We are excited to announce the general availability of HashiCorp Vault 1.5. Vault is a tool which provides secrets management, data encryption, and identity management for any application on any infrastructure.
Vault 1.5 focuses on improving Vault’s core workflows and integrations to better serve your use cases. In this release, we added additional telemetry metrics and released a Splunk monitoring app, expanded support for running Vault in Kubernetes via OpenShift, and added a major new feature called Resource Quotas for protecting against distributed denial of service (DDoS) attacks.
This release includes the following key features and improvements:
- Monitor Telemetry and Log Data with Splunk: We released a Splunk App for Vault Enterprise customers. The app is accompanied by an updated monitoring guide and new telemetry metrics to enable more users to better monitor Vault.
- Resource Quotas: Vault now supports specifying a quota to rate limit requests on Open Source and Enterprise. Enterprise customers also have the ability to set quotas on the number of leases that can be generated on a path.
- Red Hat OpenShift Support: We have updated the Helm charts to allow users to install Vault onto their OpenShift clusters.
- Integrated Storage as HA Storage: It is possible to use Integrated Storage as HA Storage by using a different storage backend as regular storage.
- Replication UI Improvements: We have redesigned the replication UI to highlight the state and relationship between primaries and secondaries nodes in the cluster and improved management workflows, enabling a more holistic understanding of multiple Vault clusters.
- VMware and NetApp Certifications: Vault has successfully completed product compatibility validations for both VMware vSphere and NetApp ONTAP for use as an external key manager solution using the built-in Key Management Interoperability Protocol (or KMIP) standard.
This release also includes additional new features, workflow enhancements, general improvements, and bug fixes. The Vault 1.5 changelog provides a list of all changes.
»Monitoring Telemetry & Log Data with Splunk
We released a Splunk application for Enterprise to help users with an out-of-box Vault monitoring experience. The application helps you understand how Vault is doing from an operational and security perspective in a multi-tenant environment, and comes with seven sample dashboards that span various monitoring use cases. It is also accompanied by an updated Performance Tuning Guide that includes recommendations on the most important metrics to be monitored, why they are important to be monitored, their critical thresholds, and more. You can read more about HashiCorp and Splunk working together over on their blog post.
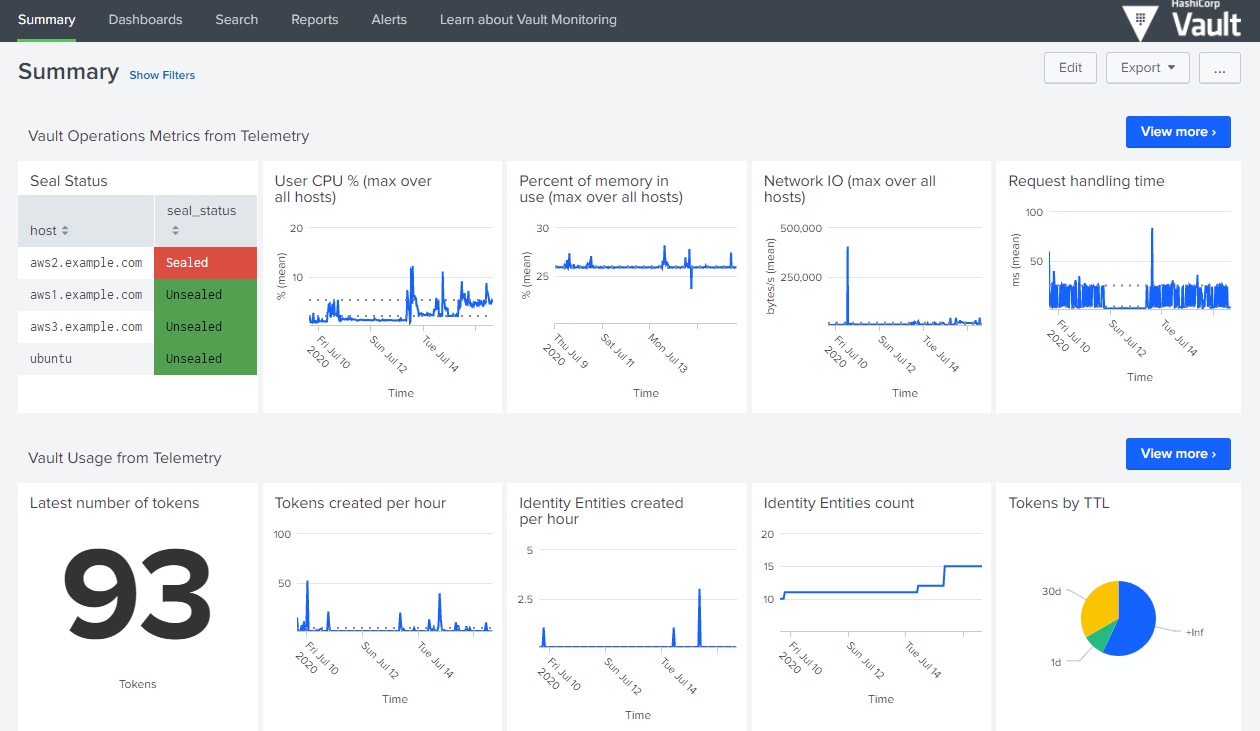
Vault Enterprise users can complete the Splunk app request form to request access to the app.
