Strengthen security and governance
Reduce cloud infrastructure risk with an identity-first security approach. HashiCorp delivers lifecycle-driven security from Day 0.
A data breach can cost you $4.44M
Cloud infrastructure has unlocked speed and scale, but it also brings new security risks. Ephemeral environments and distributed teams make it harder to maintain control. And when security is added after deployment, visibility and compliance suffer. To stay ahead of threats, enterprises need built-in security that’s automated, scalable, and built with zero trust principles.
81%
of enterprises use multiple cloud providers, complicating infrastructure management
98%
of companies have experienced at least one cloud-related security incident
75%
of companies faced security breaches from cloud misconfigurations
Reduce cloud risk by strengthening security and governance
The Infrastructure Cloud helps organizations strengthen security and governance by embedding identity-based access controls, secrets management, policy as code, and automation into every stage of the infrastructure lifecycle.
3 ways to strengthen security and governance
Avoid becoming the next data breach headline — without compromising speed or increasing costs. HashiCorp helps leading companies around the world strengthen security and governance by focusing on three interconnected pillars.
Proactive risk management
Stop security incidents before they happen by reducing manual processes, enforcing policy at scale, continuously validating security, and streamlining remediation throughout the infrastructure lifecycle.
- Centralized visibility and controlReduce risk across hybrid and multi-cloud environments with a unified control plane that acts as your single system of record, and infrastructure that’s secure by default.
- Continuous security validationAutomatically scan code repositories and monitor privileged access sessions and service registries.
- Vulnerability and patch managementIdentify, prioritize, and mitigate vulnerabilities through automated workflows built into your CI/CD pipelines.
- Drift detection and alertsContinuously monitor infrastructure for changes against its expected state to eliminate insecure or non-compliant infrastructure.
Enhanced compliance posture
Maintain audit readiness across hybrid cloud environments with automated policy enforcement, continuous monitoring, golden image deployment pipelines, and holistic secrets governance.
- Compliance workflows and regulatory readinessEnhance governance with automatic policy enforcement, drift detection, and automated audit logging.
- Holistic secrets managementAdopt end-to-end holistic secrets management, including dynamic secrets that are generated, rotated, and revoked automatically.
- Compliant modules by defaultShift compliance left with prebuilt images, modules, and registries that are secure and compliant by default.
- User compliance monitoringActively monitor users and sessions to ensure compliance and terminate access when improper or suspicious activity is detected.
Advanced zero trust cloud practices
Enforce dynamic, identity-based access for both human and non-human identities. Minimize standing access, authenticate every request, log every action, and protect sensitive data across all environments
- Secure human accessAuthenticate and authorize users while ensuring least-privileged and time-bound access to sensitive systems.
- Machine identity and trustExtend identity-based security to machine-to-machine access requests.
- Secure application and service networkingDiscover, schedule, and securely connect any service across any runtime with identity-based service networking.
- Data lifecycle managementSecure the entire lifecycle of your most important data with dynamic keys, certificates, encryption as a service, and automated secrets discovery and remediation.
How leading organizations are strengthening security and governance
How ILM and SLM work together to strengthen security and governance
To truly reduce cloud infrastructure risk, security can’t be layered on after deployment — it needs to move in lockstep with infrastructure. That’s where Infrastructure Lifecycle Management (ILM) and Security Lifecycle Management (SLM) come together.

