It’s been another busy few months of Terraform Enterprise releases, with a collection of new features focused on manageability, flexibility, and efficiency.
The most significant update for operators was the introduction of flexible deployment options, which introduced new deployment capabilities on Docker Engine and cloud-managed Kubernetes services (Amazon EKS, Microsoft Azure AKS, and Google Cloud GKE). Along with the new lightweight single-container architecture, customers can reduce operational costs, complexity, and risk by choosing the platform that fits their organizational standards and preferences. Current Terraform Enterprise customers on Replicated-based installs should review the Migrating to Flexible Deployment Options guide to plan their migration because support for the Replicated deployment option will be removed in the future. Information about the support timeline for the Replicated Native Scheduler deployment option can be found on the Terraform Enterprise releases page.
Let’s review some of the other recent feature additions:
»Ephemeral workspaces
Unused or forgotten infrastructure can result in runaway costs for many organizations. These costs can be mitigated if administrators have effective methods to enforce time-to-live policies for infrastructure resources. Unused resources also represent potential attack surfaces for malicious actors. Therefore, removing unused workspaces is important not just for cost control, but for security purposes as well.
Terraform Enterprise v202310-1 now supports ephemeral workspaces, which allow customers to set timeouts that automatically destroy temporary resources. For administrators, this should eliminate a large amount of manual clean-up, reduce infrastructure costs, and further simplify workspace management and testing.
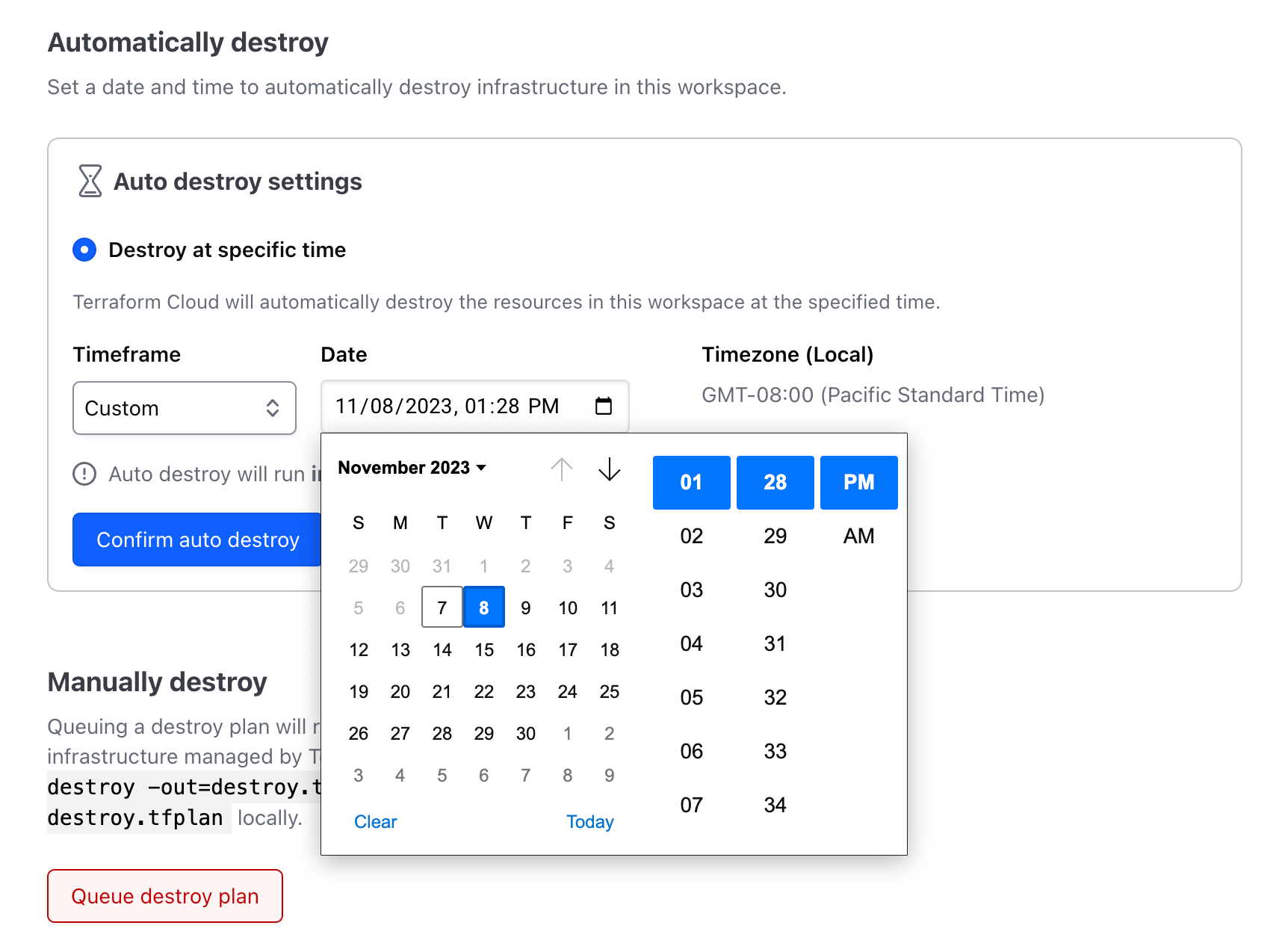
Auto-destroy settings can be found in workspace settings.