For more information on the Monitoring Vault with Splunk, please see our dedicated release announcement, updated performance tuning guide, and a detailed learn guide.
»Resource Quotas
Vault 1.5 introduced resource quotas to protect your Vault environment's stability and network, as well as storage resource consumption from runaway application behavior and distributed denial of service (DDoS) attack. The Vault operators can control how applications request resources from Vault, and Vault's storage and network infrastructure by setting the following:
- Rate Limit Quotas: Limit maximum amount of requests per second (RPS) to a system or mount to protect network bandwidth
- Lease Count Quotas (Vault Enterprise only): Cap number of leases generated in a system or mount to protect system stability and storage performance at scale
For more information on Resource Quotas, please see our dedicated release announcement, documentation, and a detailed Learn Guide.
»Red Hat OpenShift Support
We have updated our Kubernetes Helm chart with support for Red Hat OpenShift. The Vault Helm chart is the recommended way to install and configure Vault on OpenShift. In addition to running Vault itself, the Helm chart is the primary method for installing and configuring Vault Agent Injection Mutating Webhook.
For more information on Red Hat OpenShift support via the Helm chart, please see our dedicated release announcement, documentation, and a detailed Learn Guide.
»Integrated Storage as HA Storage
We initially introduced Integrated Storage in Vault 1.2, which allows Vault admins to configure an internal storage option for storing Vault’s persistent data, rather than using an external storage backend.
In most scenarios, you would configure your Vault server nodes to use a storage backend that supports high availability (HA), therefore the storage backend stores the Vault data while maintaining the HA coordination. However, not all storage backends support HA (for example, Amazon S3, Cassandra, MSSQL). In some cases, you may need to use a storage backend that does not have HA support which means that you can only have a single-node Vault deployment instead of an HA cluster.
To solve this problem, Vault 1.5 now has the option to specify integrated storage as the HA coordination option for Vault, when any durable data storage backend is used.
For more information on Integrated Storage as HA Storage, please see our documentation, and a detailed Learn Guide.
»Replication UI Improvements
Replication is a Vault Enterprise feature, with two use cases: disaster recovery and performance replication. Disaster recovery replication is meant to protect against a failure of entire clusters, while performance replication is built to distribute a high-volume workload.
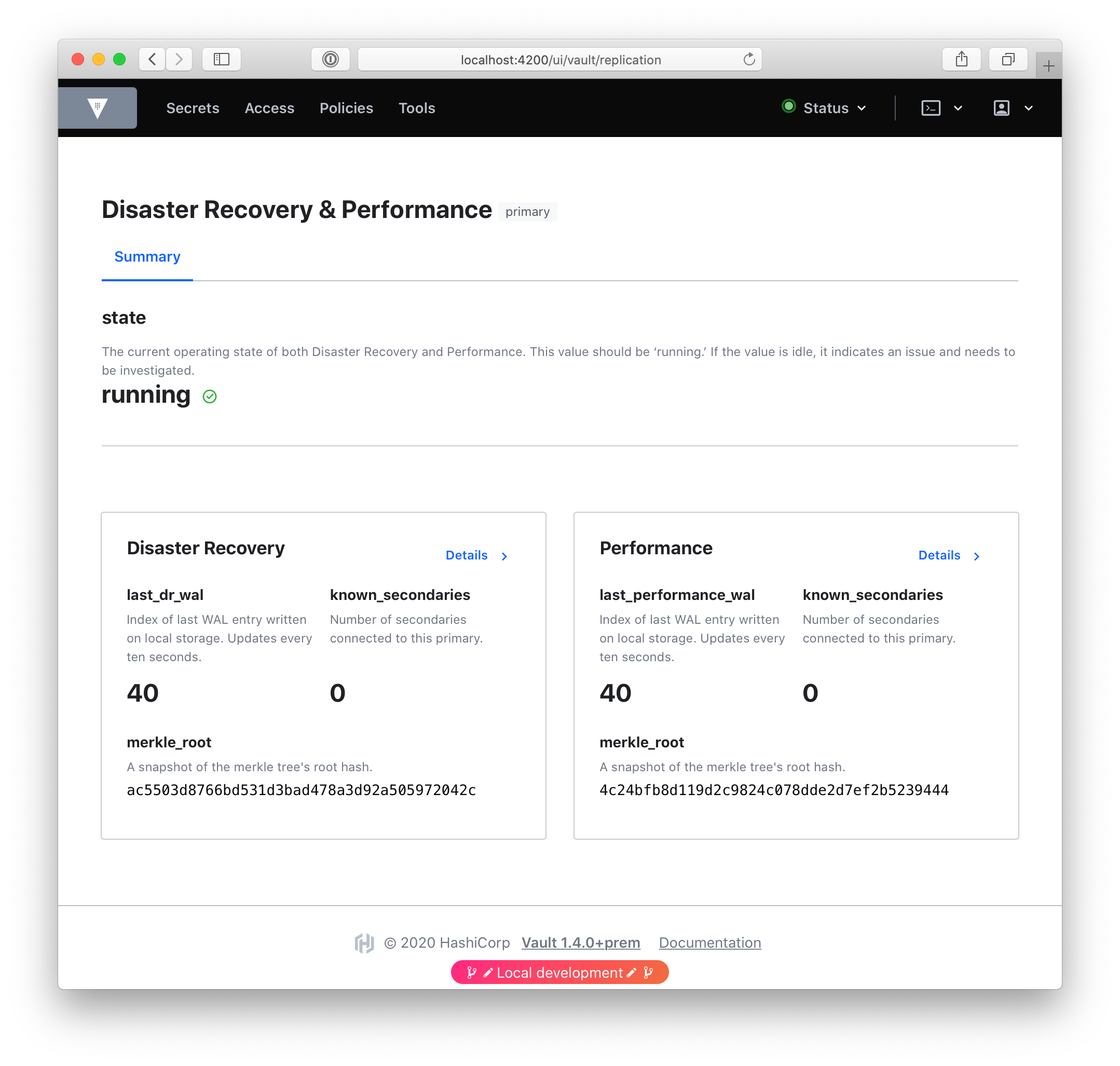
In both instances, it is important to be able to monitor the health of both the primary and secondary clusters, be made aware of potential issues and ways to address those issues, and note the connections between clusters. In Vault 1.5, we redesigned the replication UI to create dashboards that are easy to read, easy to parse, and make problems easier to see and troubleshoot. We are eager to share our redesigned dashboards with you.
