Today at HashiConf Global, we are pleased to announce the general availability of HCP Boundary, a fully managed version of HashiCorp Boundary available as a service on the HashiCorp Cloud Platform (HCP). Boundary was first released as an open source project in October 2020 to help organizations securely access critical systems remotely with fine-grained authorizations based on trusted identities. The general availability of HCP Boundary builds on June's HCP Boundary beta release to now offer a production-ready managed offering for remote access in cloud-based zero trust security architectures.
HCP Boundary provides a consistent workflow for securing access to infrastructure in ephemeral cloud environments without exposing your network or host credentials to users. The combination of Boundary, HashiCorp Vault, and HashiCorp Consul creates a cloud-managed, zero trust security solution for customers to authenticate identities for applications, networks, and people. A zero trust security approach is increasingly critical to protect the growing number of dynamic multi-cloud and hybrid environments where legacy security approaches may no longer be effective. This helps ensure that everything — from people to machines to services — is authenticated, every action is authorized, and that data is always protected.
»Part of HashiCorp's Zero Trust Security Solution
According to HashiCorp’s 2022 State of Cloud Strategy Survey, 81% of enterprise technology practitioners and decision makers already use or will be using multiple clouds within the next 12 months. Unsurprisingly, security remains top of mind: 89% of respondents said security is a key driver of cloud success. However, many organizations still struggle to secure growing attack surfaces across complex on-premises and multi-cloud environments where there is no clear network perimeter, infrastructure is continuously deployed, and network addresses are constantly changing.
A zero trust security approach addresses these issues by making sure that anything or anyone trying to gain access to the network is authenticated and authorized. The key is to implement unified identity-based access controls, where every logical entity — machine or human, from web apps and load balancers to DevOps personnel and remote users — has an identity that must be authenticated across platforms.
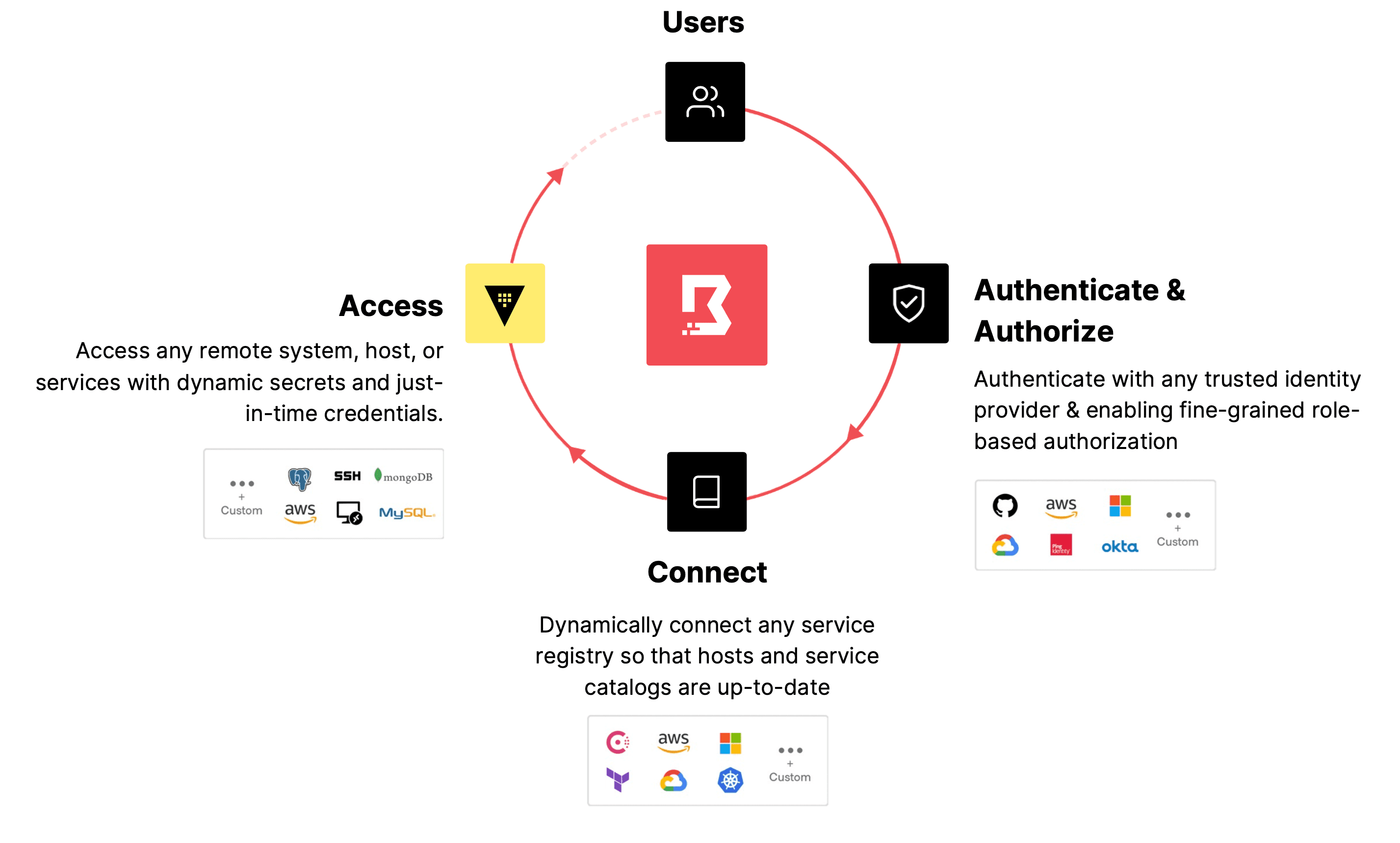
HashiCorp’s zero trust security solution is built for today’s threat landscape, unifying all these identities to safeguard the entire organization. Vault acts as the foundational piece, brokering identities and secrets across applications, networks, and users throughout even the most complex infrastructures. Boundary authenticates and authorizes users through integrations with existing identity providers (IDPs) such as Okta, Azure Active Directory, and GitHub to facilitate secure remote access without the need to distribute and issue credentials or exposing networks or other resources. Consul, meanwhile, leverages identity to safeguard the network by acting as a system of record for authenticating and authorizing access between applications and services while securing traffic and data across clouds and datacenters.
