Terraform modules on AWS allow practitioners to easily describe their infrastructure in terms of its architecture, rather than directly in terms of physical objects. Modules can be called multiple times, either within the same solution or in separate ones, helping practitioners quickly deploy Terraform-based deployments on AWS. Currently there are 15 modules available (all include the process to work with Terraform Cloud):
- terraform-aws-vpc
- terraform-aws-ecs-cluster
- terraform-aws-ecs-fargate
- terraform-aws-rds-aurora
- terraform-aws-globalnetwork
- terraform-aws-codestar
- terraform-aws-codebuild
- terraform-hashicorp-cloud_workspace
- terraform-aws-sqs
- terraform-aws-codecommit
- terraform-modules-examples
- terraform-aws-sns
- terraform-hashicorp-cts-alb_listener-nia
- terraform-aws-transit-gateway
- terraform-aws-label
Each of the Terraform modules on AWS include:
- Availability from registry.terraform.io and GitHub
- Getting started provisioning instructions
- A readme that details how the module can be imported into your Terraform files
In this post, we’ll walk through setting up and using the Amazon Virtual Private Cloud (VPC) for Terraform on AWS module.
»Deploying Your First Pattern on AWS
The Amazon VPC pattern allows you to set up a VPC that provides a networking foundation based on AWS best practices for your infrastructure. The VPC environment has both public and private subnets where you can launch AWS services and other resources based on this quickstart guide.
»Install Terraform
To deploy this module, do the following: Install Terraform. (See Install Terraform for a tutorial)
»Sign up for Terraform Cloud
This pattern uses Terraform Cloud. Sign up and log into Terraform Cloud here. (There is a free tier available)
»Configure Terraform Cloud API Access
Tip: If you are using a pre-12.21 version of Terraform, set up a CLI configuration file to authenticate.
In order to authenticate with Terraform Cloud, run the terraform login subcommand. Terraform will prompt you to confirm that you want to authenticate by typing yes in your terminal.
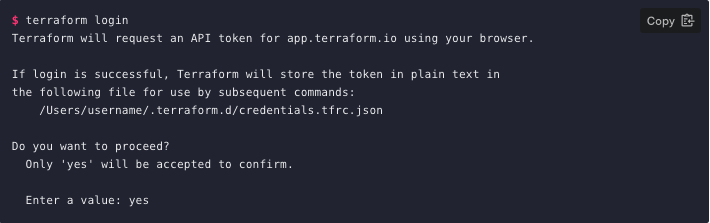
»Generate a Token
A browser window will automatically open to the Terraform Cloud login screen. Enter a token name in the web UI, or leave the default name, terraform login.
Tip: If your browser doesn't open automatically, navigate to the URL output in your terminal or click here to be taken to the token creation UI.
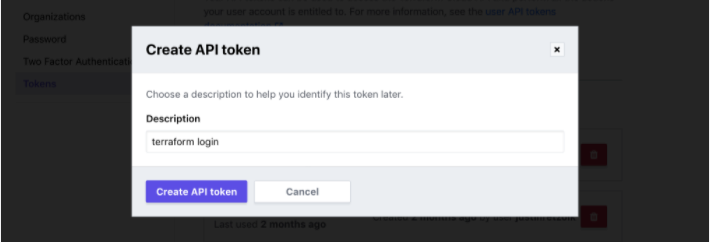
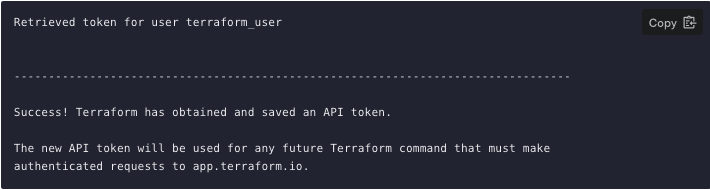
Click "Create API token" and Terraform Cloud will generate the authentication token.
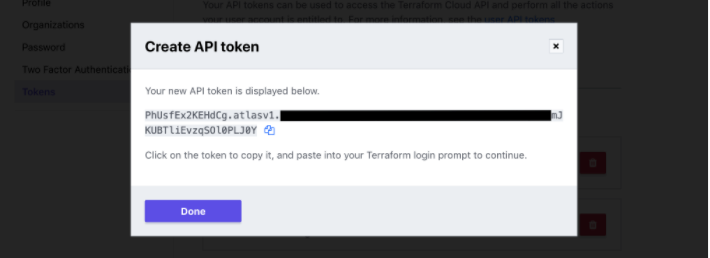
Save a copy of the token in a secure location. It provides access to your Terraform Cloud organization.