For more information on the replication UI improvements, please see our behind the scenes redesign announcement, documentation, and a detailed guide on Monitoring Vault Replication.
»VMware and NetApp Certifications
Vault Enterprise successfully completed product compatibility validations for both VMware vSphere and NetApp ONTAP. You can use Vault Enterprise as a flexible, very cost-effective, and scalable external key manager solution using the built-in Key Management Interoperability Protocol (or KMIP) standard for securing and encrypting storage systems.
If you would like to learn more, we have released two new white papers that highlight these certified integrations:
- HashiCorp Vault Enterprise Securing VMware Data Whitepaper
- HashiCorp Vault Enterprise Securing NetApp Data Whitepaper
For more information on the KMIP Secrets Engine, please see our documentation, or a detailed Learn Guide.
»Other Features
There are many new features in Vault 1.5 that have been developed over the course of the 1.4.x releases. We have summarized a few of the larger features below, and you can consult the changelog for full details:
- Vault Monitor: Similar to the monitor command for HashiCorp Consul and Nomad, we added a new “vault monitor” command, which lets users stream logs of a running Vault server. The log level selected can be different from the log level used by the server logs.
- Seal Migration: We have made updates to allow migrations from auto unseal to Shamir unseal.
- Namespace support for SSH helper: Vault now has an option to allow users to specify the namespace of the SSH mount when using the SSH helper.
- Password Policies: Vault now allows operators to customize how passwords are generated for select secret engines (OpenLDAP, Active Directory, Azure, and RabbitMQ).
- AWS Secrets Groups Support: IAM users generated by Vault may now be added to IAM Groups.
- AWS Auth Web Identity Support: We've added support for AWS Web Identities, which will be used in the credentials chain if present.
- OIDC Auth Provider Extensions: We've added support to OIDC Auth to incorporate IdP-specific extensions. Currently this includes expanded Azure AD groups support.
- GCP Secrets: Support BigQuery dataset ACLs in absence of IAM endpoints.
- Static Credential Rotation Support for MS SQL Server: Vault now allows static credential rotation for MS SQL.
»Upgrade Details
Vault 1.5 introduces new functionality. As such, we provide Vault 1.5-specific upgrade notes.
As always, we recommend upgrading and testing this release in an isolated environment. If you experience any issues, please report them on the Vault GitHub issue tracker or post to the Vault discussion forum. As a reminder, if you believe you have found a security issue in Vault, please responsibly disclose by emailing security@hashicorp.com and do not use the public issue tracker. Our security policy and our PGP key can be found here.
For more information about Vault Enterprise, visit hashicorp.com/products/vault. Users can download the open source version of Vault at vaultproject.io.
We hope you enjoy Vault 1.5.








