HashiCorp is excited to announce the general availability of version 2.5 of the ServiceNow Service Catalog for Terraform, now with the ability to provision no-code workspaces through the Service Catalog. This release represents another step forward in our effort to streamline processes and promote broader adoption to organizations with many ServiceNow-provisioned workspaces. These enhancements empower customers to not only securely connect external applications to ServiceNow but also provision resources with Terraform in a simpler way. The 2.5 release has been certified for the latest “Washington DC” ServiceNow server version.
Important new features in the ServiceNow Service Catalog 2.5 include:
Let’s run through what’s new:
»Support for no-code modules
Version 2.5 of the ServiceNow Service Catalog for Terraform introduces a streamlined solution for Terraform customers when provisioning infrastructure.
Previously, customers were required to connect at least one VCS (version control system) repository to their ServiceNow instance to order infrastructure through the Terraform Catalog. The updated version of the Terraform plugin gives ServiceNow administrators an option of linking Catalog Items in the Terraform Catalog to no-code modules in the HCP Terraform private registry instead of directly connecting to VCS branches. This feature opens up a new avenue for creating Terraform workspaces and provisioning infrastructure using no-code modules, empowering users to seamlessly deploy pre-approved modules without writing any Terraform code. Moreover, the updated plugin offers greater control over the release process by allowing users to upgrade previously created no-code workspaces when a new version of the no-code module becomes available.
No-code modules are published in the Terraform private registry, providing an additional layer of abstraction. The no-code solution promotes a self-service model by allowing users to provision infrastructure without having to write any code. There are two personas associated with this feature: the module author, who is responsible for writing the underlying Terraform configuration and having it published as a no-code module, and the end user, who supplies any input variables or other appropriate configuration for the infrastructure to be provisioned via ServiceNow.
The two-part solution provides two new Catalog Items:
- Provisioning a no-code workspace and deploying resources, which automatically creates and initiates a Terraform run in a new no-code workspace, reporting results and output to ServiceNow.
- Updating a no-code workspace and deploying resources, which updates and triggers a Terraform run in an existing no-code workspace upon a new module version release, reporting output to ServiceNow.
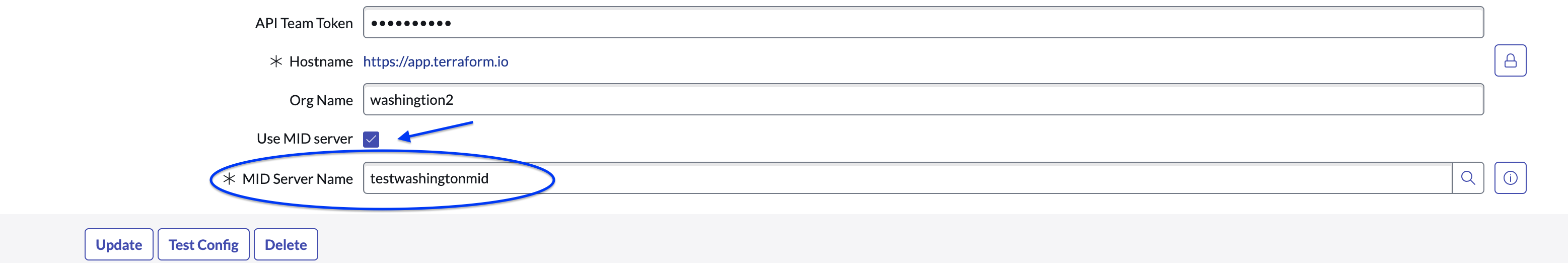
»Simplified MID server configuration
Streamlining MID Server routing has long been a highly requested feature. The previous solution for streamlining MID Server routing involved manually configuring and updating each type of API request sent to HCP Terraform or Terraform Enterprise through an MID server.
The Management, Instrumentation, and Discovery (MID) server is a Java application that enables communication and movement of data between ServiceNow and external applications. This enhances security posture and compliance. We have streamlined the MID server update process for enhanced traffic routing, particularly benefitting customers operating Terraform Enterprise behind a firewall.
The latest improvements include the addition of a checkbox option to use an MID server and a name field with a drop-down list of MID servers available to the application’s configuration form, transforming the previously manual and repetitive process into a one-time, one-click setup step.
»Key benefits
The general availability of the latest version of ServiceNow Service Catalog for HCP Terraform and Terraform Enterprise lets users provision infrastructure powered by no-code modules published in their organization’s private registry and provides a convenient way to route Terraform requests through a MID server. That brings three main benefits:
- Improved efficiency: Customers are now able to provision infrastructure without connecting to a version control repository, thus providing greater flexibility. Additionally, customers no longer need to manually enable API endpoints to use a MID Server, they can now use the checkbox, which is part of the configuration UI.
- Reduced risk: By implementing no-code integration, organizations can reduce their reliance on version control repositories, making them optional rather than mandatory for ServiceNow infrastructure provisioning. This approach eliminates the risk of subjecting Terraform workspaces to automatic, potentially unwanted updates with every commit to the branch, providing greater control and stability over the release process. In addition, simpler MID server enablement eliminates the error-prone task of manually updating API endpoints, reducing the chance of human error.
- Enhanced security: Users are now empowered to request infrastructure powered by no-code modules published securely in their organization's private registry, which helps ensure that sensitive information remains under the organization's control. Streamlining the MID server configuration process benefits Terraform Enterprise customers operating behind a firewall by reducing the risk of data breaches and making it easier for organizations to meet compliance standards.
»Connect your ServiceNow instance to HCP Terraform
Integrating your ServiceNow instance with HCP Terraform is simple thanks to robust APIs that enable smooth data exchange and workflow automation between the two platforms.
For more details and to learn about all of our enhancements in ServiceNow Service Catalog for Terraform 2.5, please review the Service Catalog configuration documentation.
Additional resources for your integration journey include:
- Install the Terraform app from the ServiceNow Store
- Sign up for a free HCP Terraform account
- Learn how to use HCP Terraform no-code modules in the ServiceNow Service Catalog with this hands-on tutorial