»HCP Boundary’s Critical Role in Zero Trust Security
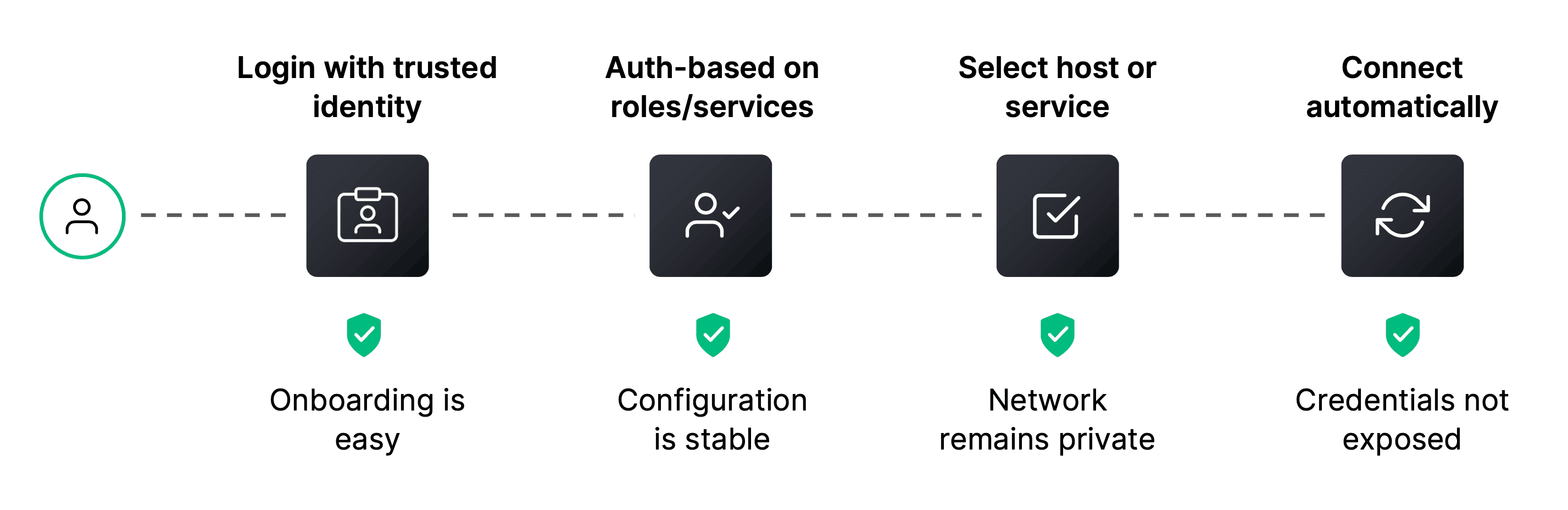
HCP Boundary bolsters zero trust security with an automated workflow that gives users easier remote access to critical infrastructure. It automates user and target onboarding — including the session connection, establishment, and credential issuance and revocation — which dramatically minimizes the configuration overhead for operators. And unlike traditional access solutions (such as privileged access management, or PAM), HCP Boundary makes it easy for operators to keep users and targets up-to-date in cloud environments. Because Boundary doesn’t actually bridge the client onto the private network, it can do all of this without ever having to expose the underlying network to users.
Built on the foundation of open source Boundary, HCP Boundary expands on key access workflows with enterprise capabilities, such as dynamic credential injection for user sessions, through a seamless integration with Vault. If users seek to access a target system through Boundary, Vault injects single-use, just-in-time credentials for passwordless authentication to the remote host, minimizing the likelihood of a credential leak as secrets are never exposed to the end user or outside actors.
As a Software-as-a-Service (SaaS) solution, HCP Boundary combines a single-click deployment experience with the operational hardening of a production service — including enterprise support, security hardening, and service level agreements (SLAs) for service availability.
»Getting Started with HCP Boundary
HCP Boundary is engineered to minimize the steps required to use Boundary in cloud environments. At a high level, users need to complete three tasks to start using HCP Boundary:
- Create: Create a HashiCorp Cloud Platform account.
- Deploy: Select HCP Boundary from the HCP dashboard.
- Connect: Connect to an initial infrastructure target.
To help users get started, we have created a series of HashiCorp Learn guides to HCP Boundary to provide guidance on executing these steps.
»Next Steps
We are excited about the general availability of HCP Boundary, now ready for use in production environments. With HCP Boundary, organizations can let HashiCorp assume responsibility for maintaining, monitoring, and scaling their Boundary deployments. It also lets teams take advantage of additional enterprise capabilities that simplify observability — like audit log streaming — and advanced secrets management functionality — such as credential injection — through Boundary’s integration with Vault.
We recommend creating an HCP account and trying HCP Boundary today: the first 50 sessions are free to help organizations easily get started securing remote access for their users. For more information on how Boundary provides secure remote access built for the cloud, read the HCP Boundary press release. For more details on HCP Boundary and pricing, please visit the Boundary product page or sign up through the HCP portal.








