We’re excited to announce the release of HashiCorp Terraform 1.4, now immediately available for download and ready for use in HashiCorp Terraform Cloud. Terraform is widely adopted as the standard for multi-cloud provisioning and automation for individuals and teams at any scale. This release introduces improvements for CLI interactions with Terraform Cloud and a new native replacement for the “null” resource.
»Enhanced Terraform Cloud output for CLI-driven runs
One of the many benefits of Terraform Cloud is an enhanced user interface for visualizing and exploring run results. But this structured run output experience has been limited to runs initiated from the UI, version control integrations, or the API. Terraform runs initiated from the CLI continued to display raw console output in the Terraform Cloud UI.
Now, Terraform Cloud runs initiated using Terraform 1.4 can also enjoy this enhanced UI experience. Instead of scrolling through a stream of text, you can quickly see the impact of your changes no matter how the run was started.
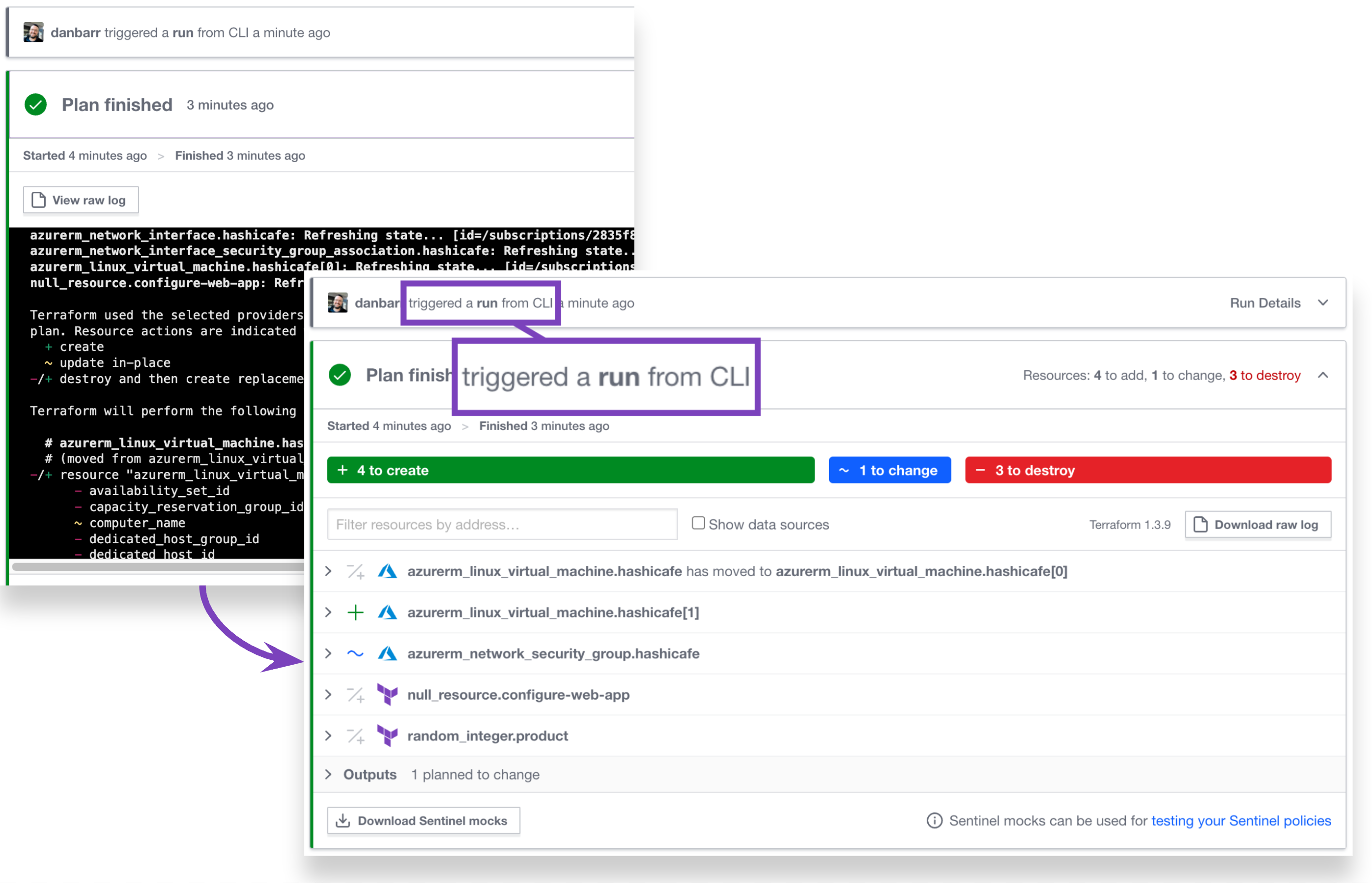
Enhanced output for CLI runs.
