Blue-green deployments and rolling upgrades (canary tests) allow you to release new software gradually and mitigate the potential blast radius of a failed release. Using this pattern, you can release new software with near-zero downtime.
In the new tutorial, Use Application Load Balancers for Blue-Green and Canary Deployments, you will use a combination of blue-green, canary, and rolling deployments to incrementally promote a new application version via HashiCorp Terraform feature toggles and an AWS application load balancer (ALB).
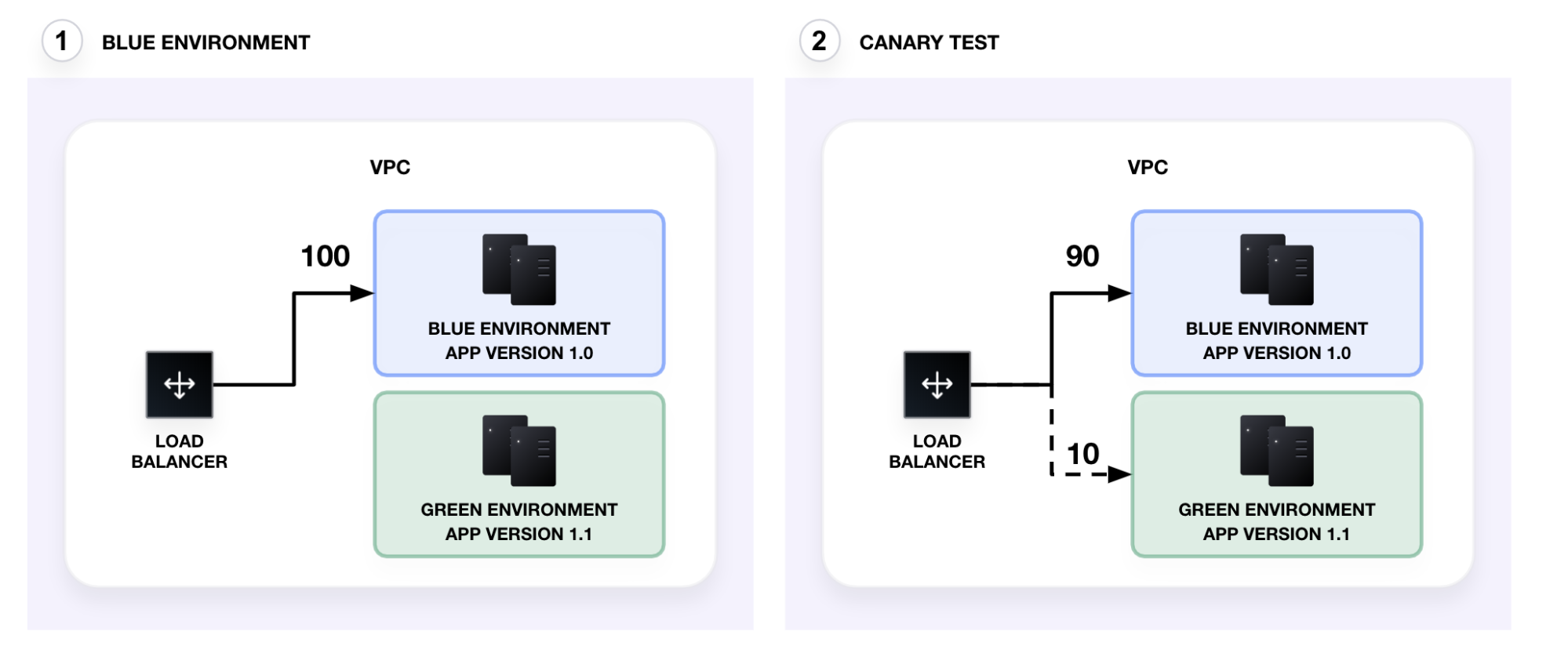
The ALB automatically distributes incoming traffic to the appropriate service at the application layer. ALBs are different from classic load balancers, which only route traffic to EC2 instances across multiple availability zones. You can define an ALB's listeners (rules) and target groups to dynamically route traffic to services. These rules enable you to run canary tests on and incrementally promote the green environment.
»What You’ll Learn
By the end of this tutorial, you will know how to use an application load balancer to incrementally deploy a new application release. In addition, you will have implemented feature toggles to codify and run three advanced deployment techniques in a consistent, reliable manner.








