Today at HashiDays, we are excited to announce new capabilities for HashiCorp Terraform Cloud, making it easier to import, view, validate, and manage resources across your entire infrastructure.
The announcements include:
- Explorer for workspace visibility (beta)
- Ephemeral workspaces (coming soon)
- Config-driven import (GA)
- Continuous validation with Terraform checks (GA)
»Terraform is designed to secure infrastructure
According to the 2023 State of Cloud Strategy Survey, commissioned by HashiCorp and conducted by Forrester Consulting, security initiatives are critical cloud strategy drivers, and 88% of respondents see security as a key factor in cloud success. Meanwhile, 92% of respondents see multi-cloud as helping to achieve or expected to achieve their organization’s business goals.
So how can customers manage multiple environments without increased risks and complexity? Terraform is a key part of the solution.
Earlier this year, HashiCorp released dynamic provider credentials for secure, short-lived authentication, giving platform teams a way to securely authenticate to Terraform providers. Dynamic provider credentials use just-in-time (JIT) access to reduce the risk and complexity associated with storing long-lived static credentials in Terraform.
In April, Terraform added Vault-backed dynamic credentials, which combine dynamic provider credentials with Vault secrets engines to offer a consolidated workflow. This approach authenticates Terraform runs to Vault using workload identity tokens generated by Terraform Cloud, then uses Vault secrets engines to generate dynamic credentials for the Amazon Web Services (AWS), Microsoft Azure, and Google Cloud providers. This authentication method is a significant enhancement for customers already using Vault for on-demand cloud access and for any organization seeking to reduce the risks of managing credentials.
Today's announcements further bolster secure infrastructure provisioning and management from Terraform.
»Explorer provides workspace visibility across all infrastructure
When organizations scale their cloud environments and DevOps teams with multiple technologies and tools, it can become difficult to keep the software — including module, provider, and Terraform versions — up to date across teams. This can lead to teams using deprecated or revoked versions, which poses a security risk. What teams need is a way to view the versions of those Terraform components across all workspaces to see which workspaces might be falling behind.
Explorer for Terraform Cloud provides a consolidated view of workspace data across your organization, including information on providers, modules, Terraform versions, and health checks from drift detection and continuous validation. This consolidated view helps teams ensure their environments have the necessary up-to-date versions for Terraform, modules, and providers, while tracking health checks ensures security, reliability, and compliance.
Using explorer, platform teams can determine which versions to remediate when vulnerabilities or misconfigurations are discovered. They can then notify the appropriate workspace owners to upgrade by identifying all workspaces utilizing a specific version. Manually building a report with all of this data could take weeks, but with explorer it can be done in minutes.
Explorer provides a consolidated view of all your Terraform Cloud workspace data.
»Ephemeral workspaces remove unused resources
Unused or forgotten infrastructure constitutes a runaway cost for many organizations. These costs can be mitigated if administrators have effective methods to enforce time-to-live policies for infrastructure resources.
Terraform Cloud’s upcoming ephemeral workspaces will allow customers to set timeouts that automatically destroy temporary resources. For administrators, this should eliminate a large amount of manual clean-up, reduce infrastructure costs, and further simplify workspace management and testing.
Ephemeral workspaces work with existing workspace permissions and have a simple workflow. Just set a date when you would like the workspace to be deprovisioned. Then, once that date is reached, Terraform will automatically run a destroy plan and apply it to destroy your managed resources. A reminder notification will be sent before it starts and after the run is finished to indicate success or failure.
Unused resources also represent more potential attack surfaces for malicious actors. Therefore, removing unused workspaces will be important not just for cost control, but for security as well.
»Config-driven import simplifies migration to Terraform
A unified workflow for all infrastructure reduces risks and alleviates skills gaps that many organizations identify as a common barrier to multi-cloud. While Terraform provides a single workflow for all infrastructure, we understand that not all infrastructure resources are provisioned through Terraform today. Customers need to migrate unmanaged resources (from API, CLI, or web console) into Terraform to reduce costs and improve security. The Terraform import command was a good first step in simplifying migration to Terraform, but resources had to be imported one at a time and the matching resource code had to be created manually. Further, import was not supported for VCS and UI-driven workflows in Terraform Cloud, meaning state and provider credentials had to be exposed to direct access from the developer’s local machine.
Config-driven import — released in Terraform 1.5 and now available in Terraform Cloud — provides a more automated, efficient, and secure way to plan multiple imports with existing VCS, UI, and CLI workflows. It enables bulk imports while Terraform Cloud continues to secure the state and credentials. This reduces risks and eliminates the complexity of coordination across multiple users to prevent conflicting operations that lead to resources being deleted. Another benefit is auto-generated configuration — no more repetition between running a plan, referencing documentation, and updating configurations. For more information read our Terraform 1.5 release blog.