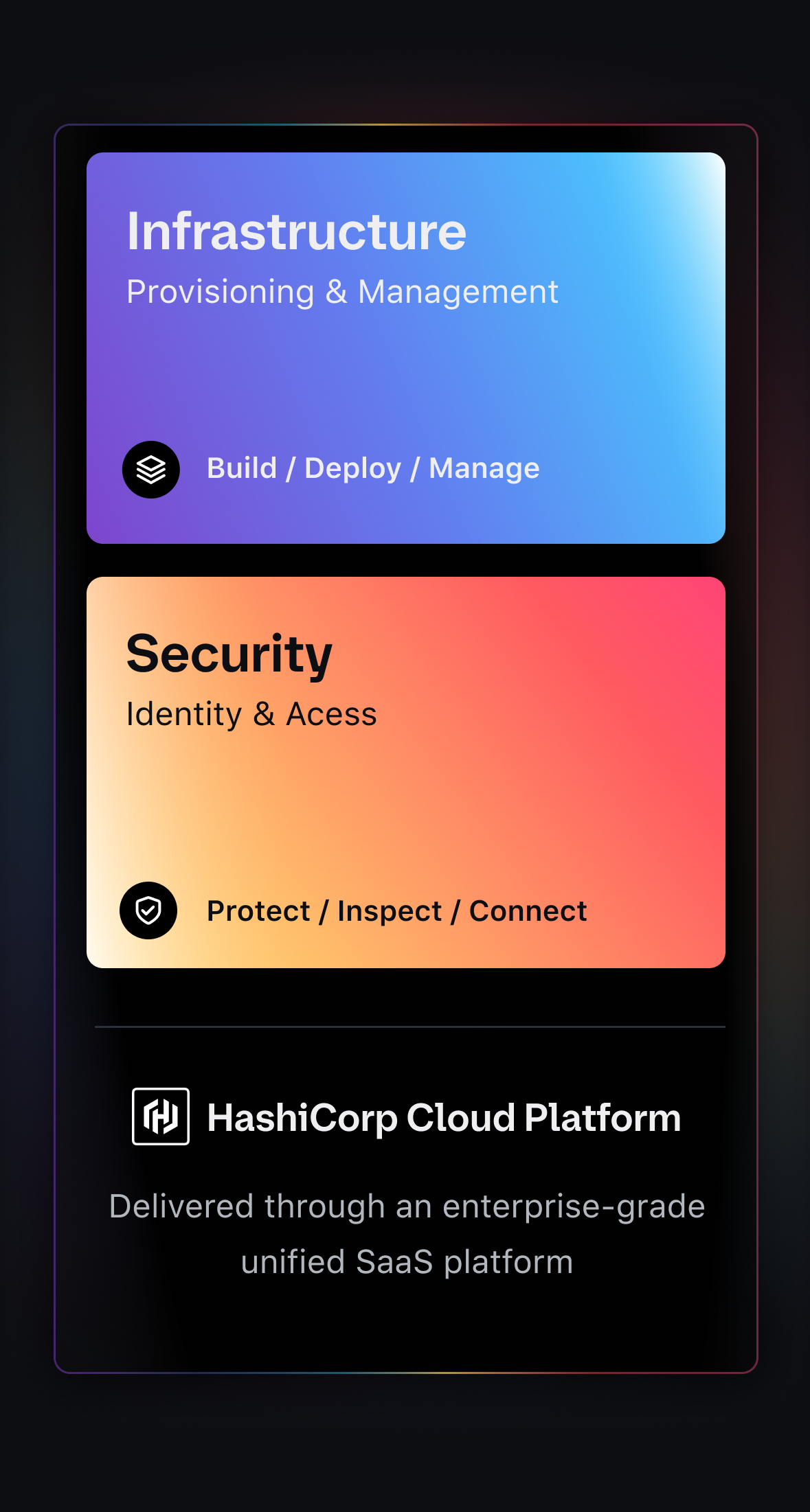
Infrastructure Lifecycle Management
With ILM, infrastructure is consistently built, deployed, and managed using automation and policy as code, removing manual steps and human error from the equation.
Security Lifecycle Management
SLM inspects, protects, and governs sensitive elements of your cloud infrastructure at every stage, so secrets, access, and service communication stay protected as the infrastructure evolves.
More ways to strengthen security and governance
Zero trust identity management for the AI era
Download the KuppingerCole report to learn how HashiCorp brings least-privilege, identity-based access and policy controls to non-human identity management across hybrid and multi-cloud environments.

Secure and scale from Day 1
Modern cloud demands proactive security. This white paper shows how The Infrastructure Cloud unifies Infrastructure and Security Lifecycle Management to reduce risk, prove compliance in real time, and accelerate delivery.

Security Lifecycle Management with the HashiCorp Cloud Platform
Download your guide to nine essential steps for maturing SLM practices across your organization, scaling security, and shrinking your attack surface with the HashiCorp Cloud Platform (HCP).

Unified identity, simplified security
Discover how HashiCorp and IBM are transforming identity management with an "identity fabric" — a unified approach that bridges human and machine identities to enhance visibility, governance, and security across your entire landscape.
It’s time to do cloud security right
Get started strengthening security and governance across your hybrid cloud infrastructure "with a $500 trial credit for the HashiCorp Cloud Platform (HCP).




