The last few months have been an exciting time for HashiCorp Terraform Enterprise. Recent releases have brought new features to enhance all aspects of your infrastructure provisioning workflow, including improved manageability, security, governance, and visibility.
Let’s recap some of the major improvements:
»Fresh new user interface
The first thing you’ll notice in v202301-1 is that the user interface in Terraform Enterprise has received a makeover. The new design aligns with the Terraform Cloud UI and is based on our newly open sourced Helios design system.
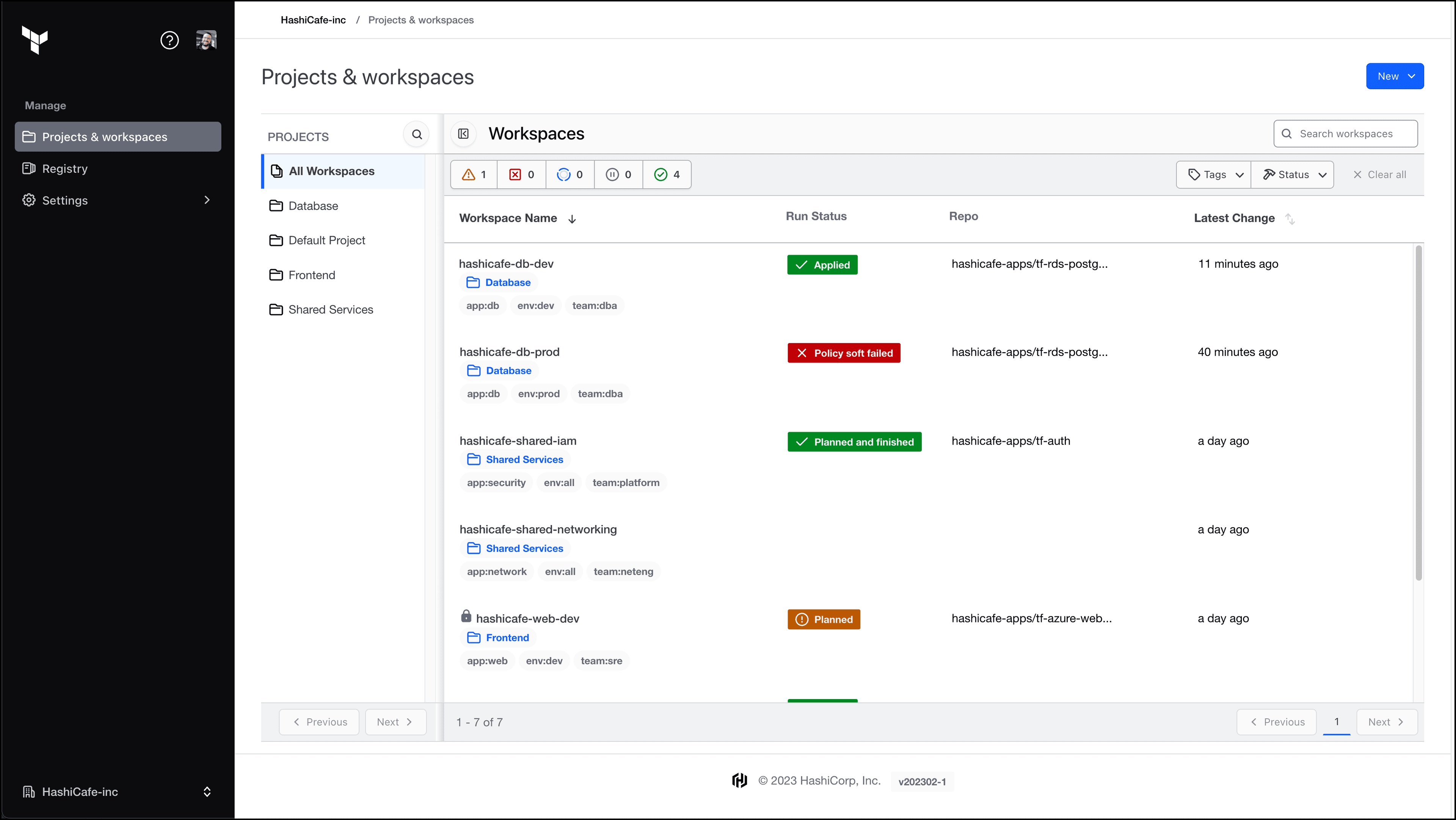
The redesigned user interface in Terraform Enterprise.
