HashiCorp Consul is a global service networking platform that provides multi-runtime service discovery and secure services networking. It is widely adopted and used in production by organizations such as Expedia and Workday. The latest release, version 1.22, includes a broad range of enhancements across different parts of Consul, including:
- A new MCP server that simplifies how users interact with Consul.
- USGv6 compliance
- Improved single-sign-on (SSO) security with private key JWT.
- Stronger security with snapshots to Azure
- More metrics for ESM telemetry
»Consul MCP server
In case you missed it, the Consul MCP server was released on September 25 at HashiConf and is available for all Consul users. The Consul MCP server will revolutionize how users interact with and manage their Consul environments.
By providing a conversational, AI-driven interface, the Consul MCP server will help users manage services, health checks, configuration, and service mesh operations through natural language. This means less time grappling with complex commands and more time focusing on what truly matters — ensuring your services are healthy, secure, and performant. For example, a platform engineer can ask, “Investigate why service-hello in dc1 is unable to communicate with service-response in dc2?”
The Consul MCP server can also help improve security within the Consul cluster. Rather than locating the different Consul CLI commands or APIs to check over-privileged access, platform and security teams can quickly check for security threats, over-privileged ACL tokens, over-permissive service intentions, and over-permissive access to Consul resources using simple human prompts. For example: “Is the token with id <Accessor ID> appropriate for kv read-only operations? Suggest remediation with best practices."
The Consul MCP server is being developed as a standalone Go application, leveraging the open standard for connecting AI agents to external tools and data sources. The initial release provides a production-ready MCP server with a comprehensive read-only API for Consul. It can connect to popular MCP clients like VS Code, Claude Desktop, and Cursor.
This foundational work will also establish a robust platform for future enhancements, including write operations, advanced workflow automation, and support for standalone and federated Consul cluster deployments. This new capability will reduce operational complexity and simplify the user experience, making Consul even more accessible and powerful for managing dynamic, distributed applications.
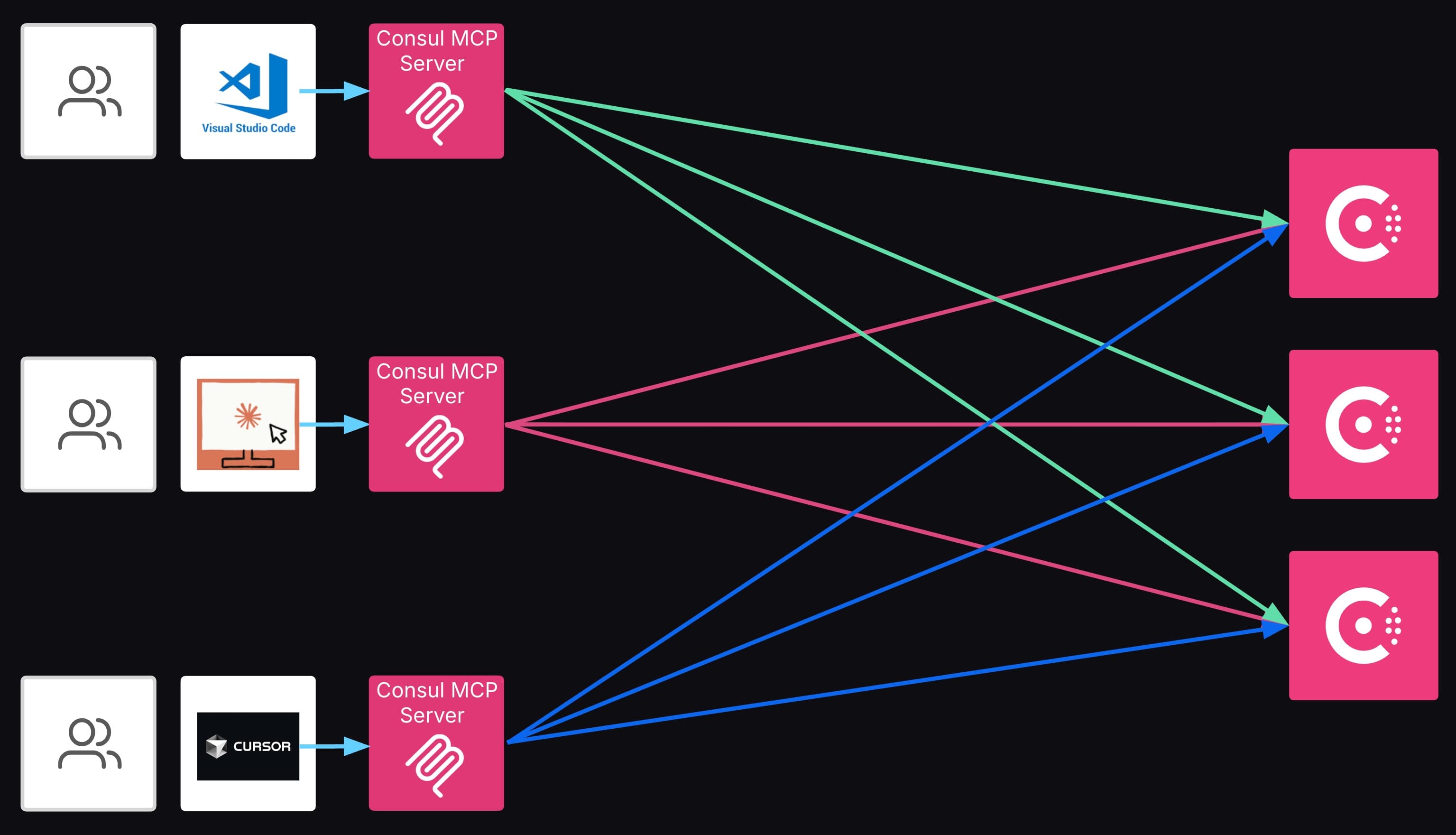
The Consul MCP server can be connected to MCP clients like VS Code, Claude Desktop, and Cursor.