»Multiple dynamic provider configurations
Terraform Enterprise allows users to define multiple configurations for the same provider on a per-resource or per-module basis with aliases. However, with the original dynamic provider credentials releases, users could configure only one set of credentials per provider and workspace. This limitation hindered users who had multiple aliases for the same provider, as they couldn't fully embrace the benefits of the new authentication functionality.
Multiple configurations for dynamic provider credentials, available in v202308-1, resolves this issue by enabling workspace admins to authenticate multiple aliases of the same provider within a single workspace when provisioning infrastructure. This feature is especially useful when provisioning across multiple regions and accounts using unique credentials with different roles or permissions.
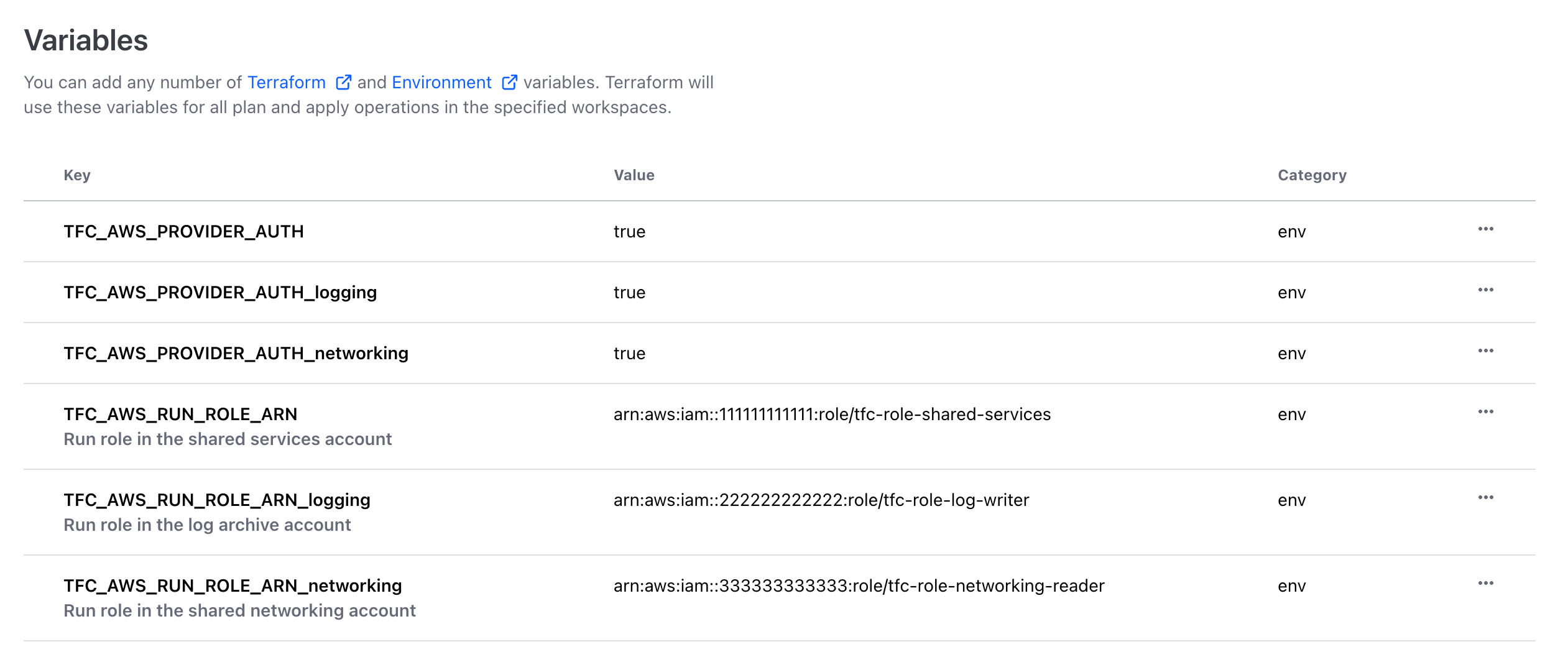
Environment variables assigned to a workspace enable dynamic provider credentials for multiple instances of the AWS provider with unique roles.