»OPA policy results in CLI
Terraform 1.4 also adds support for Open Policy Agent (OPA) results in CLI-driven runs with Terraform Cloud. Native OPA support, now generally available, enhances Terraform Cloud’s policy as code capabilities by integrating the OPA policy engine alongside our own Sentinel policy engine. With Terraform 1.4, CLI-driven runs for workspaces with OPA policies applied now have parity with Sentinel policies. If a policy rule fails and overrides are allowed, interactive runs will include an override prompt as you can see in this screenshot:
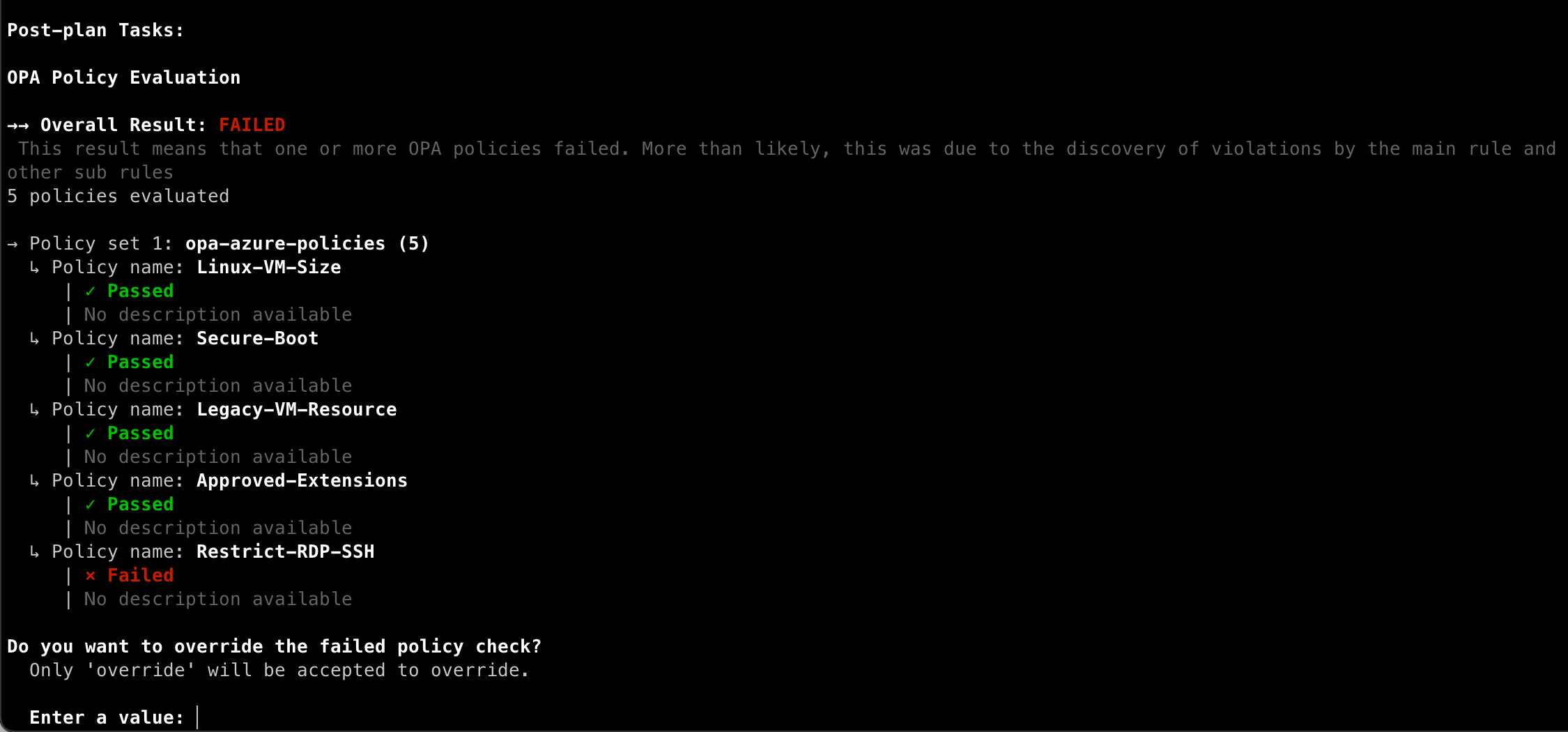
CLI-driven runs now display the results of OPA policy checks.
Learn how to enforce OPA policies in Terraform Cloud with the Detect Infrastructure Drift and Enforce OPA Policies tutorial.
»Native replacement for null_resource
The null utility provider implements a single resource (null_resource) which, as the name implies, does nothing. As strange as that sounds, this is intentional. The null resource is often used to help orchestrate tricky resource lifecycle situations. In fact it’s so widely used, it’s the 3rd most-downloaded provider in the Terraform Registry.
Terraform 1.4 introduces a new terraform_data resource as a built-in replacement for the null resource. This removes the need to include the null provider in your configuration and supports all the same capabilities as null_resource. Here’s an example using terraform_data to trigger the replacement of a resource:
variable "revision" {
default = 1
}
resource "terraform_data" "replacement" {
input = var.revision
}
# This resource has no convenient attribute which forces replacement,
# but can now be replaced by any change to the revision variable value.
resource "example_database" "test" {
lifecycle {
replace_triggered_by = [terraform_data.replacement]
}
}
You can learn more about the new terraform_data resource including its syntax and usage examples in the Terraform language docs.
»Getting started with Terraform 1.4
For more details and to learn about all of the enhancements in Terraform 1.4, please see the full HashiCorp Terraform 1.4 changelog.
- Download the Terraform 1.4 release
- Sign up for a free Terraform Cloud account
- Review the Terraform 1.4 upgrade guide
- Get hands-on with tutorials at HashiCorp Developer
As always, this release wouldn't have been possible without all of the great community feedback we've received via GitHub issues and from our customers. Thank you!