»Cross-organization provider sharing
As of v202301-1, you can now share providers in your private registries across organizations in a Terraform Enterprise installation, just like you can for modules. This eliminates the manual effort previously required to repeatedly publish providers in each organization.
»Terraform projects
Available in v202302-1, a new abstraction layer known as projects allows you to organize and manage groups of related workspaces within Terraform Enterprise organizations. Projects allow organization admins to create logical ownership boundaries and enable teams to safely self-manage their workspaces with project-level permissions. This cuts down the toil of applying workspace permissions and also reduces the need to split your instance into multiple organizations.
Check out a demo of Terraform Projects and learn more in the documentation.
»GitHub App authentication
Also added in v202302-1, GitHub App authentication provides an enhanced integration between Terraform Enterprise and GitHub.com or GitHub Enterprise. Unlike OAuth-based authentication, which uses a single highly privileged service account, the GitHub App operates under its own identity while also applying the permissions of individual users when interacting with repositories. This greatly improves the security posture of your Terraform Enterprise interactions with GitHub and provides improved auditability. As of v202303-1, VCS-driven workspaces connected via GitHub App can also be managed via the API or an upcoming release of the tfe provider.
Demo of configuring GitHub App integration with Terraform Enterprise.
»Improved run pipeline
In version v202302-1 we introduced an improved run pipeline model known as tfe-task-worker, which is based on the tfc-agent runtime. If you are using custom worker images in your Terraform Enterprise installation, please review the migration guide to learn how to transition to custom agent images.
This change enables Terraform Enterprise to deliver highly anticipated features such as native OPA support, dynamic provider credentials, and drift detection. It also improves run queueing and distribution across nodes in an active/active deployment.