»Add the Token to the CLI
Your terminal will prompt you for the generated user token.
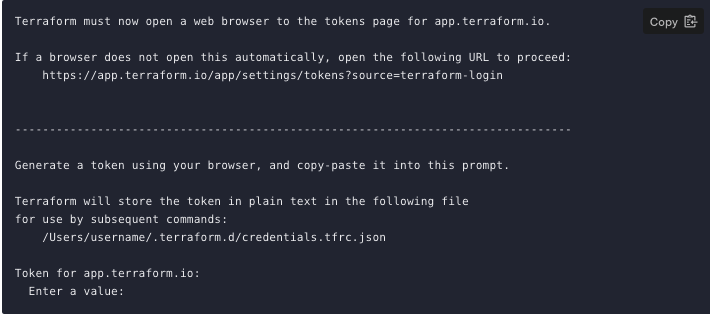
Paste the user token exactly once into your terminal. Terraform will hide the token for security, so when you paste it in you will not see it. Press Enter and you will now have access to the Terraform Cloud backend.
»Deploy Your First Module (Linux or macOS)
To get started as quickly as possible with the module, we have created a workflow that automatically sets up workspaces with Terraform Cloud so that you can run the VPC deployment within a workspace.
»Credential Handling
Now export the Terraform Cloud credentials to a local host variable to use for this session. Here’s the command:
export TERRAFORM_CONFIG="$HOME/.terraform.d/credentials.tfrc.json"
Now we need to create a configuration that will populate the variables used in the module. This is done by using a tfvars file like so:
Example filepath = $HOME/.aws/terraform.tfvars
Example tfvars file contents
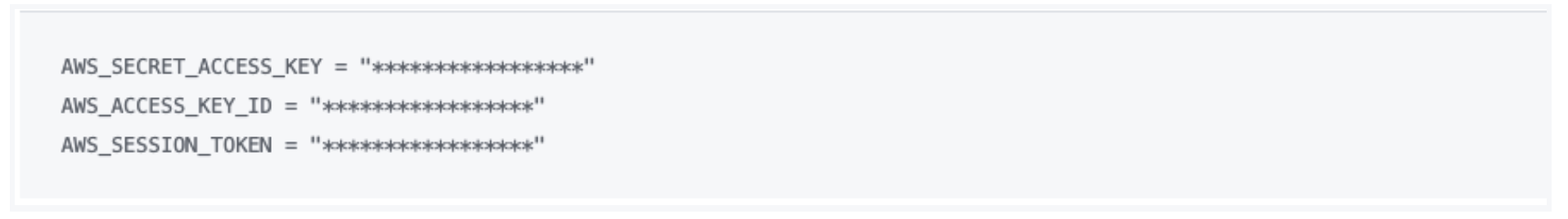
Replace *** with AKEY and SKEY
NOTE: STS-based credentials are optional but highly recommended.
CAUTION: Make sure your credentials are secured outside version control and follow secrets management best practices.
»Module Deployment
Now that we have the basics covered, we can deploy this module. These instructions are for Linux or macOS based machines.
First, clone the aws-quickstart/terraform-aws-vpc repository.
git clone https://github.com/aws-quickstart/terraform-aws-vpc
Move from your current directory to the root directory.
cd terraform-aws-vpc/
Switch into the workspace directory.
cd setup_workspace
Run these two commands to build the workspace in Terraform Cloud and create your remote file.
terraform init
terraform apply
NOTE: If you run
terraform applywithout thetfvarsfile you will have to manually add your credentials into the newly created environment vars in Terraform Cloud or in thevariables.tffile in this directory.
Alternatively, you can use the tfvar file to populate the variables in the variable.tf file.
