AWS re:Inforce is in full swing this week in Anaheim, California. HashiCorp once again has a major presence at the event, with breakout sessions, expert talks, and product demos.
HashiCorp is Amazon Web Services’ Security Partner of the Year in North America, validating HashiCorp's vision for delivering zero trust security to cloud infrastructure. The Security Partner of the Year award recognizes top partners with the AWS Security Competency and affirms HashiCorp as a partner that has proven customer success stories securing every stage of cloud adoption, from initial migration through ongoing day-to-day management.

The AWS re:Inforce security conference also offers an opportunity to reflect on our project collaborations with AWS and the state of HashiCorp security initiatives with AWS. That includes new integrations announced today with AWS to help customers sync secrets across AWS and Kubernetes, leverage dynamic credentials, and manage secure user access across any environment.
»HashiCorp and AWS security
HashiCorp Vault provides the foundation for modern cloud security. Vault was purpose-built in the cloud era to authenticate and access multiple clouds, systems, and endpoints, and to centrally store, access, and deploy secrets (API keys, credentials, etc.). It also provides a simple workflow to encrypt data in flight and at rest.
Vault lets you centrally manage and enforce access to secrets and systems based on trusted sources of application and user identity. With Vault and the HashiCorp model around zero trust security, organizations can manage their transition to AWS while maintaining the level of security they need — one that trusts nothing and authenticates and authorizes everything.
HashiCorp-AWS security developments in the last year include:
- Syncing secrets with Vault and AWS Secrets Manager
- Vault Secrets Operator for Kubernetes integrated with Amazon EKS
- Dynamic credentials with the AWS provider
- Boundary Enterprise integrated with the AWS host catalog
- Run task for AWS IAM Access Analyzer
- Start, run, and scale Kubernetes with EKS and Vault
»Vault Secret Operator for Kubernetes integrated with AWS EKS
HashiCorp’s Vault Secret Operator for Kubernetes is now generally available, supporting new authentication methods and product validations with AWS. With the Vault Secrets Operator for Kubernetes, customers can now natively sync secrets from Vault to Kubernetes clusters. The release of the Vault Secrets Operator includes integration tests with Amazon Elastic Kubernetes Service (EKS), a managed Kubernetes service to run Kubernetes in the AWS cloud and on-premises datacenters.
»Dynamic credentials with the AWS provider
Terraform Cloud's dynamic provider credentials let you establish a trust relationship between Terraform Cloud and AWS. They limit the blast radius of compromised credentials by using unique, short-lived credentials for each Terraform run. Dynamic credentials also give you fine-grained control over the resources that each of your Terraform Cloud projects and workspaces can manage. Terraform Cloud supports dynamic credentials for AWS and Vault.
When you use dynamic credentials, Terraform Cloud begins each run by authenticating with AWS, passing it details about the workload, including your organization and workspace name. Your cloud provider then responds with temporary credentials that Terraform Cloud uses to provision your resources for the run. This workflow is based on the OpenID Connect protocol (OIDC), an open source standard for verifying identity across different systems.
You can use Terraform Cloud’s native OIDC integration with AWS to get dynamic credentials for the AWS provider in your Terraform Cloud runs. Configuring the integration requires the steps outlined in our documentation. To learn more, read the joint AWS and HashiCorp blog post on how to Simplify and Secure Terraform Workflows on AWS with Dynamic Provider Credentials.
