” Products such as AWS Secrets Manager, AWS Key Management Service, AWS Certificate Manager, Azure Key Vault, and Google Cloud Secret Manager, which all show up in the Radar report, “offer organizations tight integration loops with features,” the report says, but could lead to vendor lock-in.
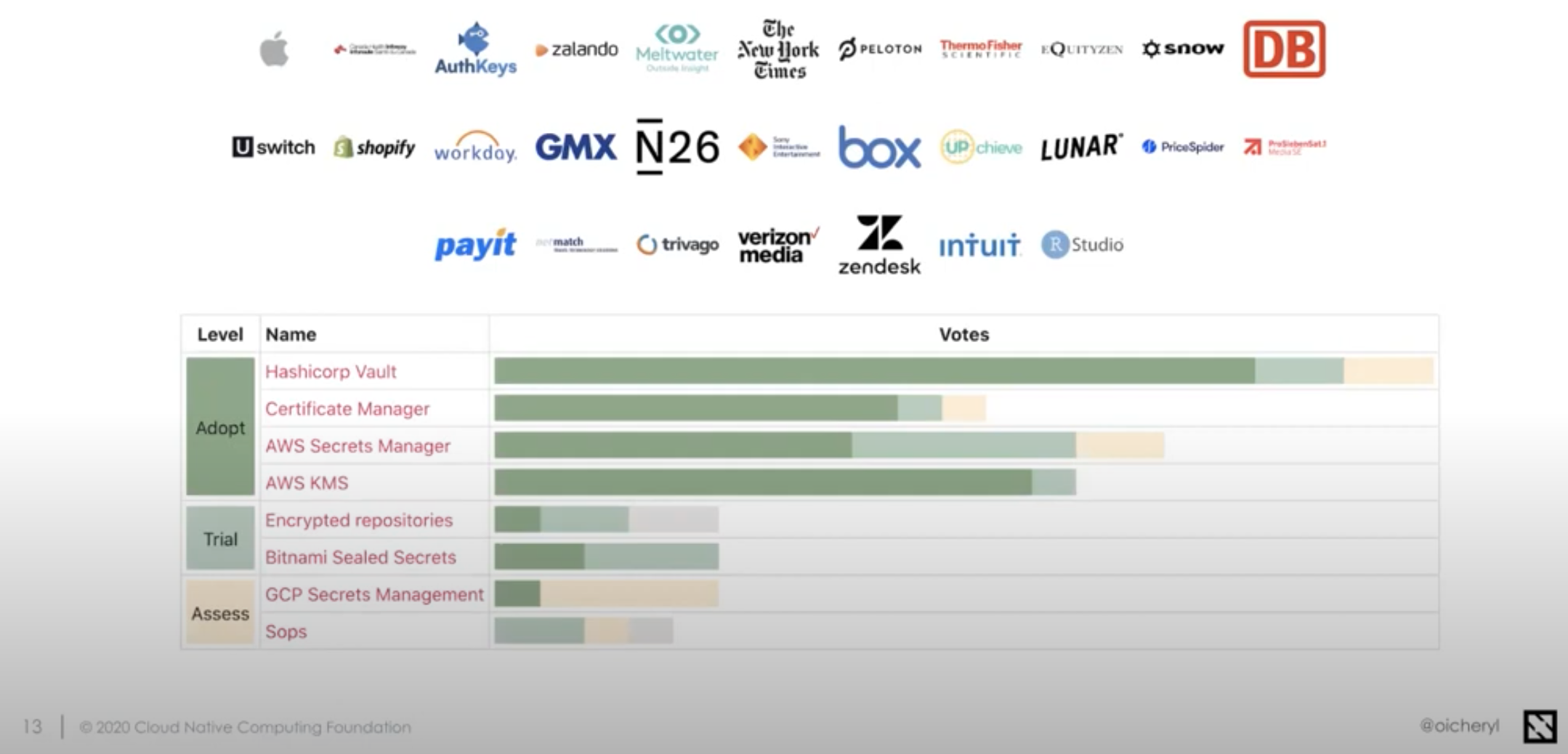
Dark green represents votes for Adopt, light green is Trial, beige is Assess, and gray is Hold, which does not figure in the final Radar report.
By contrast, “other solutions in the space are fragmented across various levels of maturity and complexity,” the Radar notes, and were often designed for more specific use cases like frameworks and encrypted files in Git repositories.” These tools “did not receive enough adoption/trial/asses votes to be included on the Radar.”
The exception was the relatively new Certificate Manager, which “saw high adoption among organizations using Kubernetes,” suggesting that “secrets management is top of mind ... for Kubernetes users.” Similarly, according to Galbusera speaking in the CNCF Radar video, homegrown secrets management solutions were not included in the Radar because they were too fragmented to treat as a single option.
»Learn More About CNCF Radar and HashiCorp Vault
The CNCF End User Technology Radar is a guide for evaluating cloud native technologies, on behalf of the CNCF End User Community. Intended for a technical audience, it places solutions at one of three levels, Assess, Trial, and Adopt. For more information on the CNCF Radar results and methodology, see the Secrets Management Radar announcement and the Radar home page. You can also watch this half-hour video that walks you through the entire process and conclusions of the secrets management edition of the CNCF Radar:
Users can download the open source version of Vault at vaultproject.io. For more information about Vault Enterprise, visit hashicorp.com/products/vault.