»Native Open Policy Agent support
Enforcing policies and security guardrails is a critical aspect of standardizing your infrastructure automation across an organization. HashiCorp Sentinel is a powerful policy as code framework that has been part of Terraform Enterprise since its inception. Now, as of version 202303-1, you can also choose to enforce policies using the Open Policy Agent (OPA). OPA and Sentinel can operate side-by-side so teams can choose their preferred framework and work together seamlessly. For more information see our announcement of general availability of native OPA support in Terraform Cloud and the OPA policies section of the Terraform Enterprise docs.
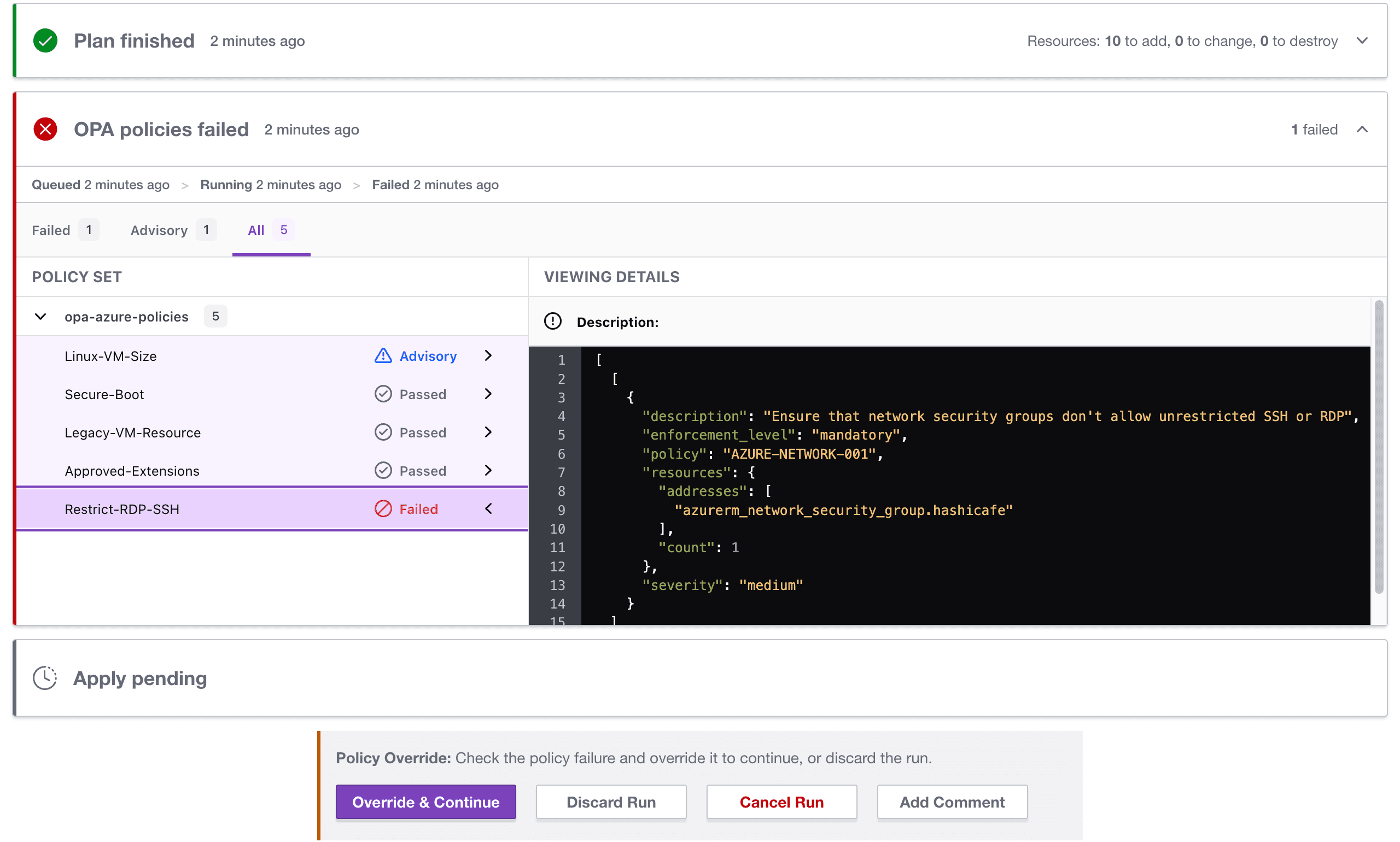
Review OPA policy results natively in Terraform Enterprise.
»Dynamic provider credentials
Now generally available in Terraform Cloud, dynamic provider credentials are also available for Terraform Enterprise in the v202303-1 release. This new authentication model leverages the industry standard workload identity process with OpenID Connect (OIDC) to generate short-lived cloud credentials for your Terraform runs, eliminating the risks inherent with static long-lived credentials. Dynamic provider credentials in Terraform Enterprise natively integrates with the HashiCorp Vault, Amazon Web Services (AWS), Microsoft Azure, and Google Cloud providers to help ensure that each Terraform run receives only the permissions it needs. Learn more by visiting the dynamic provider credentials documentation and tutorials.
»Drift detection
Another highly anticipated feature enabled by the new run pipeline is drift detection, now available in Terraform Enterprise v202303-1. Once your infrastructure is provisioned, how do you know if something has changed outside the Terraform workflow? Drift detection provides built-in continuous checks against infrastructure state to detect these changes, with customizable notifications to alert operators. Enabling drift detection is as easy as turning on the health assessments feature in your workspace settings.
