HashiCorp Terraform configuration often includes sensitive inputs, such as passwords, API tokens, or Personally Identifiable Information (PII). Terraform provides several features to help avoid accidentally exposing sensitive data.
Learn to Protect Sensitive Inputs
Follow our new tutorial on HashiCorp Learn, Protect Sensitive Input Variables. In this tutorial, you will provision a web application using Terraform, and use the `sensitive` variable flag to set sensitive values. You will also learn about ways to manage sensitive values in your Terraform state.
Use the “sensitive” Flag
New in Terraform 0.14, input variables now support the `sensitive` flag. Terraform will redact the values of sensitive variables in console and log output, to reduce the risk of accidentally disclosing these values.
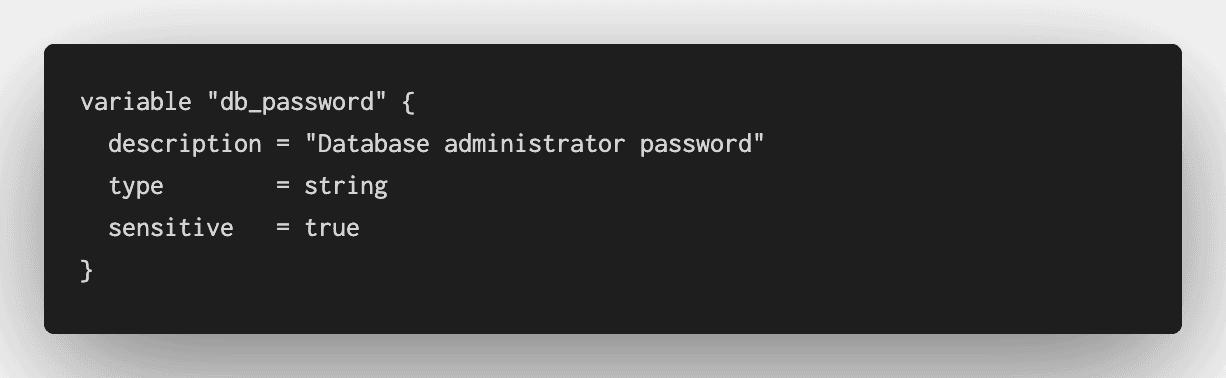
When you apply this configuration, Terraform redacts the sensitive value from its console output.
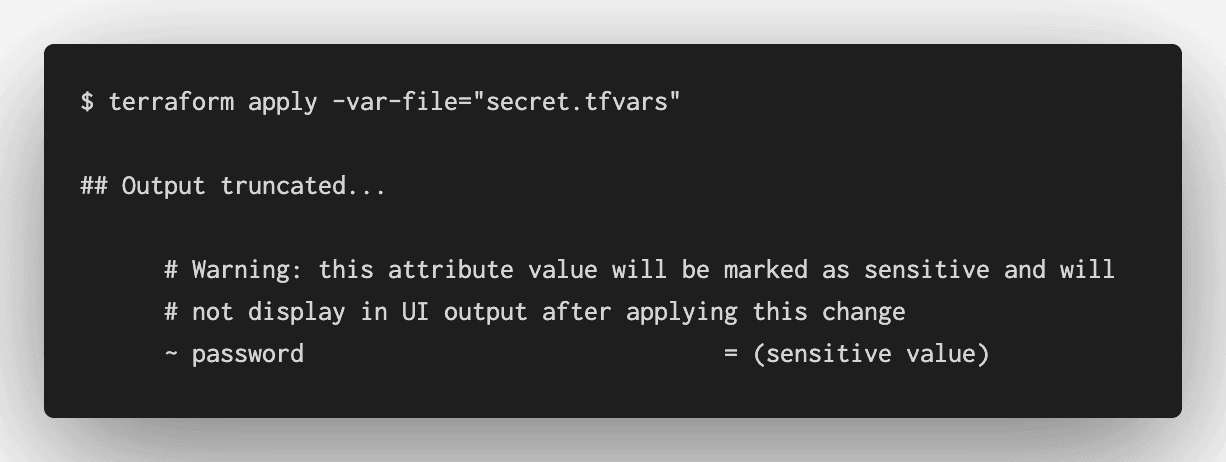
This feature helps prevent accidental disclosure of sensitive values, but is not sufficient to fully secure your Terraform configuration.
Secure Terraform State
Even when a variable is marked sensitive, Terraform still needs to store the value in its state file, so that it can correctly apply configuration changes.
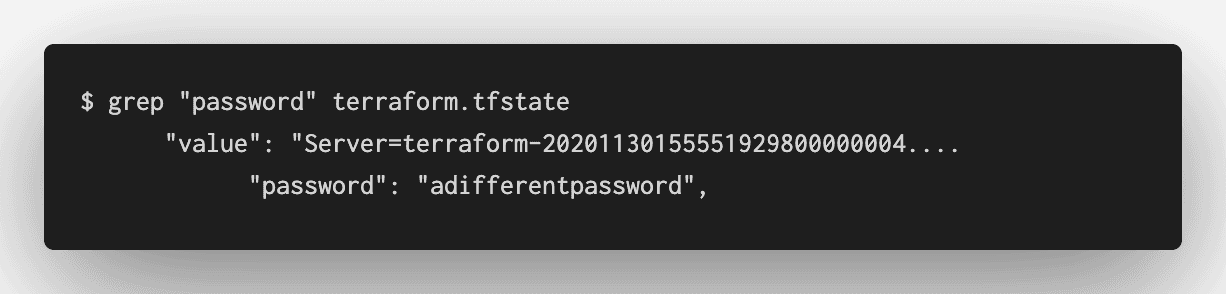
In this tutorial, you will learn about several methods that Terraform and other HashiCorp products provide to secure your state file.