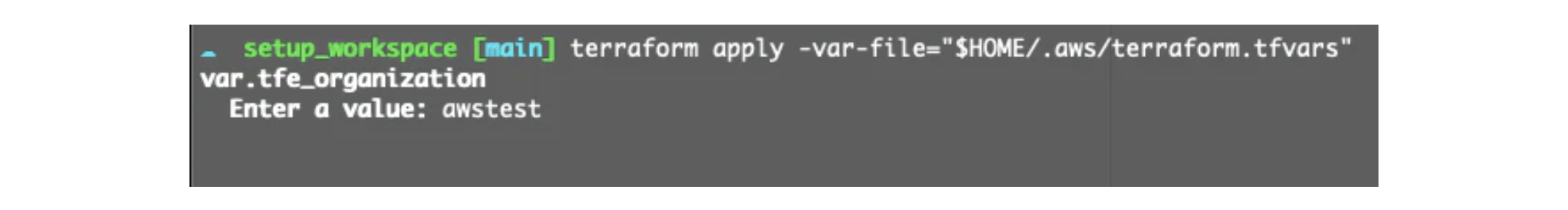
terraform apply -var-file="$HOME/.aws/terraform.tfvars"
If you use that command you will be prompted to create an organization name to use in Terraform Cloud or you can press Enter to auto-generate a name.
Next, confirm the plan.
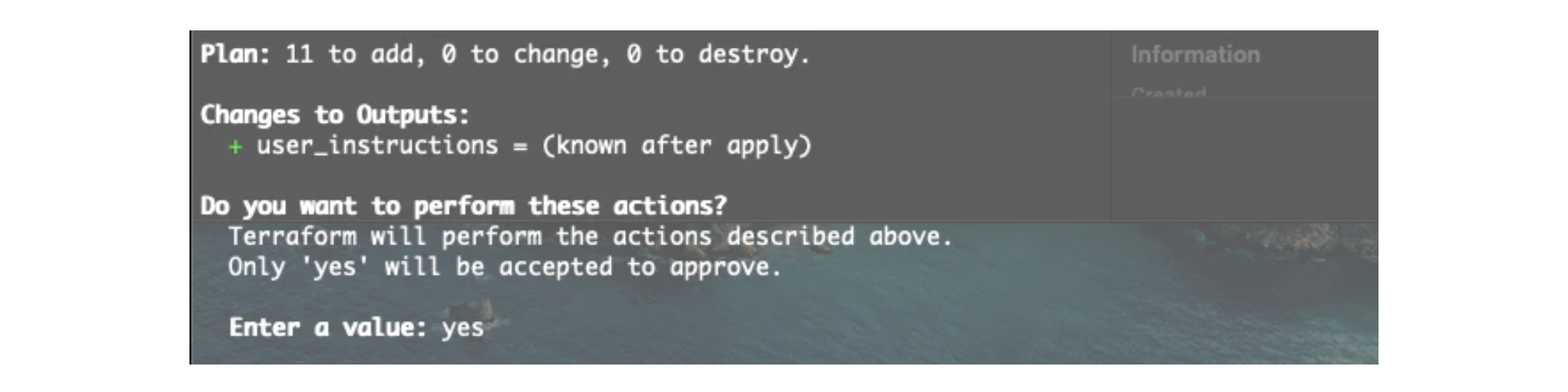
Once complete you will see this output message.
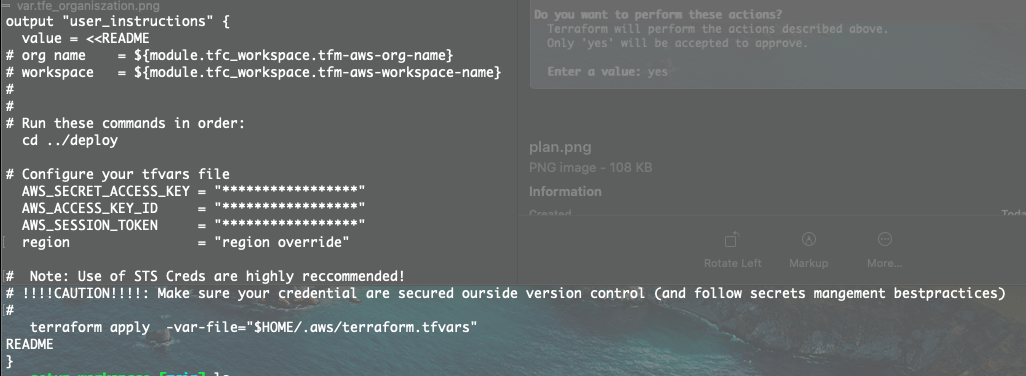
Next, move into the deploy directory. There, the previous command auto-generated a backend.hcl file, which will allow you to run the VPC build in Terraform Cloud.