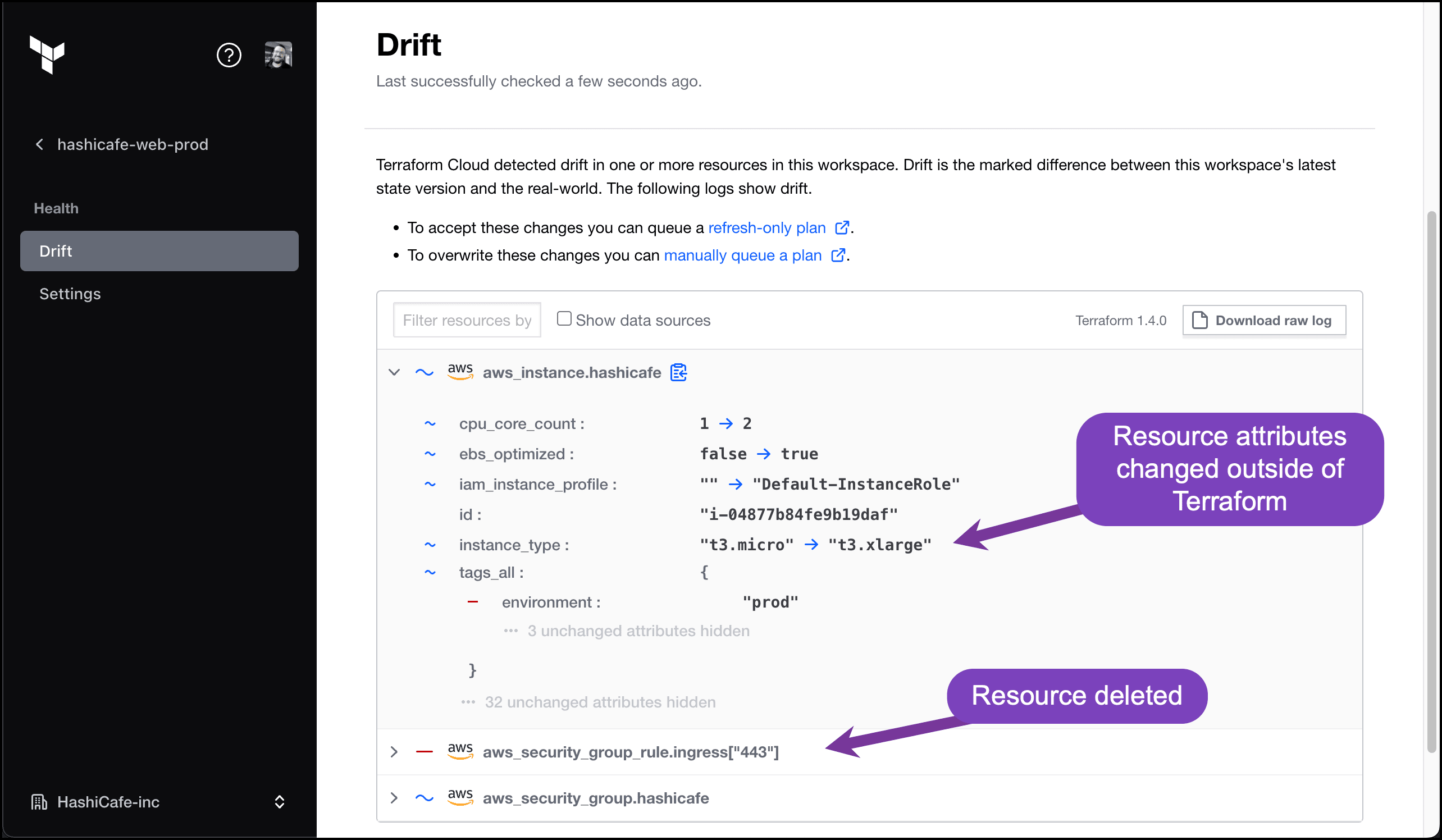
Drift detection identifies resources changed outside of Terraform.
»Next steps
For more information about the latest releases of Terraform Enterprise, see the release notes on the Terraform Enterprise releases page. For more details on Terraform Enterprise or to get started, visit the Terraform product page or contact HashiCorp Sales.