»USGv6 compliance
Since its introduction in the early 1980s, IPv4 has powered the internet as we know it. But with the rapid growth of connected devices, the limitations of IPv4 became clear. To address this, the federal government launched an initiative to accelerate the adoption of IPv6 — the next-generation Internet protocol designed to replace IPv4.
Today, IPv6 adoption isn’t just a best practice; it’s a mandate for U.S. federal agencies. The Office of Management and Budget (OMB) memorandum M-21-07 requires all federal agencies to transition toward IPv6-only environments, setting aggressive milestones along the way. By the end of fiscal year 2024, 50% of IP-enabled assets across federal networks must operate exclusively on IPv6. Any remaining non-compliant assets can request exemptions but must have a schedule to be replaced or retired.
To meet these requirements of our federal customers, Consul 1.22 is now fully compliant with USGv6. Consul agents and mesh components have been enhanced to support IPv6 binding, registration, discovery, and routing. Consul logs and metrics also reflect IPv6 traffic, enabling full operational visibility in IPv6-only environments. As a result, both service discovery and service mesh capabilities within Consul will now be able to run in IPv6-only environments.
»Tighter security Consul private-key JWT
As organizations face heightened security and compliance demands, authentication methods need to evolve. Consul supports OpenID Connect (OIDC), which allows users to authenticate into Consul using SSO through integrations with external identity providers like Okta, Ping, and IBM Verify. However, prior to this release, Consul’s OIDC integration primarily relies on the client_secret method — a shared secret passed between Consul and the identity provider. While functional, many organizations require a more secure method that reduces the risk of exposing secrets.
To address this, Consul is enhancing its OIDC authentication by adding support for private_key_jwt. This aligns with modern security standards like FAPI and OAuth 2.1, offering stronger protection against credential theft and authorization code interception. As a result of this enhancement, security engineers gain confidence that authentication events are cryptographically verifiable and free of static secrets. Platform engineers can now simplify credential management by removing the need to rotate client secrets, and developers can seamlessly authenticate to Consul using existing corporate SSO solutions.
»Consul snapshots on Azure with managed Azure identities
Consul has the capability to take snapshots of a cluster’s current state, which can be used to backup and restore failed clusters in the event of a disaster. Using the Consul snapshot agent, snapshots can be stored locally or to various cloud storage destinations, including AWS S3, Google Cloud Storage, and Azure Blob Storage. Previously, configuring the Consul snapshot agent to back up snapshots to Azure Blob Storage meant storing sensitive credentials — either account_key or a combination of a service principal ID, secret, and tenant ID — directly in configuration files, which is a concern if not properly managed and secured. Furthermore, these secrets needed to be rotated properly, which increased operational overhead for platform engineers.
In Consul 1.22, these issues are addressed with the use of Azure Managed Identities, which eliminate these static secrets and simplify the overall configuration and management of the backup process. Instead, the Consul snapshot agent configuration file will accept a new AuthType field, which is used to select the Azure Managed Identity option.
Here is an example snippet in the Consul snapshot agent configuration file:
"backup_destinations": {
"azure_blob_storage": [
{
"account_name": "my-storage-account",
"container_name": "consul-snapshots",
"auth_type": "msi" }
]
}
With Consul 1.22, security engineers can audit snapshot configurations and quickly confirm that no static credentials are in use, helping teams meet compliance and least-privilege standards. Platform engineers reduce maintenance without the burden of secret rotation. And lastly, backups become more reliable and consistent.
»Consul ESM telemetry improvements
Consul ESM is a software component that is responsible for monitoring and performing health checks on external services where Consul agents are prohibited from being installed. Examples of external services include third party SaaS services like Amazon RDS or Azure Databases, legacy services that do not permit installing third-party software, or services managed by other teams, where you do not have access to the underlying node.
While Consul ESM provides visibility into the health of external services, ironically, there is little insight that Consul operators have on the health of the Consul ESM node cluster itself. As a result, operators and platform engineers are not able to proactively detect and respond to issues in a timely manner.
In this release, Consul ESM offers more telemetry data that improves observability. The new metrics include:
- Leadership status and changes between ESM nodes
- Leadership election events
- ESM agent health status
- Number of healthy and unhealthy checks
These metrics are compatible with common observability tools like Prometheus and StatsD. With this enhancement, platform engineers have actionable insights into the ESM cluster nodes, which help improve overall operational reliability and response time.
»Learn more about Consul 1.22
Get started with HashiCorp Consul through our many tutorials for both beginners and advanced users. You can start a free trial with Consul Enterprise to test out commercial features. More detailed information is available in the newly improved Consul documentation.