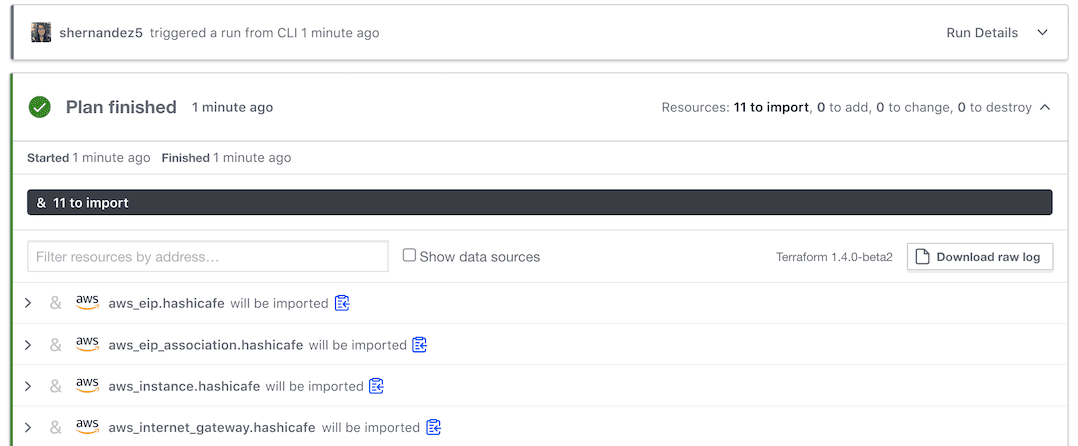
Multiple imports with existing VCS, UI, and CLI-driven workflows
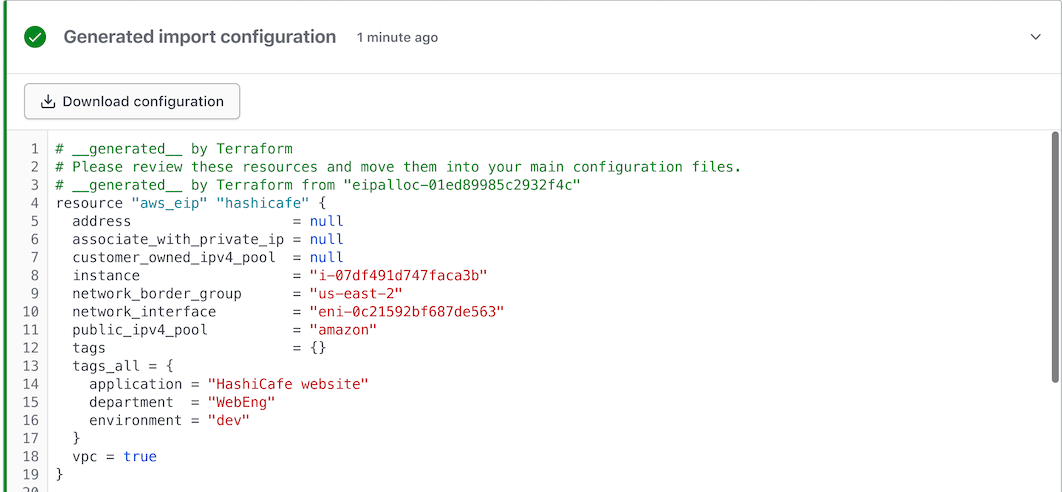
Auto-generated configuration without the need to reference documentation
»Continuous validation ensures infrastructure works as expected
It is challenging and time-consuming to maintain infrastructure health and security, especially when using integrated third-party solutions. Users often need to check multiple dashboards manually and continuously.
To alleviate these challenges in infrastructure tracking and management, we announced the beta version of continuous validation at HashiConf Global 2022. In that beta, continuous validation allowed customers to add custom conditions to Terraform configurations and/or modules. Today, we’ve announced the general availability of continuous validation for Terraform Cloud Plus, which now supports checks — a new feature in Terraform 1.5, which gives customers more flexible options to validate their infrastructure uptime, health, and security — all in one place without requiring additional tools.
Continuous validation sends notifications immediately when things fail, so customers can quickly take action to remedy the situation. For example, by using Terraform checks to continuously validate certification expiration dates, platform administrators can avoid downtime caused by expired certificates. Other use cases include evaluating the status of resources and checking if an app is returning an expected result or if a monitoring metric is exceeding a threshold.
Terraform checks also present new opportunities for provider authors to expose additional data to help users perform functional validation. Here are a few examples of how customers can use continuous validation with the leading cloud and technology partners:
- AWS: Ensure your AWS account is within budget and detect threats with detailed findings for AWS accounts. (See: Using Terraform Cloud's continuous validation feature with AWS.)
- Google Cloud: Assert a VM is in a running state, check if a certificate will expire within a certain timeframe, and validate the status of a cloud function. (See: Using Terraform Cloud's continuous validation feature with Google Cloud.)
- Azure: Assert if a VM is in a running state, monitor if a Container App certificate will expire within a certain timeframe, and check if an App Service Function or Web App has exceeded its usage limit. (See: Using Terraform Cloud's continuous validation feature with Azure.)
- New Relic: Assert the configuration or status of your New Relic notification destination and validate the age of a New Relic secure credential. (See: New Relic Terraform Provider: Continuous Validation with Terraform Cloud)
Continuous validation checks if configs or modules with assertions have passed/failed.
»Try Terraform Cloud today
Terraform is the industry standard for provisioning and managing any infrastructure. It offers a way to standardize infrastructure automation for any resource and provides a shared provisioning service within organizations. With new features such as continuous validation, explorer, and config-driven import (available today and coming soon to Terraform Enterprise) alongside upcoming ephemeral workspaces, platform teams can better leverage Terraform to gain efficiency, reduce risks, and optimize costs. Try these new features today — and if you are new to Terraform, sign up for Terraform Cloud and get started using the Free offering today.