cd ../deploy
terraform apply
Again, you can alternatively use the tfvar file to populate the variables in the variable.tf.
terraform apply -var-file="$HOME/.aws/terraform.tfvars"
The terraform apply is run remotely in Terraform Cloud and will end with the following outputs:
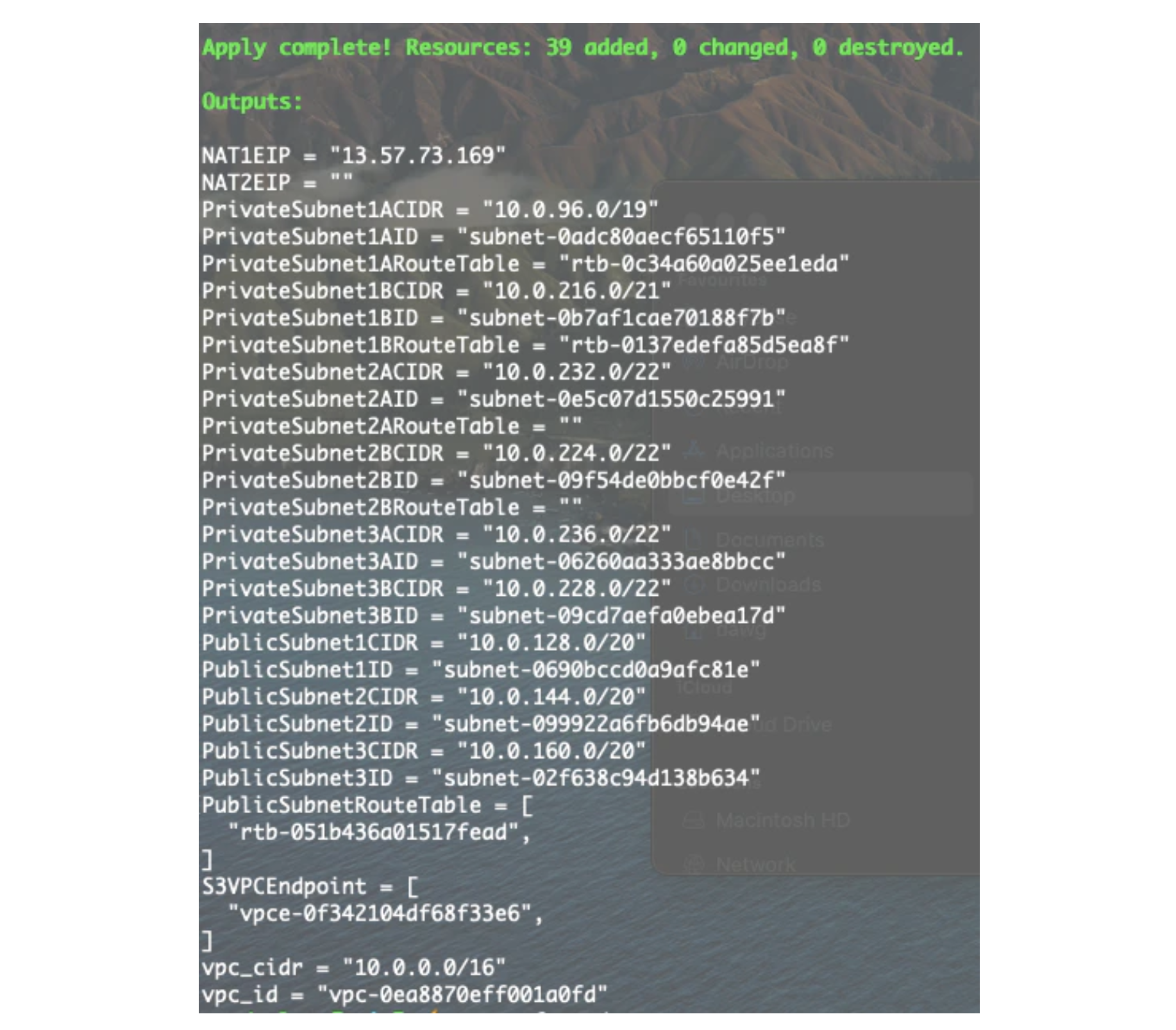
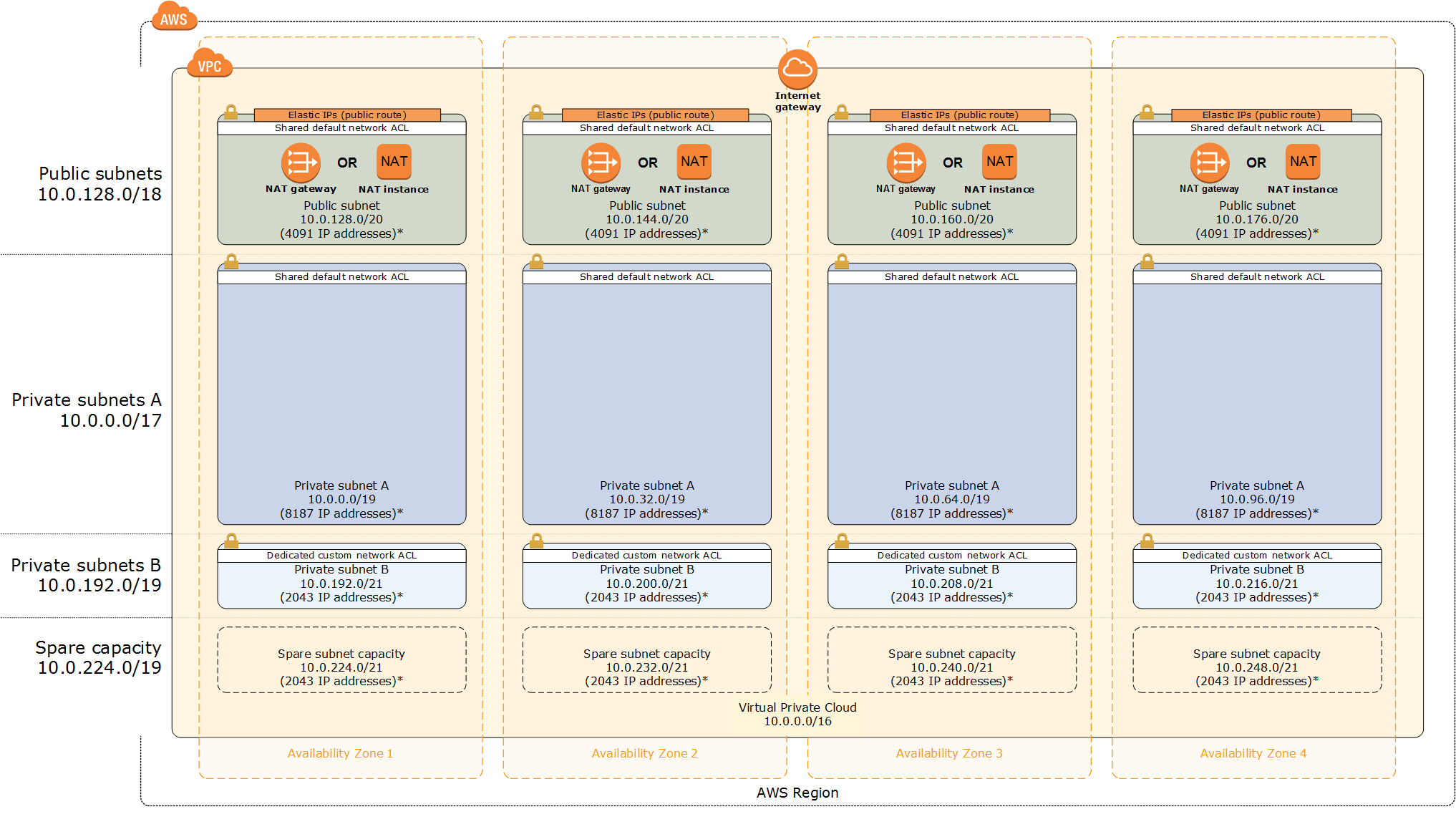
Once Terraform finishes, you will have created a VPC setup in your account that is illustrated in the diagram below. This deployment is based on the best practices outlined in this AWS quickstart deployment guide.
»Additional Information
Terraform modules on AWS are published under an open source license with the source code available on GitHub. Terraform modules on AWS are currently available as a developer preview and on the Terraform registry.
Terraform Cloud is free for up to five users and organizations can upgrade to the Team & Governance or Business tiers at any time. To get started, sign up for Terraform Cloud and follow our Getting Started tutorial or contact HashiCorp Sales.








