As of February 2022, Centrify is now Delinea. The following is a guest blog from David McNeely, Vice President of Product Strategy at Delinea.
Delinea enables organizations to adopt a Zero Trust Security model through the power of Next-Gen Access controls for both applications and infrastructure. Delinea uniquely converges Identity-as-a-Service (IDaaS), enterprise mobility management (EMM) and privileged access management (PAM) in order to enforce Zero Trust Security, verifying every user, validating their device, and limiting access and privileges to proactively secure your organization.
Today, Delinea is proud to announce the integration of the Delinea Identity Service with HashiCorp Vault for role-based user authentication and access to the Vault.
The Delinea Next-Gen Access Management platform now provides an additional Auth Method called "centrify" for HashiCorp Vault. This Auth Method allows you to authenticate users to HashiCorp Vault, leverage any connected directory source for authentication, and enable role-based authorizations to Vault resources using Delinea Roles.
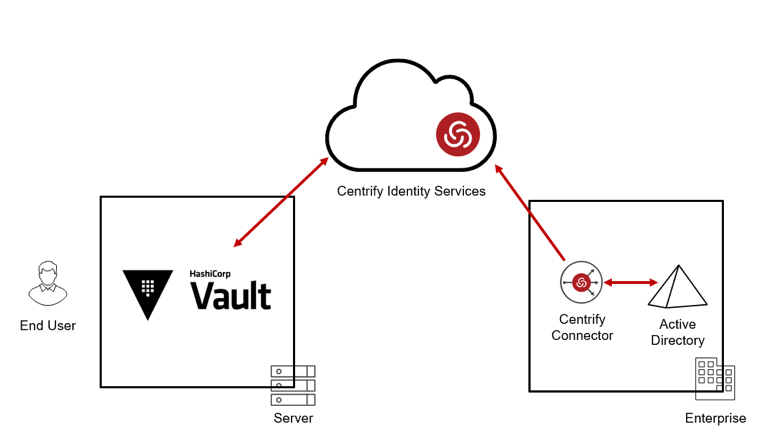
Figure 1: HashiCorp Vault integration with Delinea Identity Services
There are several benefits to using Delinea for user authentication to HashiCorp Vault:
- Delinea brokers authentication to any connected directory source, including Active Directory, LDAP, Google Directory, or the Delinea Cloud Directory for user or service accounts.
- User access to the Vault is time-bound and is based on authentication to the Delinea Identity Service. This allows you to avoid long-lived credentials left behind on user's machines and protects against potential malware attacks.
- Delinea's integration enables workflow-based access control, allowing users to request and receive access to the Vault only when needed. This enables you to grant access to the Vault without assigning permanent access rights within the Delinea Identity Service.
- Delinea integration centralizes access management for new users and temporary workers. You can simplify account creation during the on-boarding process and automatically disable user access upon termination.
- Delinea captures an audit log of all user login events to the HashiCorp Vault and sends these logs to your security information and event management (SIEM) solution for analysis.
- With Delinea, you can authenticate your on-premises users to the Vault deployed on-premises, in a DMZ, within one or more VPCs on Amazon AWS, or in other IaaS hosting services.
Delinea can also simplify the integration with Active Directory for those deployments where Vault runs on Linux and has direct Active Directory access. In this model, Delinea extends Vault's current LDAP Auth Method to support proper operations within complex multi-domain or one-way trust Active Directory (AD) environments through the Delinea LDAP Proxy. Additionally, Delinea Agent for Linux provides centralized public key infrastructure (PKI) certificate management for Linux within environments which use Microsoft Certificate Authority for automated certificate issuance and renewal.
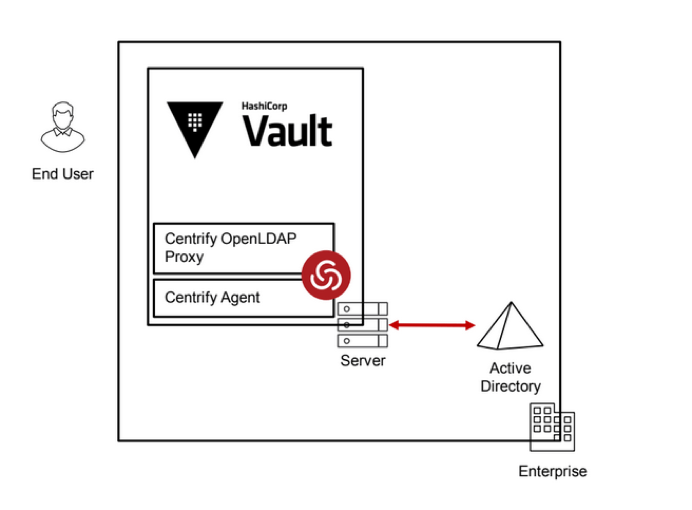
Figure 2: HashiCorp Vault integration with Delinea Agent for Active Directory
Regardless of how you would like to centralize user authentication to Vault, Delinea provides a solution to integrate Vault into Active Directory, LDAP, Google Directory or Delinea Cloud Directory as well as provide role-based authorization to Vault resources.
»About David McNeely
David McNeely is vice president of product strategy at Delinea, where he works with customers to drive the product strategy and roadmap for Delinea's award-winning Privileged Access Management and Identity-as-a-Service offerings. McNeely has worked in the identity and access management market for over 20 years, holding various product management positions at ActiveIdentity, AOL and Netscape. At Netscape he was the director of product management for the Directory and Security product line, where he first promoted the concept of a centralized enterprise directory for unified identity and access management.
»About Delinea
Delinea delivers Zero Trust Security through the power of Next-Gen Access. The Delinea Zero Trust Security model assumes that users inside a network are no more trustworthy than those outside the network. Delinea verifies every user, validates their devices, and limits access and privilege. Delinea also utilizes machine learning to discover risky user behavior and apply conditional access — without impacting user experience. Delinea's Next-Gen Access is the only industry-recognized solution that uniquely converges Identity-as-a-Service (IDaaS), enterprise mobility management (EMM) and privileged access management (PAM). Over 5,000 worldwide organizations, including over half the Fortune 100, trust Delinea to proactively secure their businesses.
»Learn More
To learn more about Delinea Identity Services, visit Delinea at https://delinea.com/. You can view technical documentation on GitHub at https://github.com/hashicorp/vault-plugin-auth-centrify