»Run data retention
Efficiently managing data is essential to maintaining a secure and scalable infrastructure. Over time, a Terraform Enterprise environment accumulates a large amount of data from past runs. This presents challenges from operational, cost, and data governance perspectives.
This latest enhancement in v202311-1 provides a configurable data retention policy for Terraform run data. With this feature you can manage the lifecycle of configuration version files and state files that are produced through the VCS, API, and CLI workflows. Administrators can easily configure how long data should be retained, and the data cleanup process is fully automated. The default retention policy is set at the organization level and can be overridden at the workspace level if needed. This feature reduces storage costs and mitigates compliance risks, enabling businesses to adhere to privacy regulations, industry standards, and internal policies, reducing the chance of penalties for non-compliance.
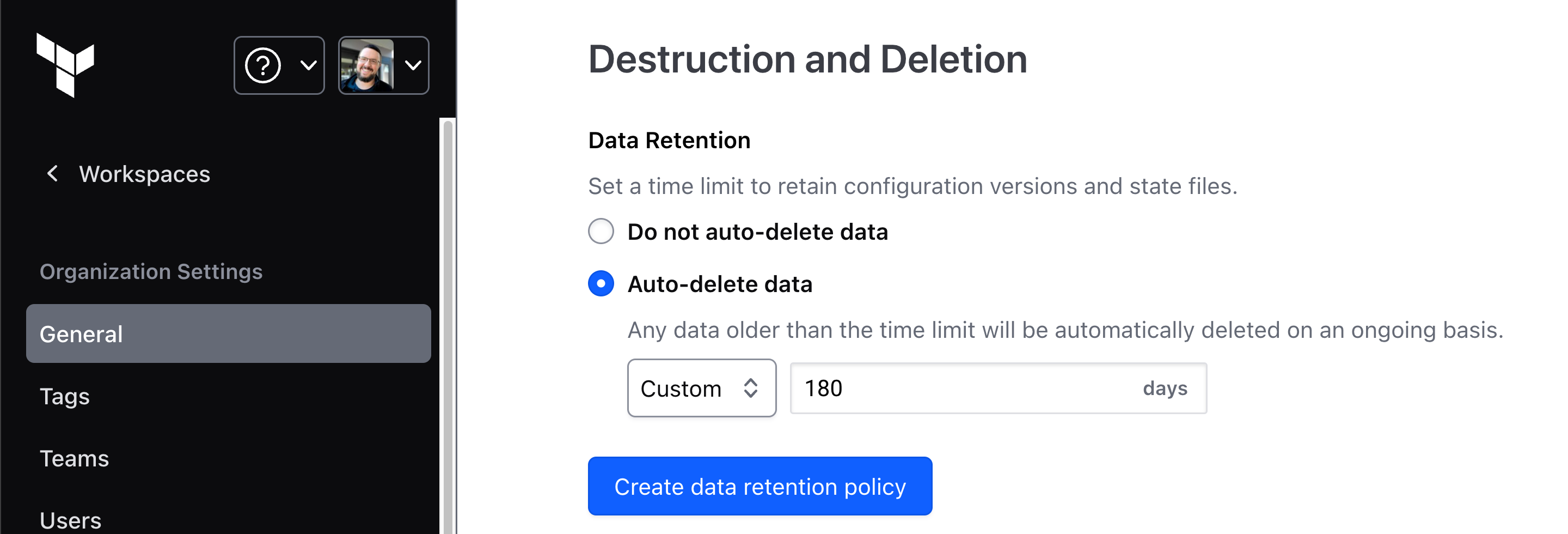
The organization default retention policy is configured in the General settings.
In v202311-1, the amount of data archived by Terraform plans is also dramatically reduced, resulting in an immediate improvement in disk space utilization on mounted disk installations or object storage utilization when services are externalized.
»Other enhancements and next steps
In addition to these new major features, Terraform Enterprise also now supports:
- Custom project permissions (v202308-1), enabling admins to create task-focused permission sets on a per-project basis to provide least privilege access to sensitive information.
- Policy set workspace exclusions (v202310-1), which provides the flexibility to exclude individual workspaces from global and project-scoped policy assignments.
- Organization default execution mode (v202310-1), a new organization-level setting to facilitate the scoping of agent pools for all new workspaces in environments that rely on agents to reach isolated network segments.
For more information about the latest releases of Terraform Enterprise, review the release notes in the Terraform Enterprise documentation. To learn more about Terraform Enterprise and get started, visit the Terraform product page or contact HashiCorp sales.