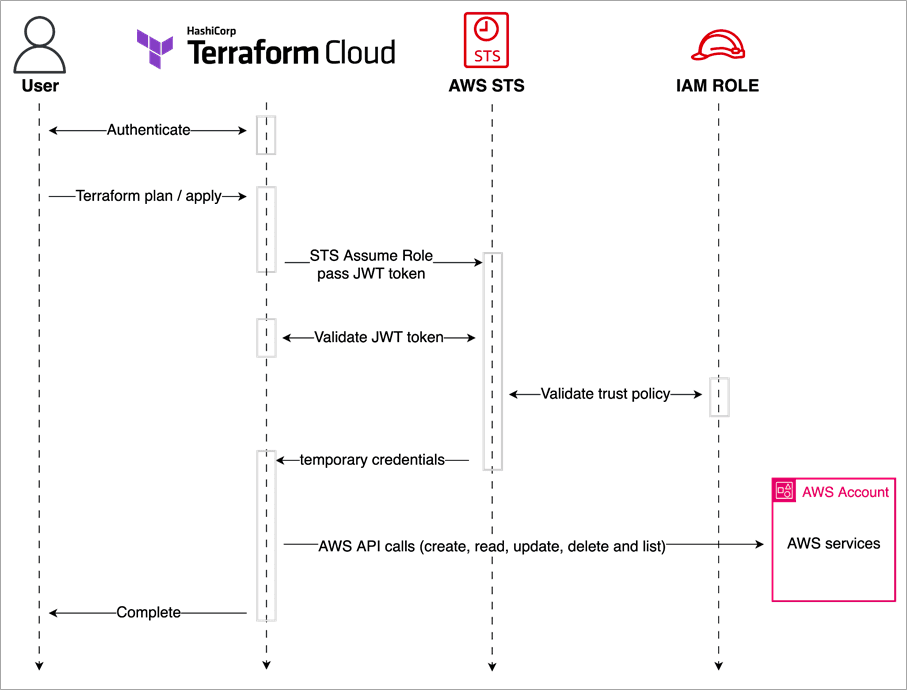
Diagram of Terraform Cloud dynamic provider credentials workflow in AWS
»Boundary Enterprise integrated with AWS host catalog
At last year’s AWS re:Inforce security conference, HashiCorp presented a new way to safeguard who and what has access to applications, systems, and endpoints with the beta release of HCP Boundary. HashiCorp Boundary is a secure remote-access solution that provides an easy way to securely access critical systems with fine-grained authorizations based on trusted identities.
With the announcement of Boundary Enterprise at HashiDays, organizations with strict requirements for where its software can be hosted can now manage remote access with a self-managed deployment of Boundary. Bundled into this release is the latest open source release of Boundary, which includes session recording — a feature that allows organizations to track what actions a user or application takes when accessing infrastructure via a remote-access protocol such as RDP or SSH/TLS. Boundary's session recording launches with AWS S3 as our exclusive storage provider.
Dynamic updates to host catalogs is an important differentiator for Boundary compared to traditional access methods that rely on manual target configuration. This enables even tighter integrations with AWS for seamlessly onboarding cloud tenant identities, roles, and targets. With support for AWS, dynamic connections to any service registry ensures that hosts and host catalogs are consistently up-to-date. This critical workflow offers access-on-demand and eliminates the need to manually configure targets for dynamic, cloud-based infrastructure. To learn more, check out our tutorial demonstrating how to configure Dynamic Host Catalogs on AWS.
»AWS IAM Access Analyzer run task
With AWS Identity and Access Management (IAM), you can specify who or what can access services and resources in AWS, centrally manage fine-grained permissions, and analyze access to refine permissions across AWS. A new AWS IAM Access Analyzer run task has now been published as a Terraform module and an AWS run task in the Terraform Registry.
Start, run, and scale Kubernetes with EKS and Vault
»Start, run, and scale Kubernetes with EKS and Vault
Amazon Elastic Kubernetes Service (EKS) is a managed Kubernetes service to run Kubernetes in the AWS cloud and on-premises datacenters. In the cloud, Amazon EKS automatically manages the availability and scalability of the Kubernetes control plane nodes responsible for scheduling containers, managing application availability, storing cluster data, and other key tasks.
The HashiCorp Vault add-on for EKS deploys a flexible, scalable AWS Cloud environment to Amazon EKS and launches HashiCorp Vault using the HashiCorp Vault Helm chart. To get started, view the HashiCorp Vault on Amazon EKS reference deployment and deployment guide.
The Vault on Amazon EKS add-on has almost one million downloads.
For containerized workloads at the edge using ruggedized hardware, Amazon EKS Anywhere on Snow is now generally available with Vault integrated to manage secrets and protect sensitive data. Additionally, for customers looking to isolate tenant data in the cloud, AWS and HashiCorp have published a proposed architecture for tenant data isolation with dynamic credentials using Vault in Amazon EKS.
»A cloud-managed zero trust security solution
HashiCorp Cloud Platform (HCP) is a fully managed platform available for HashiCorp Terraform, Vault, Consul, Boundary, Waypoint, and Packer. It runs the industry’s first zero trust security solution fully deployed on the cloud by combining HCP Vault, HCP Consul, and HCP Boundary to secure applications, networks, and human access, delivered on AWS.
If you’re attending AWS re:Inforce, please stop by our booth (#659) to chat with our technical experts, take in a product demo, and learn how companies like yours are accelerating their cloud journey with HashiCorp and AWS.








